Managing risk in hybrid infrastructure is no small task. Data often spans physical servers, virtual machines, and cloud services, increasing the likelihood of misconfigurations and visibility gaps. IBM’s recent data breach report reveals that hybrid environments experience some of the highest average breach costs—$4.53 million per incident. This is not only due to direct penalties and data loss, but also the long mean time to identify (MTTI) and remediate breaches. The time it takes to discover a breach remains longest in multi-cloud and hybrid deployments.
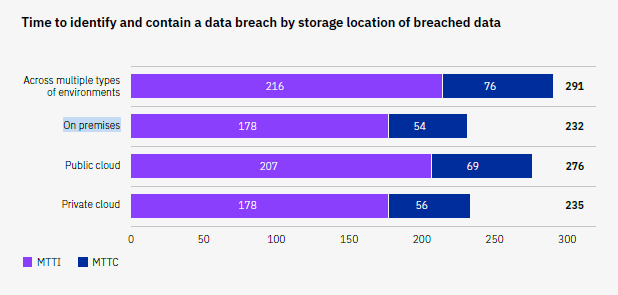
These delays are costly. While threat actors often act within hours, detection in hybrid systems can take days or even weeks. Fragmented monitoring and inconsistent controls create prolonged exposure, making remediation more complex and expensive.
Simultaneously, regulatory pressure is rising. Compliance frameworks like SOC 2, ISO 27001, and NIST 800-53 demand continuous monitoring, detailed documentation, and rigorous access controls. According to a Flexera report, 68% of IT leaders cite regulatory compliance as a primary driver for securing their hybrid infrastructure. Failing to meet these standards can result in audit failures, legal liabilities, and loss of customer trust.
Despite the high stakes, many organizations still rely on manual tracking, ad hoc reporting, and outdated processes. These approaches don’t scale in hybrid environments and often lead to errors, delays, and compliance fatigue.
This guide offers a better way forward. Whether you’re preparing for your first audit or refining an existing program, you’ll find practical strategies and tools to help you secure your hybrid data center, simplify compliance, and adopt automation that reduces effort while improving outcomes.
The Building Blocks of Data Center Security
With the challenges and urgency now clear, the next step is to understand the foundational layers of security that protect hybrid data centers. These environments span multiple platforms—on-premises servers, co-location facilities, cloud services, and edge networks—so effective protection requires a comprehensive, layered security model that works across boundaries.
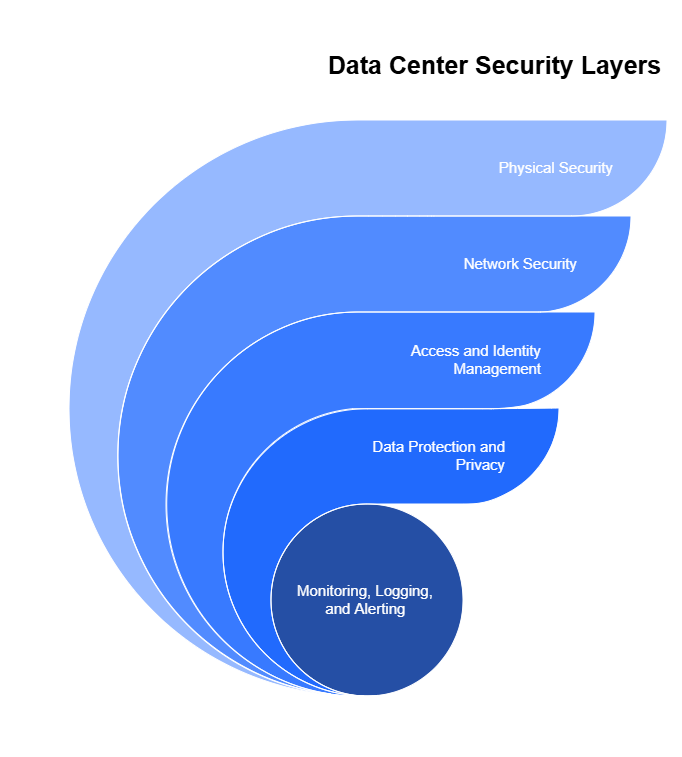
Physical Security
Even in highly virtualized or cloud-integrated environments, physical infrastructure remains a critical component. On-premises systems and co-location sites must be secured against unauthorized access, tampering, and environmental hazards. This begins with perimeter defenses such as fencing, surveillance cameras, and security guards. Inside the facility, access is restricted using badge systems, biometric scanners, and mantraps that prevent tailgating.
