A single data breach can erode customer trust, disrupt operations, and invite severe regulatory penalties. That’s why cybersecurity risk assessment in banking has become essential—not just for compliance, but for resilience.
Unlike generic IT risk frameworks, a banking-specific risk assessment must account for sector-specific factors such as:
- Real-time transaction fraud
- Payment system vulnerabilities (e.g., SWIFT, NEFT, UPI)
- Third-party fintech integrations
- Regulatory mandates from bodies like RBI, SEBI, and more
At the heart of this process lies the risk assessment matrix—a tool that helps institutions visualize and prioritize cyber threats based on likelihood and impact. When integrated into an actionable risk register and broader enterprise risk assessment strategy, it becomes a catalyst for informed decision-making.
This guide explores how banks can design and implement a cybersecurity risk matrix tailored to their unique challenges. We’ll cover the types of risk most relevant to banking, offer templates, and share insights on aligning risk assessments with enterprise-level goals and compliance obligations.
Why Cybersecurity Risk Assessment Matters in Banking
The financial sector is a prime target for cybercriminals—and for good reason. Banks manage high-value assets, handle massive volumes of sensitive customer data, and provide access to critical infrastructure like payment networks and credit systems. A single vulnerability can have cascading effects not only on the institution itself but also on the broader economy.
The Rising Threat Landscape
Cyber threats against banks have evolved far beyond rudimentary phishing scams. Today, they include:
- Sophisticated ransomware attacks that can lock down critical banking operations
- Business email compromise (BEC) aimed at hijacking large fund transfers
- Insider threats involving rogue employees or compromised credentials
- DDoS attacks designed to disable online banking services and ATMs
- Advanced persistent threats (APTs) targeting SWIFT transactions and back-office systems
In 2024 alone, global financial institutions faced billions in losses due to cyber incidents—underscoring the urgent need for proactive risk management.
Regulatory Imperatives
Governments and financial regulators have responded with stringent cybersecurity mandates. Depending on your jurisdiction, your cybersecurity risk assessment must align with one or more of the following:
Indian Regulatory Compliance Imperatives
1. Reserve Bank of India (RBI)
The RBI has issued several mandates to strengthen cybersecurity and enterprise risk management in the banking sector:
- Cyber Security Framework for Banks (2016): Mandates banks to identify, assess, and manage IT and cyber risks, including through regular risk assessments and dynamic threat monitoring.
- Baseline Cyber Security Controls (2020): Issued for UCBs and NBFCs, calling for board oversight, risk prioritization, and regular vulnerability assessments.
- Risk-Based Internal Audit (RBIA): RBI requires risk identification and categorization in internal audit processes, where cybersecurity risk plays a major role.
- Comprehensive Cyber Drill Mandates: Banks must conduct simulated cyber attack exercises and include outcomes in their risk registers.
2. Securities and Exchange Board of India (SEBI)
SEBI’s cybersecurity framework applies to banks involved in capital markets, mutual funds, and depository operations. Key guidelines include:
- Cybersecurity & Cyber Resilience Framework (2019, updated 2023) for market intermediaries.
- Requires risk-based categorization of IT assets, threat prioritization using matrix-based approaches, and regular board reporting on cyber posture.
These mandates necessitate structured cybersecurity risk matrices tailored to specific financial operations—whether it’s lending, trading, or fund management.
Global Frameworks Complementing Indian Compliance
Indian banks operating internationally, or those integrated with global systems like SWIFT, must also align with broader enterprise risk management standards:
- ISO/IEC 27001 & ISO 27005: International standards for information security risk management, emphasizing structured risk assessments and risk treatment plans.
- NIST Cybersecurity Framework (CSF): Encourages organizations to Identify, Protect, Detect, Respond, and Recover from cyber threats—often implemented using matrices and maturity models.
- SWIFT Customer Security Programme (CSP): Requires annual independent assessments of cybersecurity posture for banks using the SWIFT network.
- Basel Committee Guidelines: Recommends that banks embed cybersecurity within their enterprise risk management systems and regularly assess IT risk exposure.
