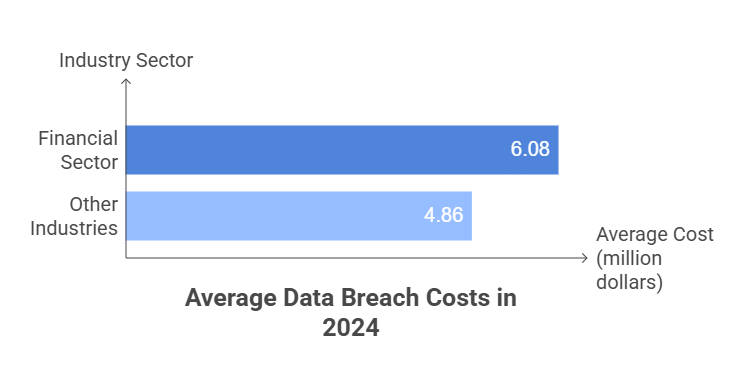
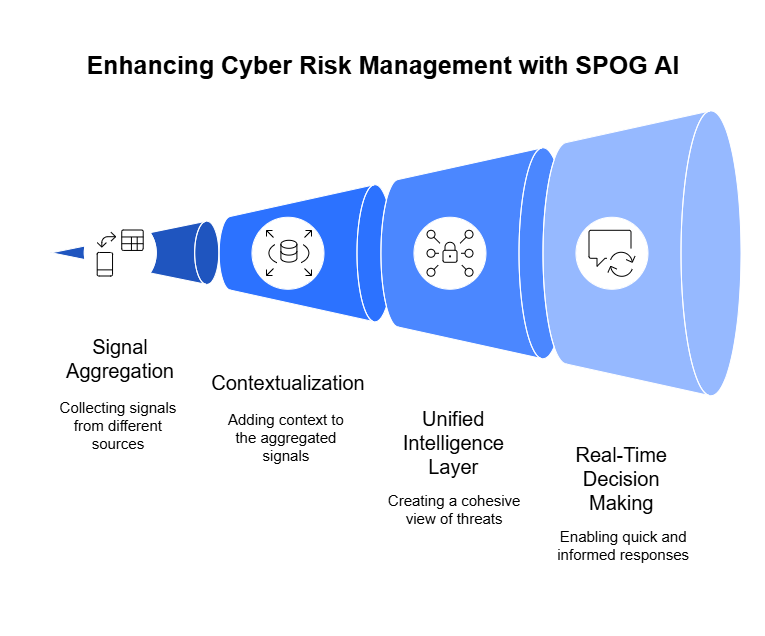
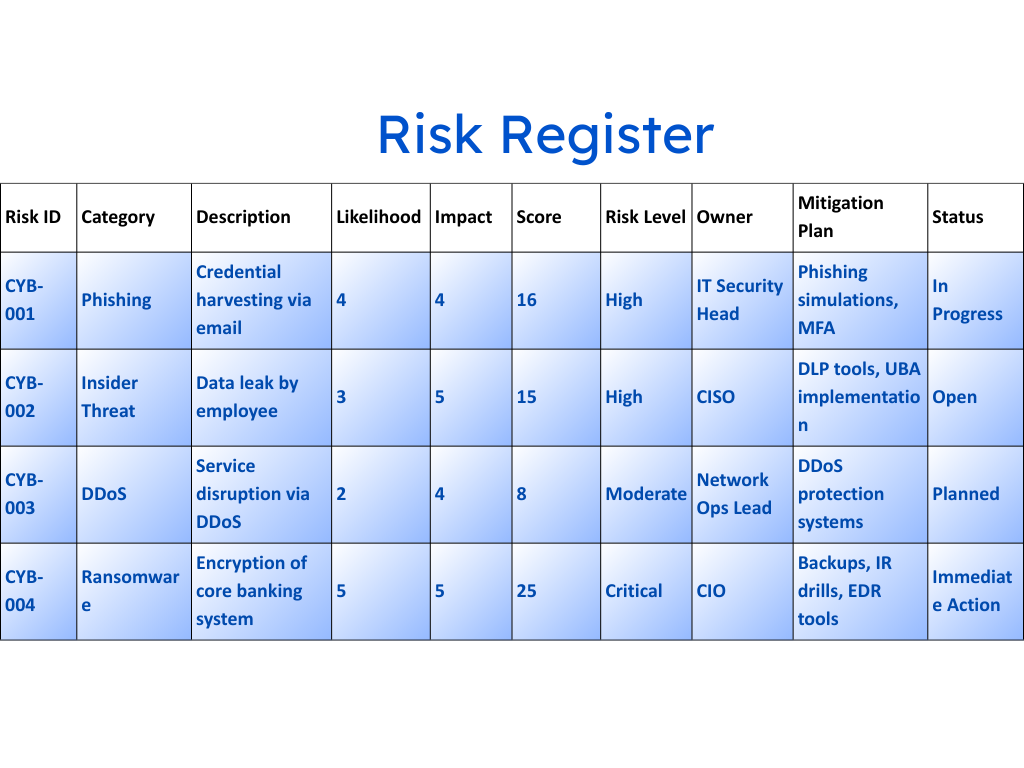
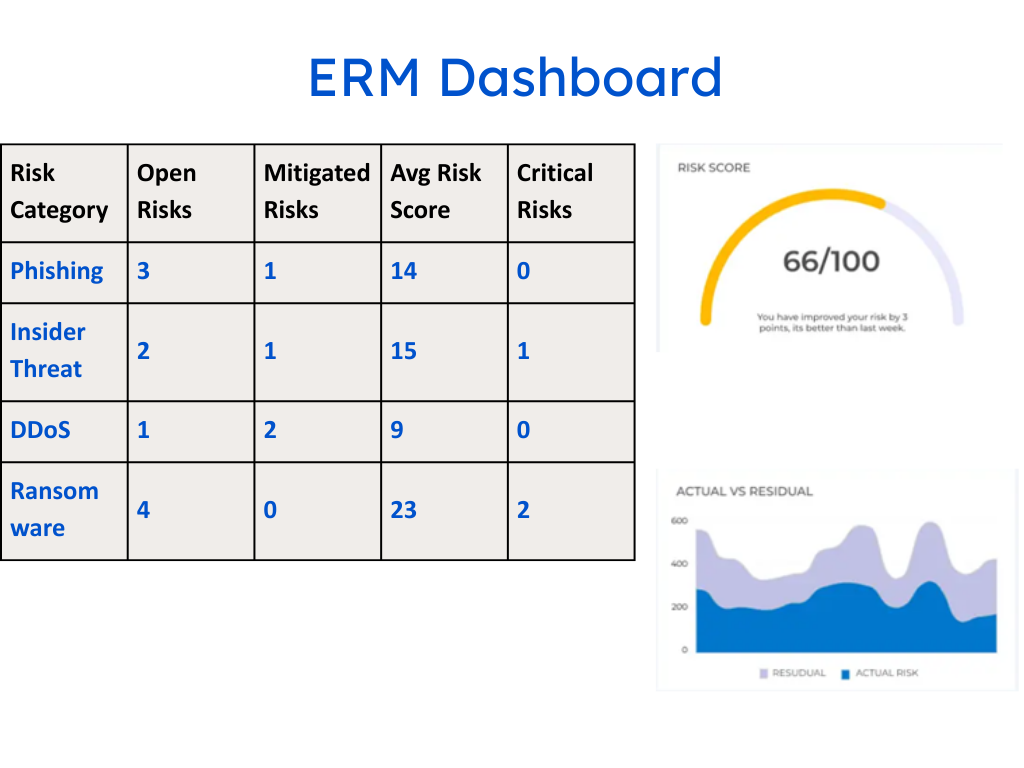
For years, the risk register has been a key tool in governance, risk, and compliance (GRC) programs. But in most organizations, it still sits in spreadsheets or static forms that capture only a single moment. By the time a team reviews it—whether in a quarterly meeting or during an annual audit—the reality on the ground has already shifted.
Today’s digital world moves too fast for this old model. Cloud services launch in hours, assets change daily, and new threats appear by the minute. A register that doesn’t adapt creates blind spots. It gives the appearance of control but offers little evidence that controls are working or risks are managed.