Environmental safeguards also play a key role. Fire suppression systems, water detection, redundant power (UPS), and HVAC monitoring help ensure uptime and protect against physical failure. These controls are often overlooked in favor of digital security—but for compliance frameworks like SOC 2 and ISO 27001, physical safeguards are a baseline requirement.
Network Security
In a hybrid model, your network perimeter extends beyond a single data center. Systems communicate over VPNs, private circuits, and public internet paths, often across multiple providers. That makes segmentation, firewall management, and intrusion detection systems (IDS/IPS) essential.
You must isolate sensitive workloads from public-facing services and enforce strict access rules between environments. Today, end-to-end encryption and Zero Trust architecture are no longer optional. Every connection—internal or external—should be authenticated, authorized, and continuously monitored to reduce lateral movement in the event of a breach.
Access and Identity Management
One of the most common gaps in hybrid security is inconsistent identity management. Users and admins often have credentials spanning Active Directory, cloud IAM platforms, and SaaS logins. Without centralized governance, it’s easy for excessive or outdated permissions to go unnoticed.
Implementing robust identity and access management (IAM)—including role-based access control (RBAC), least privilege, and multi-factor authentication (MFA)—is essential. Federated identity services and single sign-on (SSO) can help unify access across platforms. Regular access reviews and centralized logging of administrative activity are both required for audit readiness.
Data Protection and Privacy
Hybrid environments often involve data replication, backups, and workload migrations across physical and virtual boundaries. That makes data protection a moving target. You need strong encryption for data both in transit and at rest, granular access controls, and clear classification policies to manage sensitive information appropriately.
Retention and deletion policies must align with compliance mandates, especially in industries governed by HIPAA, PCI, or GDPR. Backups should be encrypted, automated, and geographically distributed. Recovery plans should be documented and tested regularly to ensure resilience against ransomware or hardware failure.
Monitoring, Logging, and Alerting
Visibility ties everything together. Hybrid systems produce vast quantities of logs—user activity, system changes, access attempts, and application events. A centralized security information and event management (SIEM) system aggregates and correlates this data across cloud and on-prem assets.
Automated alerting helps identify threats quickly by flagging anomalies and deviations from baseline behavior. When properly configured, these tools reduce mean time to detect (MTTD) and support real-time threat response, which are key to both operational success and regulatory compliance.
Key Compliance Standards Relevant to Hybrid Data Centers
Once the foundational controls are in place, aligning them with compliance frameworks becomes essential. Most organizations don’t just want secure systems—they need to demonstrate that security through certification or audit. For hybrid data centers, where infrastructure spans physical and cloud domains, that proof must cover every layer of the stack.
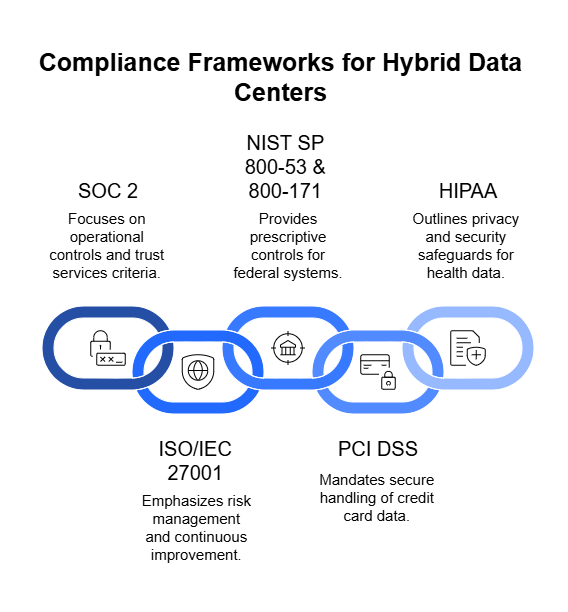
Below are the key compliance standards most relevant to hybrid environments, along with how they apply across both on-premises and cloud systems.
SOC 2 (System and Organization Controls 2)
SOC 2 is one of the most commonly adopted standards among service providers, SaaS platforms, and enterprises that handle customer data. It evaluates an organization’s controls based on five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy.
In hybrid data centers, SOC 2 requires consistent control implementation across all systems—whether they’re in a physical server room or hosted in the cloud. Auditors typically examine physical access logs, environmental safeguards, access permissions, and security monitoring. Evidence from both legacy systems and cloud-native platforms must be presented in a unified and traceable format.