Common Types of Cyber Risks in Financial Institutions
A well-structured cybersecurity risk assessment must begin with a thorough understanding of the different types of risk unique to financial institutions.
Below are the most critical categories to include in your risk assessment matrix, particularly when aligned with RBI, SEBI, ISO 27005, and NIST frameworks.
1. Phishing and Social Engineering Attacks
Phishing emails, SMS scams, and voice fraud (vishing) are commonly used to trick employees or customers into revealing credentials or initiating fraudulent transactions. Banks are frequent targets due to their direct access to funds and sensitive data.
- Impact: Unauthorized fund transfers, data leakage, account takeover
- Controls: Security awareness training, email filters, transaction alerts
2. ATM and POS Malware Attacks
Malware injected into ATMs or point-of-sale terminals can intercept PIN data or manipulate withdrawal commands.
- Impact: Cash loss, financial fraud, reputational damage
- Controls: Endpoint protection, network segmentation, ATM software whitelisting
3. Unauthorized Access and Privilege Escalation
Attackers may exploit vulnerabilities to gain unauthorized access to banking systems, often through compromised admin credentials or insecure APIs.
- Impact: Breach of customer accounts, tampering with core banking systems
- Controls: Multi-factor authentication (MFA), role-based access controls, privileged access monitoring
4. Third-Party and Vendor Risk
Banks often depend on third-party vendors for payment gateways, KYC processing, or cloud services. Any security flaw in these integrations can expose core systems.
- Impact: Data breaches, service disruptions, non-compliance
- Controls: Vendor due diligence, contractual SLAs, third-party risk assessments
5. Distributed Denial of Service (DDoS) Attacks
DDoS attacks aim to flood online banking platforms with traffic, rendering them inaccessible and disrupting customer transactions.
- Impact: Service outages, loss of trust, regulatory penalties
- Controls: DDoS mitigation tools, traffic filtering, cloud-based anti-DDoS services
6. Data Leakage and Insider Threats
Not all threats are external. Employees or contractors with legitimate access can intentionally or accidentally leak customer or transactional data.
- Impact: Regulatory breaches (e.g., under DPDP Act, 2023), reputational harm
- Controls: Data loss prevention (DLP), user behavior analytics (UBA), zero trust architectures
7. Ransomware and File Encryption Attacks
Attackers can encrypt banking databases and demand ransom payments to restore access, potentially halting business operations.
- Impact: Operational downtime, financial extortion, data loss
- Controls: Regular backups, incident response playbooks, endpoint detection and response (EDR)
8. Compliance Failures
Failure to assess and mitigate cyber risks can lead to non-compliance with RBI/SEBI mandates, ISO standards, or global requirements like GDPR/SWIFT CSP.
- Impact: Legal penalties, license suspension, audit failures
- Controls: Periodic assessments, audit trails, automated compliance reporting
Mapping Risks to a Matrix
Each of the above risks should be evaluated in a risk assessment matrix based on:
- Likelihood: How probable is the event?
- Impact: What is the potential damage?
This prioritization allows banks to channel resources effectively—focusing on the most pressing threats while maintaining a holistic enterprise risk management view.
How to Use the Risk Matrix
- Identify cybersecurity risks across systems, people, and vendors.
- Score each based on RBI/SEBI-compliant threat modeling.
- Prioritize based on matrix zones (e.g., address reds first).
- Assign ownership and define timelines within your risk register.
- Monitor risk status and re-score periodically or post-incident.
This structured approach ensures that cybersecurity is embedded into your bank’s day-to-day governance—making audits smoother, decisions smarter, and operations more secure.
Integrating with a Risk Register and ERM Strategy
Creating a risk assessment matrix is only the first step. To truly operationalize cybersecurity within a bank, those matrix insights must flow into a risk register and align with a broader enterprise risk management (ERM) strategy. This integration ensures that cybersecurity risks are not treated in isolation but are managed alongside financial, operational, strategic, and compliance risks.
Let’s explore how banks can build this integration for scalable, auditable, and board-level risk visibility.
What Is a Risk Register?