This leaves security leaders in a tough spot. They’re forced to make decisions with outdated data, often relying on assumptions instead of facts. The problem isn’t the register itself—it’s the way we manage it. To stay relevant, the risk register must evolve into something more dynamic, more connected, and more alive.
Why GRC Risk Registers Are Stuck in the Past?
Manual risk registers were built for a slower world—when changes were monthly,
assets were static, and compliance was once a year. Today’s digital environments
are far too dynamic for that model.
Today, businesses run in cloud environments where new servers and applications are created and retired daily. Employees connect from anywhere, often on unmanaged devices. Attackers use automation to probe for weaknesses by the hour, not the quarter.
This speed has outgrown the static tools many organizations still rely on. A spreadsheet might capture a snapshot, but it cannot reflect the constant change of real operations. The result is a dangerous lag: risks evolve, but the register remains frozen in time.
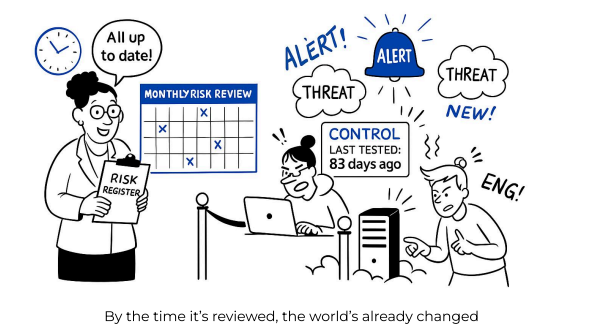
Here’s where static risk management breaks down:
- They Don’t Reflect Change: Risks are often recorded once and rarely updated. Meanwhile, controls drift, threats emerge, and asset inventories shift—yet the register remains frozen in time.
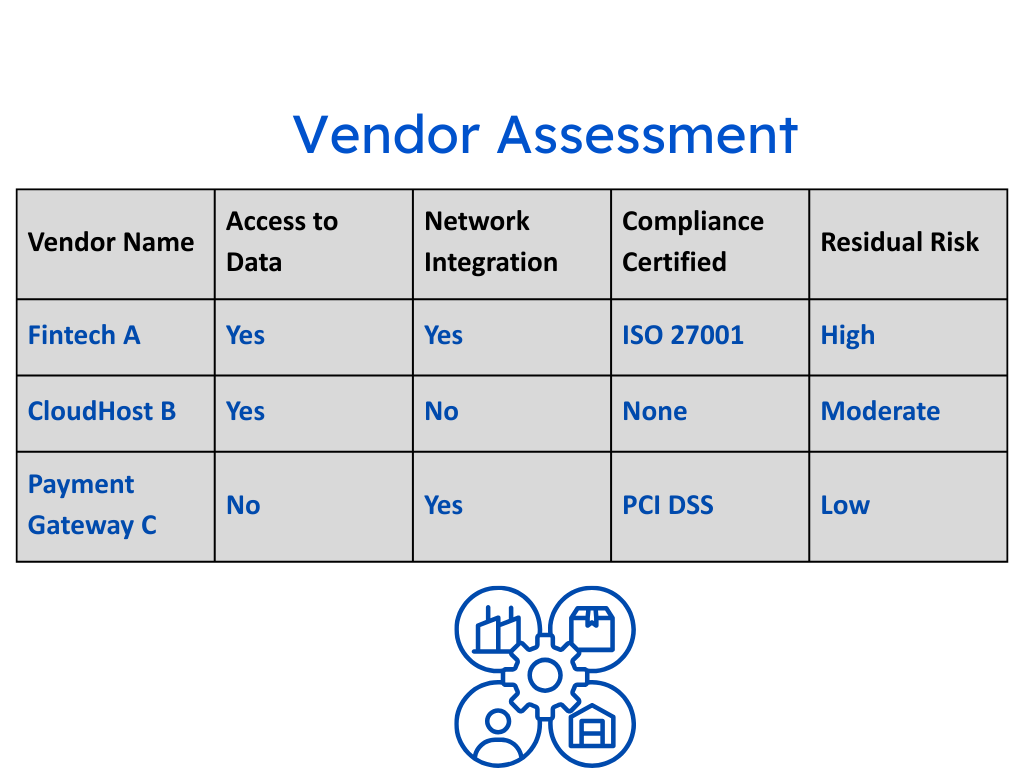
- No Control Context: Registers log risks but lack real-world evidence. Is the control enforced? Is it working? Who owns the fix? These answers often live outside the register in siloed tools.
