Over half (52%) of cybersecurity professionals are reporting an increase in cyber-attacks year-over-year, according to new research from ISACA.
Yet, despite this surge, fewer than 1 in 10 organizations conduct cyber risk assessments monthly, and only 40% do so annually.

The reasons? A shortage of skilled personnel, resource constraints, and fragmented processes that fail to embed risk awareness into daily operations.
This isn’t just a cybersecurity issue. It’s an enterprise-wide blind spot.
Because the truth is—Enterprise Risk Assessments are supposed to be your safety net. They’re designed to help you spot threats early, prioritize them properly, and act before damage is done. But for too many organizations, enterprise risk assessments are little more than checklists. Run once a year. Stuck in PDFs. Disconnected from actual business impact.
When the landscape is shifting by the day, you can’t afford to rely on stale risk registers or vague heat maps. You need an assessment approach that’s sharp, dynamic, and rooted in your business reality—not buried in red-yellow-green boxes that no one reads.
In this article, we break down 10 common gaps in enterprise risk assessments—the blind spots that leave companies exposed. More importantly, we show you how to close them. With sharper scoring. Clearer ownership. And a better grip on what risk really means to your business.
Ready to fix the leaks? Let’s go.
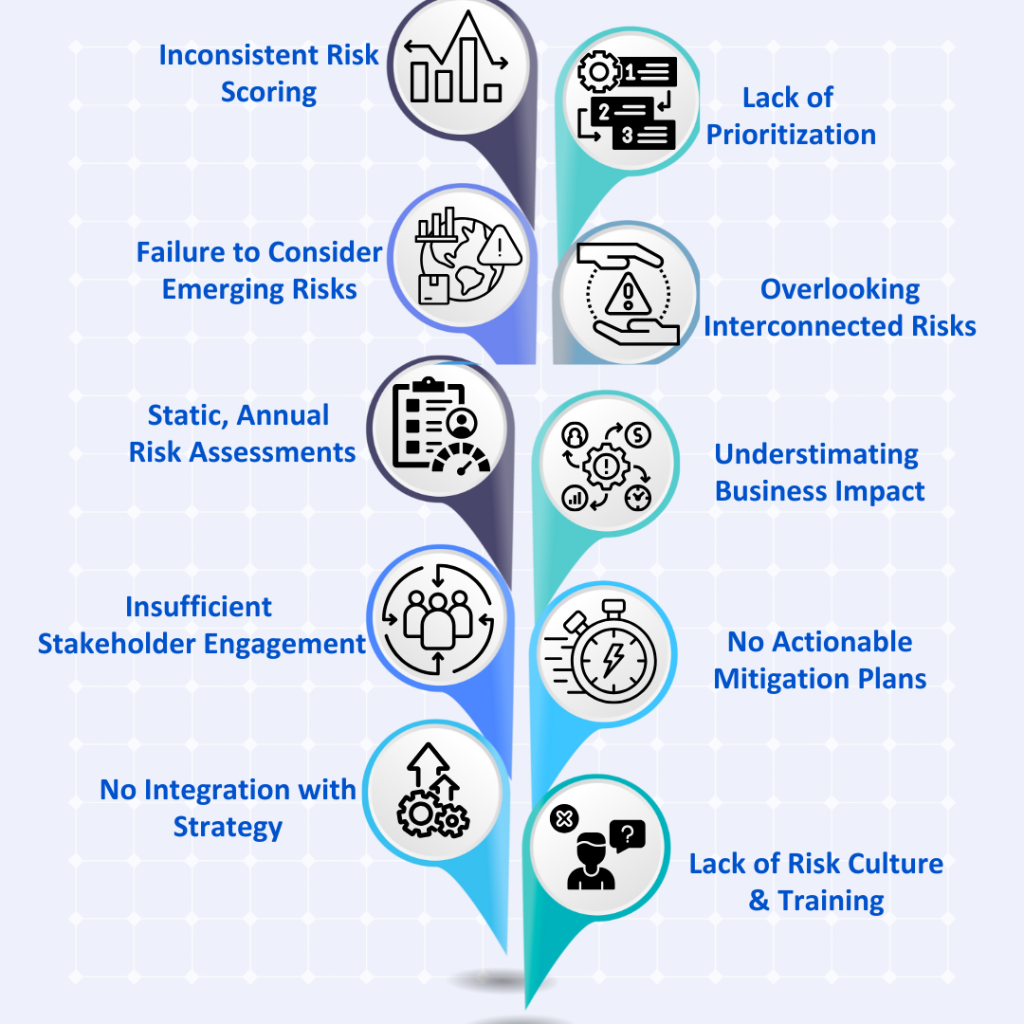
1. Inconsistent Risk Scoring
Let’s start with the basics. If you can’t score risk properly, you can’t manage it properly.