A risk register is a centralized, living document or platform that captures:
- Identified risks
- Risk scores (likelihood × impact)
- Assigned owners
- Mitigation strategies
- Current status (open, in progress, mitigated)
- Review dates and outcomes
For cybersecurity, each row in your register should correspond to a risk highlighted in your matrix. This ensures continuity between identification, prioritization, and treatment.
RBI/SEBI Alignment:
Regulators such as RBI (via the Cybersecurity Framework) and SEBI (via Cyber Resilience Guidelines) mandate structured documentation of cyber threats, incidents, controls, and mitigation plans. A well-maintained risk register fulfills this obligation and serves as a ready tool during audits or supervisory reviews.
Embedding Cyber Risk into Enterprise Risk Management
An enterprise risk assessment looks at all major risk domains under a unified framework. For cybersecurity risks to get the attention and resources they deserve, they must be embedded into this enterprise view.
Here’s how to ensure alignment:
- Map Cyber Risks to Strategic Objectives
Link each cybersecurity risk to core banking priorities—such as customer trust, regulatory compliance, or uninterrupted digital services. - Assign Ownership Across Functions
Risk ownership should be distributed beyond IT. For example:- Fraud team handles social engineering threats
- Compliance handles regulatory penalties
- HR handles insider threats
- Define Escalation Protocols
Ensure that risks crossing certain thresholds (e.g., “Critical” score) are automatically escalated to the Risk Committee or Board, as mandated by RBI circulars. - Standardize Reporting
Use dashboards and heatmaps to communicate cyber risk exposure alongside other business risks during executive and board meetings. - Ensure Cross-Functional Reviews
Coordinate periodic joint reviews involving IT, Compliance, Operations, and Business Units to re-score risks, update controls, and revise action plans.
Tools & Automation
For banks with extensive operations, managing this process manually can be error-prone. Consider tools that offer:
- Automated risk scoring based on threat feeds and incident history
- Integrated risk registers with audit trails and version control
- Real-time dashboards for visualizing risk posture
- Compliance mapping to RBI, SEBI, ISO, and NIST controls
Benefits of Full Integration
| Benefit | Impact |
| Regulatory Readiness | Smooth audits, reduced compliance risk |
| Enterprise-Wide Risk Visibility | Informed strategic decisions by the board and CXOs |
| Faster Response & Recovery | Clear ownership and pre-defined mitigation protocols |
| Reduced Operational Silos | IT, legal, and business units collaborate on cyber risks |
When integrated correctly, your risk assessment matrix becomes the foundation for a dynamic, responsive, and enterprise-wide risk management system.
Case Studies: Lessons from Recent Banking Cyber Attacks
Real-world incidents offer powerful lessons in the importance of proactive cybersecurity risk assessment. Below are notable cyberattacks on banks—both in India and globally—that highlight what can go wrong without a robust risk assessment matrix and risk register in place.
Case Study 1: Cosmos Bank (India), 2018
Type of Attack: Malware and SWIFT compromise
Loss: ₹94 crore (~$13.5 million) siphoned off in two days
What Happened:
Hackers breached the bank’s internal systems and bypassed authentication mechanisms to fraudulently authorize SWIFT transfers and ATM withdrawals across multiple countries.
Missed Risk Factors:
- Inadequate network segmentation between core banking and SWIFT systems
- Absence of real-time transaction anomaly detection
- Weak access controls and no privilege escalation monitoring
Risk Matrix Insight:
This incident would have scored Critical on both likelihood and impact if the matrix had modeled SWIFT fraud risk properly. Proper mapping to the risk register could have enabled stronger third-party isolation and transaction control.
Case Study 2: Canara Bank, 2016Type of Attack: Malware in ATM infrastructure
Impact: Cardholder information compromised
What Happened:
An ATM managed by a third-party vendor was found to be infected with malware that copied user card data and PINs. These were then used for unauthorized withdrawals.