- No Residual Risk Visibility: Without up-to-date control effectiveness, risk ratings are assumptions. Residual risk, the risk that remains is unknown, making prioritization guesswork.
- Overhead Without Insight: Manual reviews, recurring risk committee updates, and audit cycles generate administrative load, but don’t improve actual security posture.
Static risk registers create the illusion of control without the evidence or agility needed in today’s dynamic environments.
The Rise of Living Risk Registers
If static registers fall short, what takes their place? The answer is a new approach: the living risk register. Unlike spreadsheets that capture a frozen moment, a living register evolves alongside the environment it monitors.
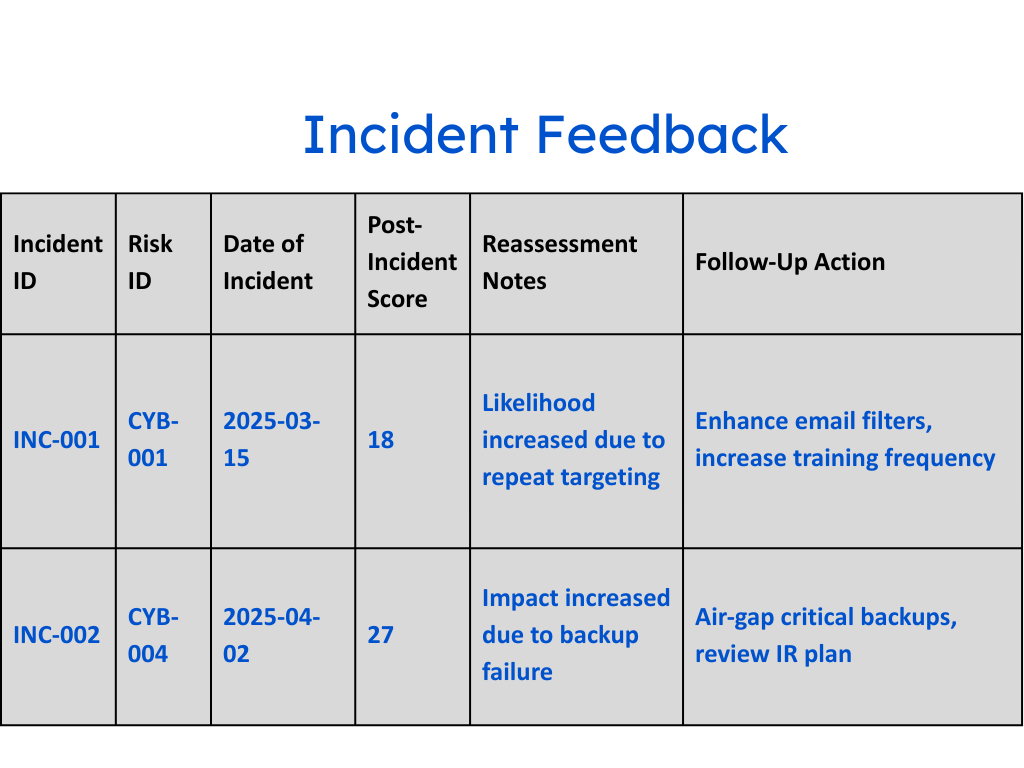
A living register connects directly to the systems and controls it tracks. Instead of waiting for a manual update, it reflects real-time changes—whether a control is failing, a new asset appears, or a vulnerability emerges. Risks aren’t just listed; they’re tied to evidence, context, and ownership.
This shift is more than technical. It changes the role of the register itself. Once seen as a tool for audits and reporting, the register becomes a driver of ongoing assurance. It’s not only about documenting what could go wrong, but about proving what’s under control—and identifying what still needs action.