And yet, this is where many risk assessments fall apart. One team ranks a risk as “high” based on gut feel. Another calls the same thing “medium” because it’s happened before and didn’t blow things up. No shared criteria. No consistent math. Just opinions—and a lot of guesswork.
The impact? Confusion. Misalignment. And worse, misplaced focus. Real threats may slip under the radar while less serious ones hog attention (and resources).
How to Close the Gap
Standardize your scoring model. Use a clear, organization-wide framework that measures both likelihood and impact on a fixed scale—typically 1 to 5. That gives you a clean 5×5 matrix to compare risks objectively.
Define what each level means in plain terms. For example:
- Likelihood 4 = “Likely to happen this year”
- Impact 5 = “Causes multi-million dollar loss or major operational outage”
Automate where possible. Pull data from threat intelligence, incident history, and internal audits to reduce bias and add hard numbers to the conversation.
And here’s the kicker: make it usable. If your scoring model takes a 10-minute meeting to explain, no one’s going to follow it. Simplicity wins.
2. Lack of Prioritization
Here’s the trap: you log the risks, you tag the vulnerabilities, you build the list. But somehow… everything feels urgent. And when everything’s urgent, nothing gets done.
Risk registers grow. Action stalls. And the business keeps flying blind.
The problem? Most teams confuse activity with impact. They’re chasing alerts, not prioritizing what actually matters. Which means serious, high-impact threats often get buried under noise.
How to Close the Gap
Start with a mindset shift: Prioritization isn’t about the loudest alert—it’s about the biggest impact.
It’s not enough to rank risks based on abstract scores or static categories. You need contextual signals—the kind that tell you why a risk matters and how it could hurt the business. Go beyond CVSS scores or severity tags. Ask sharper questions:
- Is this vulnerability exposed externally or buried deep inside the network?
- Does it involve sensitive data, like PII or financials?
- Is the system it touches business-critical—customer-facing, revenue-driving, or core to operations?
- Are there any safeguards already in place (like firewalls, EDR, segmentation)?
- What would happen if this went wrong today?
These aren’t just technical questions—they’re business ones. And the answers will help you separate signal from noise.
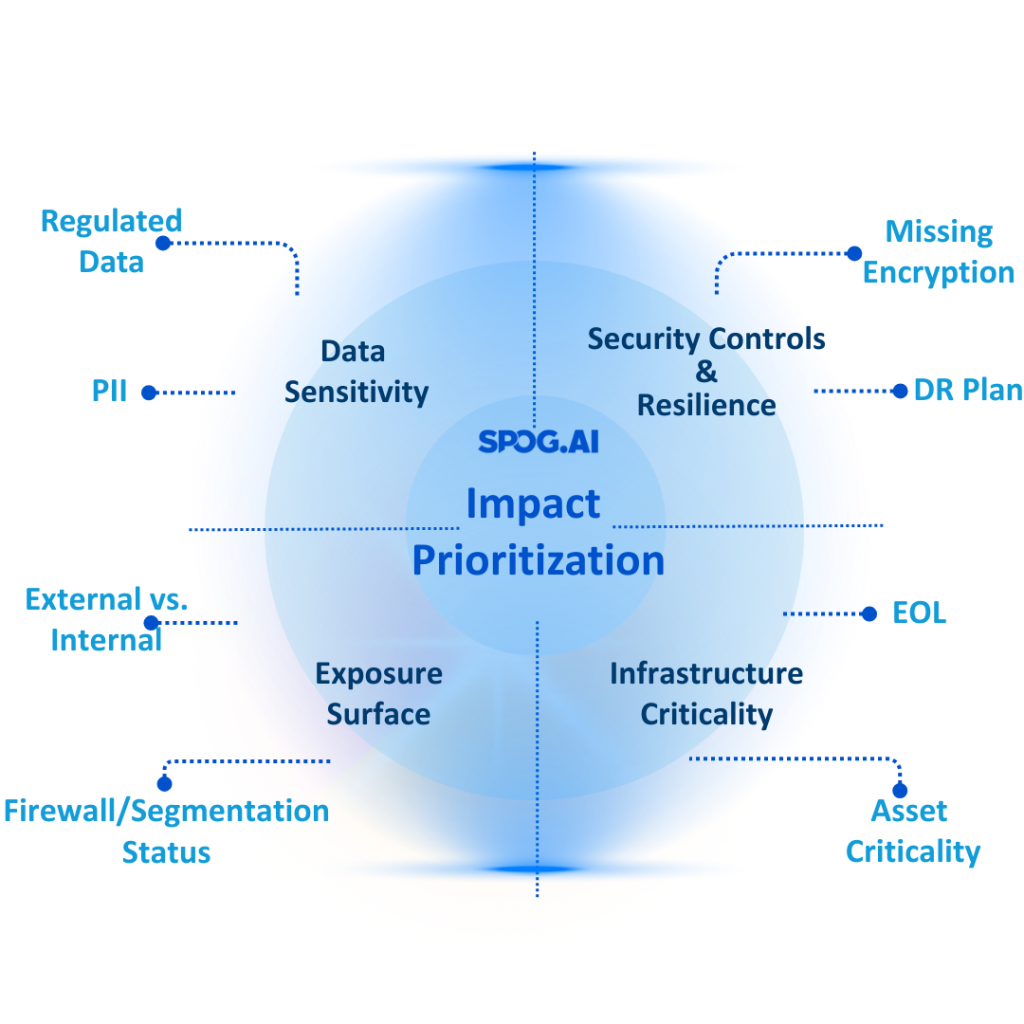
Map your risk landscape through a business lens. Group risks into action categories like:
- Critical—Act Now: High-impact risks on vital assets with weak controls