Missed Risk Factors:
- Poor third-party risk assessment and vendor security validation
- Lack of endpoint monitoring on ATM terminals
- No automated alerts for unusual transaction patterns
Risk Matrix Insight:
A well-defined third-party risk matrix could have flagged vendor-managed ATMs as high-risk assets. Assigning ownership and implementing DLP measures would have prevented or reduced the breach impact.
Case Study 3: Capital One (U.S.), 2019
Type of Attack: Cloud misconfiguration & insider threat
Data Breached: 100 million customer records
What Happened:
A former employee exploited a vulnerability in a misconfigured AWS firewall, gaining access to sensitive data stored in the bank’s cloud environment.
Missed Risk Factors:
- Misconfiguration in cloud IAM policies
- Lack of continuous configuration assessments
- Insider activity not flagged by behavior analytics tools
Risk Matrix Insight:
A mature enterprise risk assessment would have modeled cloud service risks as high-likelihood, especially in hybrid architectures. Tracking such risks in a central risk register with controls around IAM and data governance would have reduced exposure.
Key Lessons from These Attacks
| Lesson | Why It Matters |
| Visibility across all IT and third-party assets | Unseen assets are unmanaged and unprotected |
| Risk ownership and response clarity | Lack of accountability leads to response delays |
| Continuous reassessment | Static matrices miss evolving threats like zero-days and insider tactics |
| Risk-to-business mapping | High-impact risks often don’t seem technical—until they hit core revenue streams |
These cases underscore a critical truth: cybersecurity risk assessments must be living, adaptive processes, not annual check-the-box exercises. A regularly updated risk assessment matrix, integrated with an active risk register and monitored by a cross-functional team, is the only way to stay ahead of adversaries in banking.