In short, a living register bridges the gap between risk on paper and risk in practice. It gives leaders a clearer, more trustworthy view of their true security posture, every day.

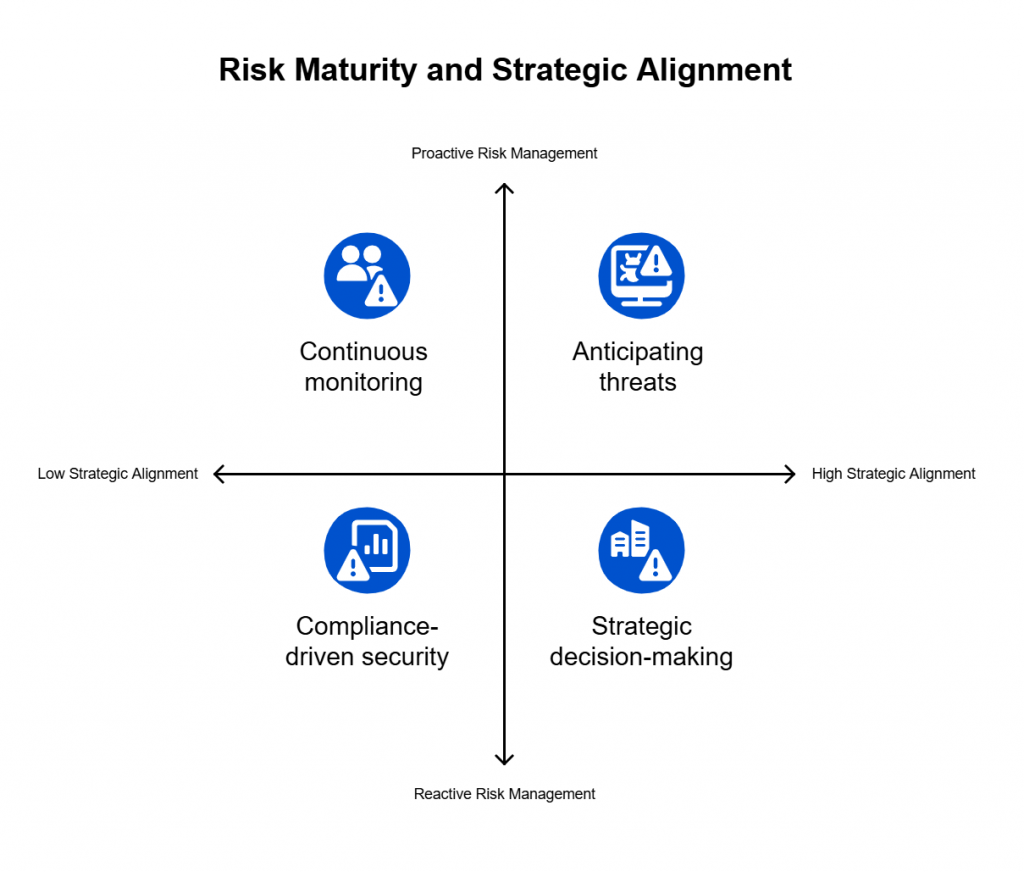
Core Principles of a Living Register
A living risk register isn’t just a digital version of a spreadsheet. It works because it follows a few key principles that make it more responsive, reliable, and actionable in fast-changing environments:
1. Continuous Visibility