- Medium—Plan and Track: Medium risks tied to long-term business goals
- Low—Monitor: Low-impact items with adequate coverage
Then build a ranked view—not a bloated register. Prioritization is about surfacing the right risks, not all of them.
The result? Less firefighting. Faster decision-making. Smarter use of resources. And most importantly—measurable risk reduction where it matters most.
3. Failure to Consider Emerging Risks
Most risk assessments look backward.
They’re built on what happened last year. Last quarter. Or last time there was an audit. And while history matters, it can’t see around corners.
The real threat? What’s coming next.
Too many organizations miss this. They focus on known risks—phishing, patching, downtime—because they’re easy to quantify. Meanwhile, emerging risks—AI misuse, third-party concentration, deepfakes, geopolitical instability—slip through the cracks. No history? No data? No urgency.
But that’s exactly what makes them dangerous.
How to Close the Gap
Create space for the unknown. Emerging risks won’t always show up with clean numbers or clear playbooks. That doesn’t mean you can ignore them. It means you need to treat them as signals, not noise.
Start by building an emerging risk radar. Make it someone’s job—yes, an actual person—to track trends that might not have hit your org yet but could soon:
- Changes in regulation or geopolitical tensions
- Shifts in attacker behavior (e.g. AI-driven phishing)
- Tech disruptions (e.g. dependency on a new third-party SaaS)
- Social and reputational risks (e.g. public stance on sensitive issues)
Hold quarterly risk foresight sessions. Bring in voices from security, ops, product, compliance—even marketing. Let them share what they’re seeing on the edges. Patterns. Anomalies. Gut feelings. This isn’t about being “right”—it’s about being ready.
Then track these risks separately in your register. Tag them as “emerging.” Assign someone to monitor their evolution. Link them to potential business impacts, even if speculative. Build “what if” scenarios—not to predict the future, but to prepare for it.
Because in today’s environment, being caught off guard isn’t just costly—it’s reckless.
4. Overlooking Interconnected Risks
Risks don’t live in silos. But most assessments treat them like they do.
A ransomware attack isn’t just a security event—it’s also a data privacy, business continuity, and reputational crisis. A supply chain disruption might start with a vendor, but ripple all the way to your customers, compliance teams, and earnings calls.
Yet, when teams log risks, they rarely map the connections.
They write down what they see, not where it could spread.