Templates for Banking Risk Assessment
To translate strategy into execution, banks need ready-to-use, customizable templates that embed cybersecurity into daily operations and regulatory reporting. These templates should support the visualization, prioritization, and tracking of cyber risks—while aligning with RBI, SEBI, and global frameworks such as ISO 27001, NIST CSF, and SWIFT CSP.
Below are key templates every bank should consider to operationalize its risk assessment matrix and enterprise risk management (ERM) practices.
1. Cybersecurity Risk Assessment Matrix Template (5×5)
Features:
- Pre-defined risk categories (Phishing, Insider Threats, DDoS, etc.)
- Likelihood and impact scoring system
- Automated heatmap with conditional formatting
- Editable matrix cells to suit organizational risk scales
Use Case: Helps visualize high-impact cybersecurity threats and drive prioritization.
✅ Regulatory Fit: Aligns with RBI Cyber Security Framework and SEBI’s risk-tiered controls.
2. Cyber Risk Register Template
Features:
- Risk ID, category, and detailed description
- Likelihood, impact, and calculated risk score
- Assigned owners, mitigation plans, deadlines
- Real-time status tracking (Open, In Progress, Mitigated)
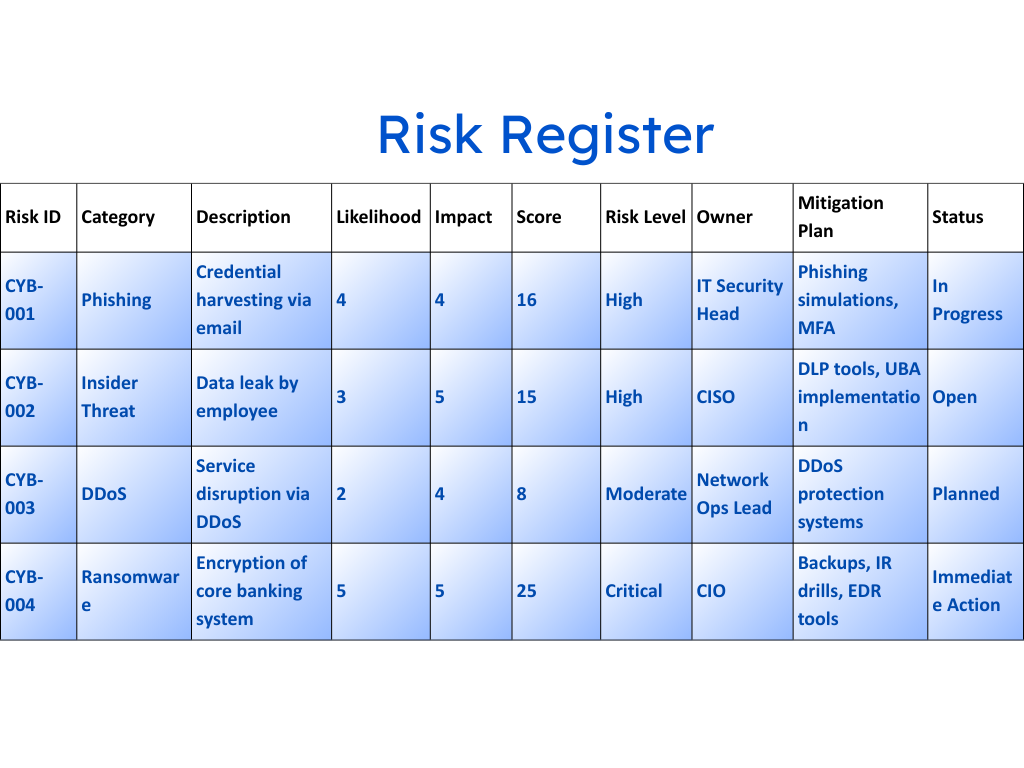
Use Case: Ideal for internal audits, IT governance reviews, and board presentations.✅ Regulatory Fit: Satisfies documentation mandates from RBI and SEBI for internal cybersecurity posture reporting.
3. Enterprise Risk Dashboard Template
Features:
- Visual risk summary: charts, trendlines, and KPIs
- Aggregated view of cyber, operational, compliance, and fraud risks
- Filtering by business unit, system, or risk owner
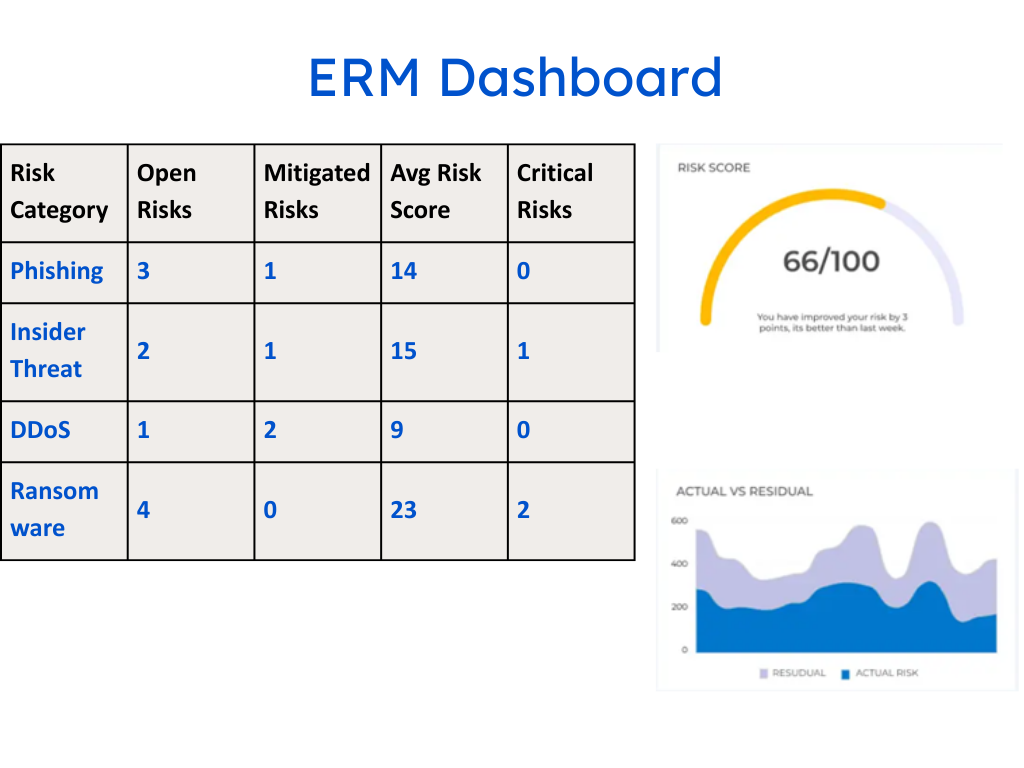
Use Case: Provides risk committees and CXOs with a birds-eye view of evolving risk exposure.