ISO/IEC 27001
ISO 27001 is a globally recognized framework for managing information security risks through a formal Information Security Management System (ISMS). Unlike SOC 2, which focuses on operational controls, ISO 27001 emphasizes risk management and continuous improvement.
For hybrid environments, ISO 27001 requires organizations to assess risks across all infrastructure layers and apply controls defined in Annex A, such as access control (A.9), cryptographic protections (A.10), and physical security (A.11). It demands tight coordination between cloud governance, IT security teams, and physical operations.
NIST SP 800-53 and 800-171
These standards are widely used in U.S. government and contractor ecosystems. SP 800-53 outlines comprehensive security and privacy controls for federal systems, while SP 800-171 focuses on protecting Controlled Unclassified Information (CUI) in non-federal systems.
Both frameworks align well with hybrid infrastructures. They emphasize structured access controls, detailed audit logs, incident response readiness, and strict system configuration. NIST standards are especially helpful for organizations that need prescriptive controls with clear technical mappings.
PCI DSS (Payment Card Industry Data Security Standard)
Organizations that process credit card data—whether in a physical point-of-sale system or a cloud-hosted platform—must comply with PCI DSS. This framework mandates secure encryption, access logging, segmentation of cardholder data environments, and regular testing for vulnerabilities.
In hybrid environments, compliance requires controls to span not just cloud workloads, but also on-prem firewalls, routers, and access systems. Third-party vendors such as hosting providers and data center operators must also meet PCI standards or sign validated attestations.
HIPAA (Health Insurance Portability and Accountability Act)
For healthcare providers, insurers, and any entity dealing with Protected Health Information (PHI), HIPAA outlines strict safeguards for privacy and security. While HIPAA is more regulatory than technical, it still requires documented policies, access controls, encryption, and audit capabilities.
Hybrid infrastructures must ensure that all systems storing or transmitting PHI—whether in a private cloud, on a physical drive, or in a hosted SaaS platform—are compliant. Organizations must also execute Business Associate Agreements (BAAs) with vendors to ensure third-party compliance.
Mapping Security Controls to Compliance Requirements
After identifying the right frameworks, the next challenge is translating your existing security practices into a form that auditors can understand and verify. That’s where control mapping comes in. It connects your technical and administrative controls to specific compliance criteria, ensuring you can demonstrate how your environment meets regulatory standards.
This step is especially important in hybrid data centers, where controls may span multiple systems, vendors, and environments.
Why Control Mapping Matters in Hybrid Environments
In a hybrid setup, different teams may own different layers of infrastructure. IT might manage physical systems and co-location facilities, while DevOps handles cloud workloads and identity providers. This division often leads to inconsistent policy enforcement or gaps in documentation.
Control mapping helps eliminate those blind spots. It brings all your efforts into a single framework, showing which controls meet which requirements—and where remediation is needed. For example, if your cloud infrastructure enforces MFA but your on-prem directory does not, the mapping process will reveal the gap before the auditor does.
Example: How Controls Align Across Frameworks
Here’s a snapshot of how common controls in a hybrid data center map to multiple compliance standards:
| Control | SOC 2 (TSC) | ISO 27001 (Annex A) | NIST SP 800-53 |
| Biometric access to server rooms | CC6.1 – Logical & physical access | A.11.1 – Physical security | PE-2, PE-3 – Physical access |
| Role-based access control (RBAC) | CC6.2 – Access restrictions | A.9.1 – User access management | AC-2 – Account management |
| Firewall segmentation + IDS/IPS | CC7.1 – System operations | A.13.1 – Network security | SC-7, SC-12 – Boundary protection |
| Data encryption (at rest/in transit) | CC6.4 – Confidentiality | A.10.1 – Cryptographic controls | SC-12, SC-28 – Encryption |
| Centralized alerting & logging | CC7.2 – Monitoring | A.12.4 – Logging & monitoring | AU-2, AU-6 – Audit logs |
When you maintain a control matrix like this, you can answer audit questions with confidence and clarity. For example, if asked, “How do you ensure unauthorized users cannot access sensitive systems?” you can point to biometric locks, audit logs, and access provisioning workflows—already documented and aligned to each requirement.
How to Build Your Own Compliance Control Matrix
To create a working control matrix for your environment:
- Identify your applicable frameworks: Choose based on customer expectations, industry regulations, and risk exposure.
- List all security controls: Include both technical (e.g., firewalls, IAM) and administrative (e.g., training, policies) controls.
- Map each control to relevant requirements across SOC 2, ISO, NIST, or others.