The result? Blind spots. You might fix one issue, but miss the four others it triggers. You mitigate a symptom, not the system.
How to Close the Gap
Start thinking in systems, not silos. Every risk should be evaluated not just for what it is, but what it touches.
Build a risk interdependency map. It doesn’t have to be fancy. A simple visual showing how one risk can cascade into others is a game-changer. Example:
- A cloud misconfiguration → data breach → regulatory fine → drop in customer trust → revenue loss
Ask “Then what?” during assessments. For every risk:
- What happens if it materializes?
- Who else is affected?
- What downstream processes, vendors, or teams are involved?
Use tools or platforms that let you link risks, not just list them. This helps you spot clusters—risks that seem small alone but dangerous together.
Also, surface compound risks to leadership. These are the ones that cross categories—financial, technical, legal, and reputational. They deserve board-level attention because they hit multiple fault lines at once.
Because in reality? Most major incidents aren’t the result of one big failure.
They’re the result of several small ones that no one connected in time.
5. Static, Annual Risk Assessments
Here’s a familiar pattern: once a year, everyone scrambles.
Spreadsheets fly. Risks are logged. Scores are debated. The register gets updated. And then? Nothing. The document goes cold. Tucked into a folder. Forgotten until next year.
That’s not a risk assessment. That’s a ritual.
And in today’s volatile world, a once-a-year snapshot is dangerously outdated before the ink dries.
Threats don’t wait for your calendar. Why should your risk process?
How to Close the Gap
Shift from static to continuous risk management. Annual risk reviews are fine as a baseline—but they’re not enough. You need a rhythm that matches the pace of change.
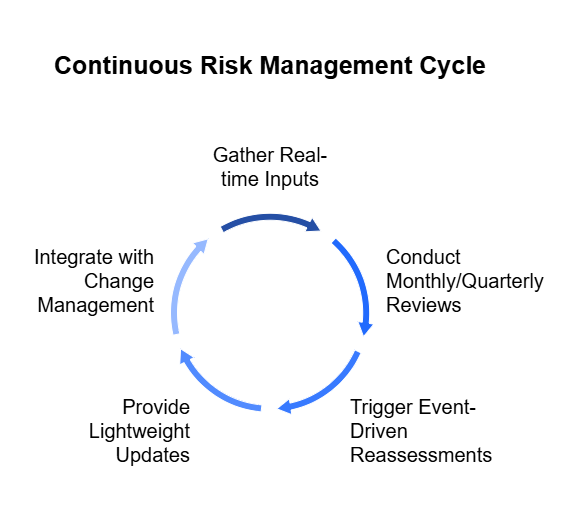
Build a risk cadence that operates on multiple levels:
- Real-time inputs from monitoring tools, threat intel, and incident data
- Monthly or quarterly reviews to update scoring and check for new threats
- Event-driven reassessments when something changes—a new vendor, a product launch, a breach in the industry
Create triggers, not checklists. Don’t just wait for the next big review. Set automated alerts for high-impact events (e.g. critical patch failures, new data exposure, M&A activity). Make it easy for teams to raise new risks outside the review cycle.
And make updates lightweight but visible. You don’t need a 30-page refresh every month. Just enough to keep leadership informed and teams aligned.
Most importantly: tie risk reviews to change. Any time your business shifts—tech stack, markets, vendors—your risks shift too. Treat risk updates as part of your business change management process.
Because let’s face it: if you only check your risk posture once a year,
you’re not managing risk—you’re hoping for the best.
6. Underestimating Business Impact
Not all risks come crashing through the firewall.
Some lurk in forgotten systems. Others hide behind a “low severity” label. But when they hit, they stall operations, trigger compliance failures, or erode customer trust—fast.
Here’s the issue: many teams assess risk in narrow, technical terms—CVSS scores, incident likelihood, uptime. But Enterprise Risk Management (ERM) isn’t about technicality. It’s about business impact. And without that lens, even your best-scored risk assessments fall short.
If you’re not connecting the dots between risk and how it affects revenue, reputation, and regulation, you’re not practicing operational risk management—you’re checking boxes.
How to Close the Gap
Start with this principle: technical severity ≠ business severity. A low CVSS score vulnerability on a critical billing system can cause more damage than a high-scoring one buried in a test server.