✅ Regulatory Fit: Maps to Basel Committee recommendations on ERM integration.
4. Vendor Risk Assessment Checklist
Features:
- Third-party vendor scoring (Data access, network integration, compliance levels)
- Residual risk evaluation after control implementation
- SLA and contract evaluation markers
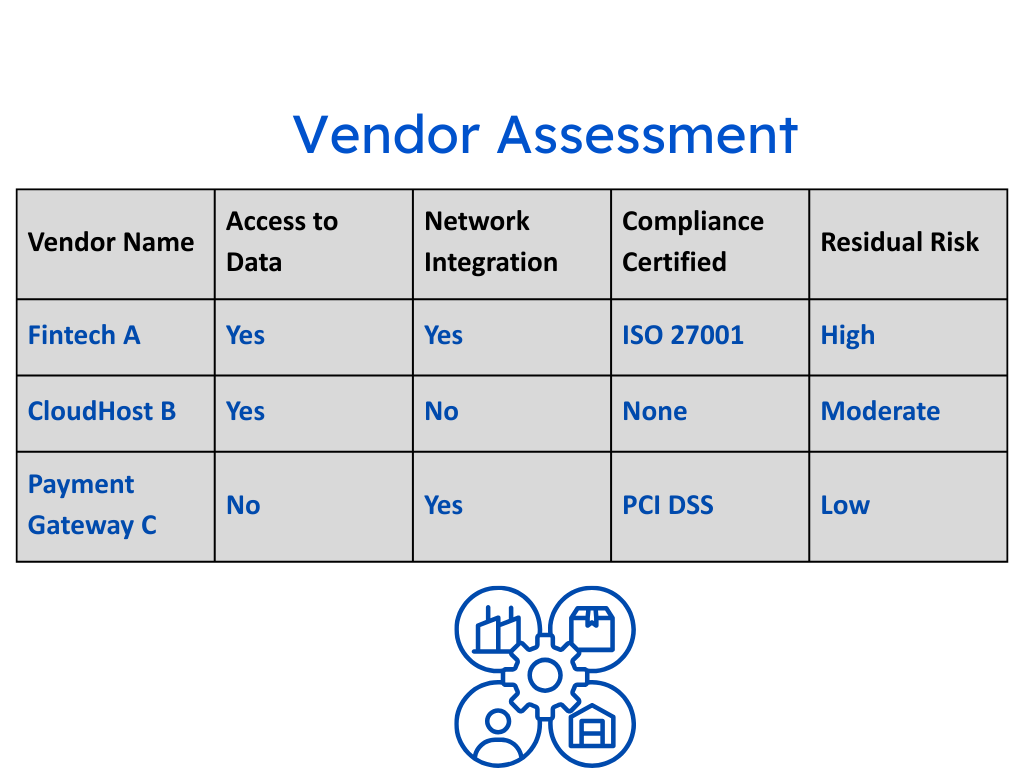
Use Case: Helps banks secure fintech integrations, outsourced IT services, and API providers.
✅ Regulatory Fit: Supports SEBI’s intermediary oversight and RBI’s third-party risk guidelines.