- Document supporting evidence such as access logs, screenshots, policy PDFs, and configuration settings.
- Use automation tools where possible (e.g., Vanta, Drata, Tugboat Logic) to continuously collect and validate evidence.
- Review and update regularly as systems evolve or frameworks are updated.
A well-maintained matrix not only accelerates audits—it helps teams stay aligned, reduces duplication of effort, and builds institutional memory.
Next, we’ll examine where organizations most often fall short—and how to avoid those pitfalls in your own hybrid compliance journey.
Common Security Gaps in Hybrid Data Center Compliance
Even with well-defined controls and mappings in place, many organizations still face challenges when preparing for audits or responding to incidents. In hybrid environments, the mix of physical and virtual systems introduces complexity—and complexity often leads to oversight. By identifying common gaps, you can take proactive steps to close them before they result in audit findings or breaches.
Inconsistent Access Controls Across Environments
Hybrid infrastructures often rely on multiple identity providers—such as on-premises Active Directory, cloud IAM platforms, and external SSO tools. Without centralized governance, it’s easy for access policies to drift out of sync. Some systems may require MFA, while others do not. Or worse, users may retain access long after they’ve left the organization.
These inconsistencies violate least privilege principles and raise red flags during audits. Auditors look for clear access provisioning workflows, de-provisioning timelines, and enforcement of access reviews across all systems.
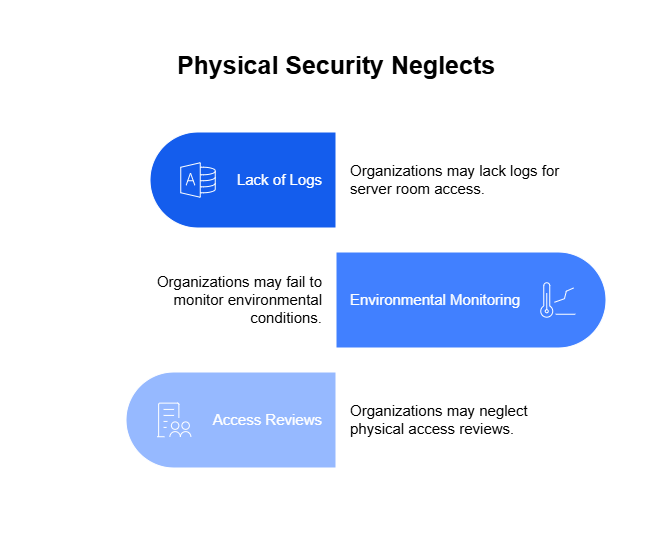
Unmonitored Physical Infrastructure
In the rush to secure cloud services, physical assets are sometimes forgotten. Organizations may lack logs for server room access, fail to monitor environmental conditions, or neglect physical access reviews.
Compliance frameworks like SOC 2 and ISO 27001 treat physical security as a core requirement. If your cameras don’t record, your logs are incomplete, or your server room lacks proper access control, you may pass digital audits but fail the physical ones.
Lack of Unified Logging and Monitoring
A typical hybrid setup generates logs from firewalls, VMs, cloud services, SaaS applications, and physical infrastructure. Without a central strategy to aggregate and correlate this data, it’s difficult to detect threats or prove control effectiveness.
Auditors expect complete, searchable logs for administrative actions, access attempts, and system changes. Fragmented or missing logs compromise your ability to investigate incidents or demonstrate compliance.
Manual Evidence Collection and Tracking
Many teams still manage compliance using spreadsheets, file folders, and screenshots. While this might suffice in small environments, it quickly breaks down at scale. Hybrid infrastructures demand automation to track changes, collect evidence, and ensure version control.
Manual workflows also create inconsistencies. Audit evidence may be outdated, misaligned, or hard to trace back to specific systems—especially when responsibilities are distributed across teams.
Outdated Policies and Documentation
Security policies often lag behind infrastructure changes. New cloud services or architectural shifts go live, but corresponding policies aren’t updated. This leads to gaps in coverage—and audit findings even when the right technical controls are in place.
Auditors don’t just want working systems—they want proof that your controls are governed by documented, reviewed, and approved policies. If your documentation is unclear, inconsistent, or outdated, your audit score will suffer.
Automating Data Center Compliance
To overcome the challenges of hybrid infrastructure, organizations must move beyond manual spreadsheets and ad hoc workflows. Automation is essential for scaling compliance, maintaining consistency, and reducing the human effort required to stay audit-ready. It transforms compliance from a point-in-time activity into a continuous, embedded practice.