To fix this, ask every time:
- What core business function does this risk touch?
- Who are the stakeholders or customers affected?
- What are the downstream costs—financial, legal, operational—if it goes bad?
Bring in business voices. Don’t leave risk scoring to IT alone. Involve finance, product, operations, and legal. They’ll give you better insight into potential losses, SLA impacts, compliance exposure, and customer fallout.
Use Business Impact Analysis (BIA) frameworks to translate risk into plain, business-relevant language. This makes risk visible—and actionable—to executives.
Then, reshape your reporting. Instead of:
“High risk: internal database misconfiguration.”
Say:
“Customer database risk. Potential downtime = $1M/day. SLA breach + regulatory fine risk.”
That’s not just a risk entry. That’s a boardroom alert.
When you bake business impact into your ERM and operational risk models, you shift from playing defense to driving strategy.
You stop chasing vulnerabilities and start protecting value.
7. Insufficient Stakeholder Engagement
Risk doesn’t live in a vacuum—and neither should your risk assessments.
But too often, they do. A handful of security or compliance folks fill out the forms. Maybe IT chimes in. The results get summarized in a slide deck. And that’s it. No one from product. No one from finance. No one from operations or customer success.
The result? An Enterprise Risk Management (ERM) process that’s disconnected from the actual enterprise.
When the people closest to day-to-day operations aren’t involved, you miss the practical risks that never show up in logs. You overlook how risk decisions play out in customer experience, revenue flow, or supply chain execution.
That’s a failure of operational risk management, plain and simple.
How to Close the Gap
Make risk a team sport. You need cross-functional input—not just at the review stage, but during identification, scoring, and prioritization.
Start by building a risk steering group or committee. Keep it lean but diverse: security, IT, finance, product, ops, legal, compliance. These are your translators—the people who turn risk insights into business actions.
Hold regular, structured conversations, not ad-hoc check-ins. Ask each team:
- What’s changed in your world?
- Where are the failure points?
- What’s keeping you up at night?
Use these insights to validate or challenge your existing risk register. You’ll catch blind spots and surface operational realities that dashboards can’t show.
Also, lower the barrier to entry. Not everyone speaks “risk.” Create lightweight intake forms, unified security dashboards, where teams can flag concerns in real time — without needing to write a policy paper.
Finally, close the loop. When a risk is reported or reassessed, share the decision and next steps. People stay engaged when they see their input move the needle.
Because here’s the thing:
Engaged stakeholders don’t just spot risks—they help solve them.
And that’s the kind of culture enterprise risk management should be building.
8. No Actionable Mitigation Plans
Spotting a risk is one thing.
Doing something about it? That’s where most enterprise risk assessments fall apart.
You’ve seen it: the risk register is packed with findings, maybe even scored and sorted. But there’s no clear plan to reduce the risk. No assigned actions. No owners. No deadlines. Just rows in a spreadsheet.
This creates a dangerous illusion: “We’ve assessed the risk, so we’ve handled it.”
Not true. A risk documented but unaddressed is a risk waiting to escalate.
How to Close the Gap
Every risk you track should have a clear, actionable mitigation plan. Not a vague intention. A plan. With specific tasks, timelines, and accountable owners.
Here’s how to make that real:
- Define clear steps. Is it patching a vulnerability? Revising a vendor agreement? Launching awareness training? Spell it out.
- Assign ownership. Not to a group—to a person. Someone accountable, who can drive progress and report back.
- Set deadlines. Risks without timeframes become background noise. Make timelines realistic but firm.
Then, go a step further: automate your response wherever possible.
Too many teams are stuck in manual follow-up loops—emails, spreadsheets, check-ins. It’s slow. It’s inconsistent. And it burns time that should be spent reducing risk, not tracking it.
Automate the routine:
- Auto-trigger patching for known exploitable vulnerabilities.
- Auto-alert when a system drifts from baseline configuration.
- Auto-assign mitigation tickets to the right teams when certain risk thresholds are hit.
This doesn’t just save time—it ensures consistency. And it closes the gap between awareness and action.
Also, make risk mitigation measurable. Track status. Measure completion. Tie efforts to real risk reduction metrics.
If you can’t show movement, you’re not managing risk—you’re admiring it.
Because in the end, a good risk assessment doesn’t just say,
“Here’s what could go wrong.”