5. Incident Response Risk Feedback Loop
Features:
- Post-incident reassessment fields
- Re-scoring capability after events (e.g., phishing, DDoS)
- Links incident records back into the risk matrix and register
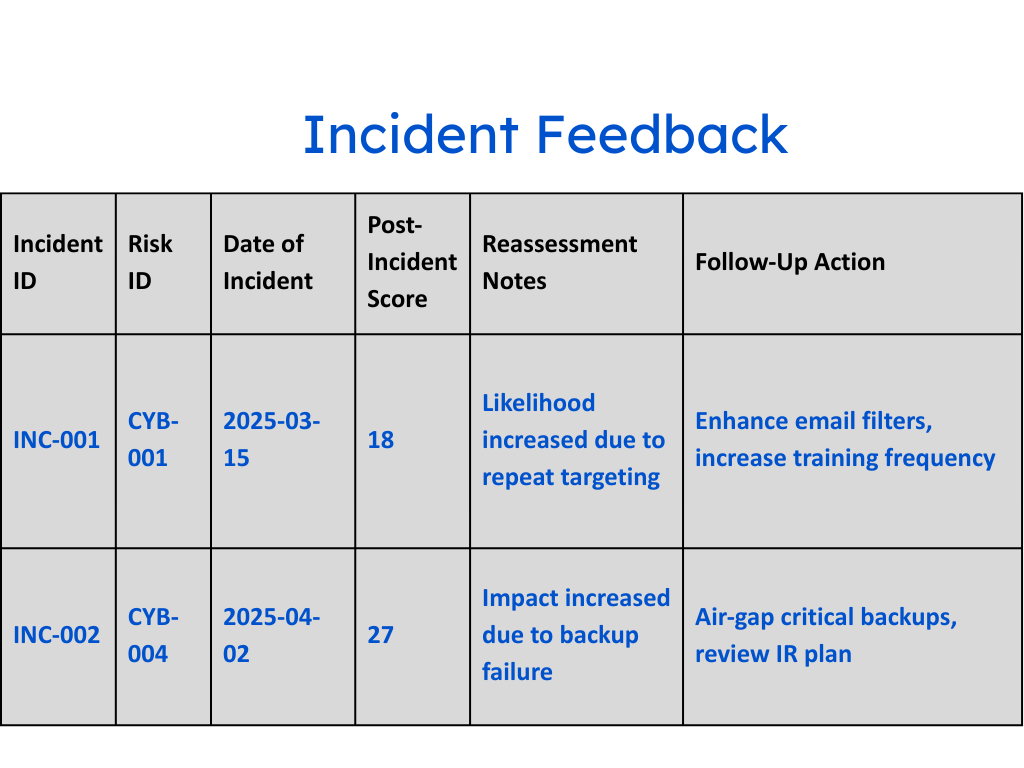
Use Case: Ensures dynamic updates to the matrix post-cyber events.
✅ Regulatory Fit: Meets RBI’s requirement for cyber incident learnings to be reflected in internal risk frameworks.
How to Use These Templates
- Customize to reflect your bank’s size, systems, and services (retail, corporate, NBFC, cooperative).
- Automate scoring and reporting with tools like Excel, Google Sheets, or GRC platforms.
- Review Quarterly to remain compliant and responsive to threat landscape changes.
- Integrate with your internal audit function, cyber drills, and board-level reviews.
💡 Pro Tip: Maintain version history of all templates for audit purposes and link risk registers to incident logs for traceability.
Conclusion
As banks face increasingly complex threats, a static checklist is no longer sufficient. They need a dynamic, actionable approach to cyber risk—one that integrates seamlessly into broader enterprise risk management strategies.
The cybersecurity risk assessment matrix plays a vital role in this transformation. By helping banks visualize, prioritize, and respond to a wide range of cyber threats—from phishing and ransomware to insider threats and cloud misconfigurations—it empowers teams to act before damage is done.
But the matrix is just the starting point.
- Feeding this analysis into a living risk register
- Aligning it with regulatory frameworks like RBI, SEBI, ISO, and NIST
- Reviewing and updating it regularly based on evolving risks and real-world incidents
…these are the practices that separate reactive institutions from resilient ones.
The templates we’ve provided can help your organization take that leap—from compliance to competence. Whether you’re preparing for an RBI cyber audit, planning your next internal security drill, or presenting risk exposure to the board, these tools will help you deliver not just data—but decisive action.
In banking, cybersecurity risk isn’t just IT’s problem—it’s everyone’s priority. Equip your team with the frameworks, templates, and insights they need to protect your institution and your customers.