Why Automate Compliance in Hybrid Data Centers
Hybrid environments bring together diverse components: on-prem servers, cloud-native workloads, SaaS platforms, and physical security systems. Each layer produces logs, requires configuration, and has its own set of controls. Trying to manage all of this manually is not only inefficient—it’s unsustainable.
Automation offers a better approach. It enforces controls programmatically, monitors for drift in real time, and automatically collects the evidence needed to prove compliance. Most importantly, it reduces the risk of error, speeds up response times, and ensures nothing is missed when environments evolve or teams change.
What Can Be Automated
Many high-effort and high-risk tasks are ideal candidates for automation:
- Access Reviews: Schedule and track user access certifications across systems, ensuring least-privilege is maintained.
- Evidence Collection: Automatically gather logs, screenshots, and system configurations into a centralized evidence repository.
- Policy Enforcement: Use infrastructure-as-code tools (e.g., Terraform, Ansible, Puppet) to standardize configurations and enforce security baselines.
- Alerting and Remediation: Detect violations such as disabled encryption or unauthorized access and trigger alerts or auto-remediation.
- Audit Reporting: Generate real-time dashboards and exportable reports that align with specific frameworks like SOC 2, ISO 27001, or PCI DSS.
With automation in place, your team can move from reactive compliance prep to a proactive model of continuous assurance.
Framework for Continuous Compliance
Automation is just one part of the solution. To build long-term resilience, organizations must adopt a compliance framework that operates continuously, not just during audits. Continuous compliance means embedding controls, reviews, and accountability into daily operations—so your hybrid data center is always secure, always compliant, and always audit-ready.
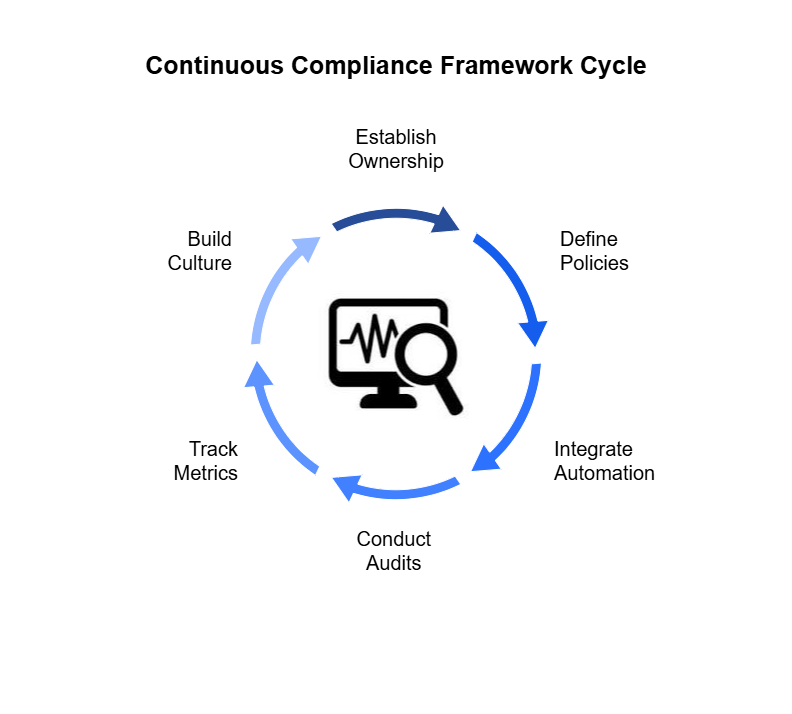
Here’s how to establish that framework in a way that supports growth, governance, and agility.
1. Establish Ownership and Governance
Every control needs an owner. Without clear accountability, gaps go unaddressed and audit prep turns into guesswork. Use a RACI matrix to assign responsibility for key domains like identity management, physical security, infrastructure hardening, and incident response.
In hybrid environments, this often involves multiple teams—cloud operations, data center facilities, DevSecOps, and compliance or GRC. Appoint a program lead to coordinate across functions and serve as the point person for external auditors.
2. Define Control Objectives and Policies
Strong policies are the foundation of strong controls. Define what must be protected, who has access, how activity is monitored, and what remediation looks like. Align each policy to your target frameworks (e.g., SOC 2, ISO 27001).
Make sure your policies reflect your hybrid architecture. For example, if you use a mix of cloud IAM and on-prem Active Directory, your access control policy should specify how they are synchronized and reviewed.