It says, “Here’s what we’re doing about it.”
9. Limited Integration with Strategic Planning
Too often, risk management happens in a vacuum.
Security teams run assessments. Risk teams compile registers. Executives set strategy. And these conversations rarely overlap. The result? Business plans move forward without a real understanding of risk—and risk assessments are built without knowing what’s coming next.
That’s a disconnect. And in today’s environment, disconnected equals vulnerable.
If Enterprise Risk Management (ERM) isn’t feeding into strategic decisions—new markets, product launches, tech investments, M&A—you’re missing a huge opportunity. Worse, you’re making big bets without seeing the downside.
How to Close the Gap
Embed risk thinking into strategic planning.
Don’t treat it as a compliance sidebar—make it part of the business planning cycle.
Here’s how:
- When building new strategies, review relevant risks up front. What could derail this initiative? What dependencies, vendors, or systems introduce exposure?
- During quarterly planning or OKR reviews, revisit the risk landscape. What’s shifted? What’s emerging? What’s worth escalating?
- For major initiatives—cloud migrations, product expansions, acquisitions—run a dedicated risk impact analysis as part of your decision-making process.
Make risk teams partners, not just reporters. Pull them into product reviews, vendor selection, budget planning. When risk is part of the conversation early, mitigation becomes design—not damage control.
Also, show leadership the full picture. Don’t just report risk as a technical metric. Connect it to strategic outcomes:
- “This risk could delay our product roadmap.”
- “This vendor dependency exposes us in the new market.”
- “This gap increases audit failure probability by X%.”
That’s language the C-suite understands.
Finally, tie risk indicators to business KPIs. When risk metrics support business outcomes—customer trust, uptime, revenue growth—they stop being background noise and start driving decisions.
Because strategic planning without risk context?
That’s just hope in a PowerPoint.
10. Lack of Risk Culture and Training
You can have the best risk framework in the world.
But if no one understands it—or cares about it—it won’t matter.
Here’s what happens: risk management gets boxed into one team. Everyone else assumes it’s “someone else’s job.” Risks get underreported. Controls get ignored. People click the phishing link. And when something breaks, there’s panic instead of process.
This isn’t a tools problem. It’s a culture problem. And in most organizations, it’s the root cause behind weak Enterprise Risk Management (ERM) and broken Operational Risk Management (ORM).
How to Close the Gap
Start with mindset. Risk isn’t just a function—it’s a shared responsibility.
Everyone, from engineering to HR to finance, plays a role in identifying and managing risk. But they need two things to do it well: awareness and confidence.
- Train broadly, not just deeply. Don’t limit training to security or compliance. Give everyone risk literacy—how to spot issues, who to tell, what good risk hygiene looks like.
- Make it role-specific. A product manager doesn’t need to know ISO 27001 clauses—but they do need to understand third-party risk and data privacy exposure in product design.
- Reinforce through storytelling. Use internal examples and near-misses to highlight impact. “Remember that outage? That started with a missed alert. Here’s how we prevent that now.”
- Reward risk awareness. When people raise concerns early or take proactive steps, recognize them. Culture shifts through reinforcement—not just policies.
Most importantly: lead by example. If leadership shrugs off risk or only engages after an incident, the rest of the organization will too. But if they ask hard questions, join the reviews, and act on findings? That behavior cascades.
You can’t automate culture.
But you can build it—through consistency, visibility, and real conversations.
Because the strongest risk program isn’t driven by tools.
It’s driven by people who care enough to act.
Conclusion
Enterprise risk isn’t static—and your approach to managing it can’t be either.
In a world where threats evolve daily, checklist-style assessments, once-a-year reviews, and siloed reporting are no longer enough. The real cost of risk isn’t just in the incidents you didn’t see coming. It’s in the ones you saw—but failed to act on.
From inconsistent scoring and weak prioritization to overlooked business impact and a culture that treats risk as someone else’s problem—these 10 gaps are common, but they’re not inevitable.
You can close them.
By shifting from reactive to strategic.
By embedding risk into planning—not just reporting.
By training teams to recognize threats and empowering them to respond.
Most of all, by treating Enterprise Risk Management as a living, breathing process—one that reflects how your business really works, and how it really fails.
Fix the gaps, and your risk program becomes more than a safety net.
It becomes a competitive edge.