Schedule regular policy reviews—at least annually, or whenever major system or business changes occur.
3. Integrate Automation and Monitoring
Use automation to keep controls enforced and logs flowing into your monitoring systems. Combine SIEM platforms with cloud-native tools (e.g., AWS Config, Azure Policy) and DCIM integrations for a unified view of compliance posture.
Real-time alerting for drift, anomalies, or misconfigurations lets teams respond quickly—before an issue becomes an incident or an audit finding.
4. Conduct Internal Audits and Spot Checks
Don’t wait for external audits. Schedule quarterly or monthly internal reviews of your most critical controls. Perform access reviews, test incident response plans, and conduct tabletop exercises with key stakeholders.
Mock audits are especially useful. They surface weak documentation, outdated policies, or missing logs before an actual audit exposes them.
5. Track Metrics and KPIs
Use metrics to measure how well your compliance program is functioning. Common KPIs include:
- Mean time to detect and resolve compliance violations
- Percentage of controls automated
- Number of overdue access reviews or policy updates
- Time to generate evidence for auditor requests
Tracking these indicators gives you visibility into program maturity and helps justify further investment in tooling and training.
6. Build a Culture of Accountability
Technology alone doesn’t ensure compliance—people do. Train staff on acceptable use, data handling, and reporting procedures. Encourage proactive feedback and create open channels to report violations or improvement opportunities.
Foster a culture where compliance isn’t seen as overhead, but as a shared responsibility that protects the organization, its customers, and its data.
When you combine ownership, clear policies, automation, ongoing monitoring, and a culture of accountability, compliance becomes part of your daily rhythm—not a scramble when the auditor arrives.
Actionable Checklist — Data Center Security and Compliance in Hybrid Environments
To put the strategies from this guide into action, use the following checklist to assess your current posture, identify gaps, and track your progress toward a secure and compliant hybrid data center. These steps reflect best practices across governance, technical controls, automation, and culture.
🔹 Governance and Ownership
Identify relevant compliance frameworks (e.g., SOC 2, ISO 27001, NIST 800-53)
Define control ownership across IT, security, DevOps, and facilities
Appoint a compliance lead or GRC officer
Create and maintain a RACI matrix for all major control domains
🔹 Policy Development
Draft or update core policies (access control, encryption, incident response, etc.)
Ensure policy coverage across both on-premises and cloud environments
Schedule regular policy reviews (annually or post-infrastructure changes)
🔹 Physical and Environmental Controls
Implement access control systems (e.g., biometrics, badge readers)
Maintain and review access logs and visitor records
Deploy environmental monitoring (e.g., HVAC, fire suppression, UPS)
Schedule and document routine facility inspections
🔹 Technical Security Controls
Enforce least privilege and MFA across systems
Segment networks and apply boundary protections (firewalls, IDS/IPS)
Encrypt sensitive data both at rest and in transit
Centralize and audit all administrative and user activity logs
🔹 Automation and Monitoring
Use SIEM tools to aggregate logs from cloud and on-prem systems
Set up real-time alerts for security incidents and policy violations
Automate evidence collection for audits
Implement compliance automation platforms
🔹 Compliance Maintenance
Create and maintain a control mapping matrix
Perform internal audits or spot checks quarterly
Track key compliance KPIs (e.g., time to produce audit evidence)
Maintain documentation version control and audit trails
🔹 Culture and Training
Deliver annual compliance and security training to all employees
Include incident response, data handling, and acceptable use training
Encourage open feedback and anonymous reporting of violations
This checklist is designed to evolve with your infrastructure. Revisit it regularly as you adopt new technologies, enter new markets, or face new compliance obligations.
By following these steps, your organization can transition from reactive audits to continuous compliance—supporting both business growth and long-term resilience.
Conclusion
As hybrid data centers become the operational backbone of modern enterprises, securing them—and keeping them compliant—is no longer optional. The complexity of managing both physical and virtual infrastructure demands more than reactive fixes and point-in-time audits. It calls for a strategic, integrated approach that combines strong controls, clear policies, smart automation, and a culture of accountability.
Compliance isn’t just about passing audits. It’s about earning trust, demonstrating operational maturity, and reducing risk in an increasingly interconnected world. By embedding compliance into the fabric of your hybrid data center operations, you set your organization up for long-term security, scalability, and success.
Start small if needed. Automate a few controls. Clean up your access logs. Review one policy a week. But stay consistent. Because in a hybrid world, compliance isn’t a destination—it’s a discipline.