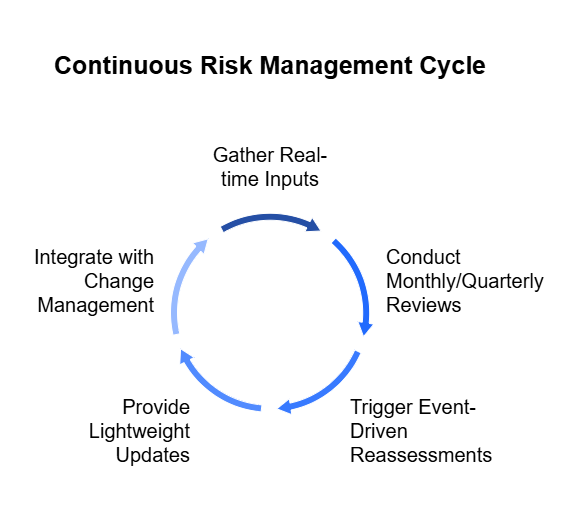
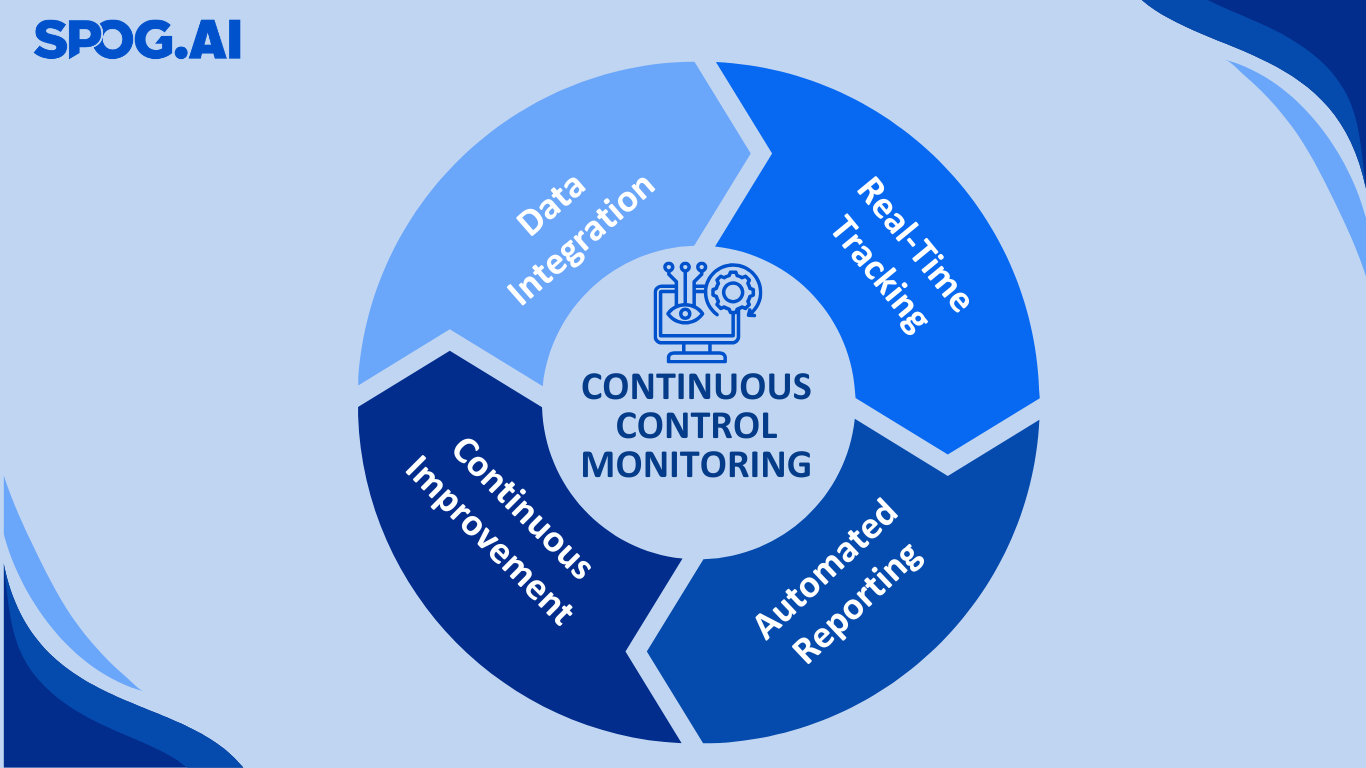
Traditional registers only capture risk at a point in time—often during quarterly reviews or annual audits. A living register, by contrast, connects to systems directly. If a firewall rule changes, an endpoint drifts from baseline, or a vulnerability is discovered, the register updates immediately. This ensures leaders make decisions based on today’s reality, not last quarter’s assumptions.
2. Contextual Accountability
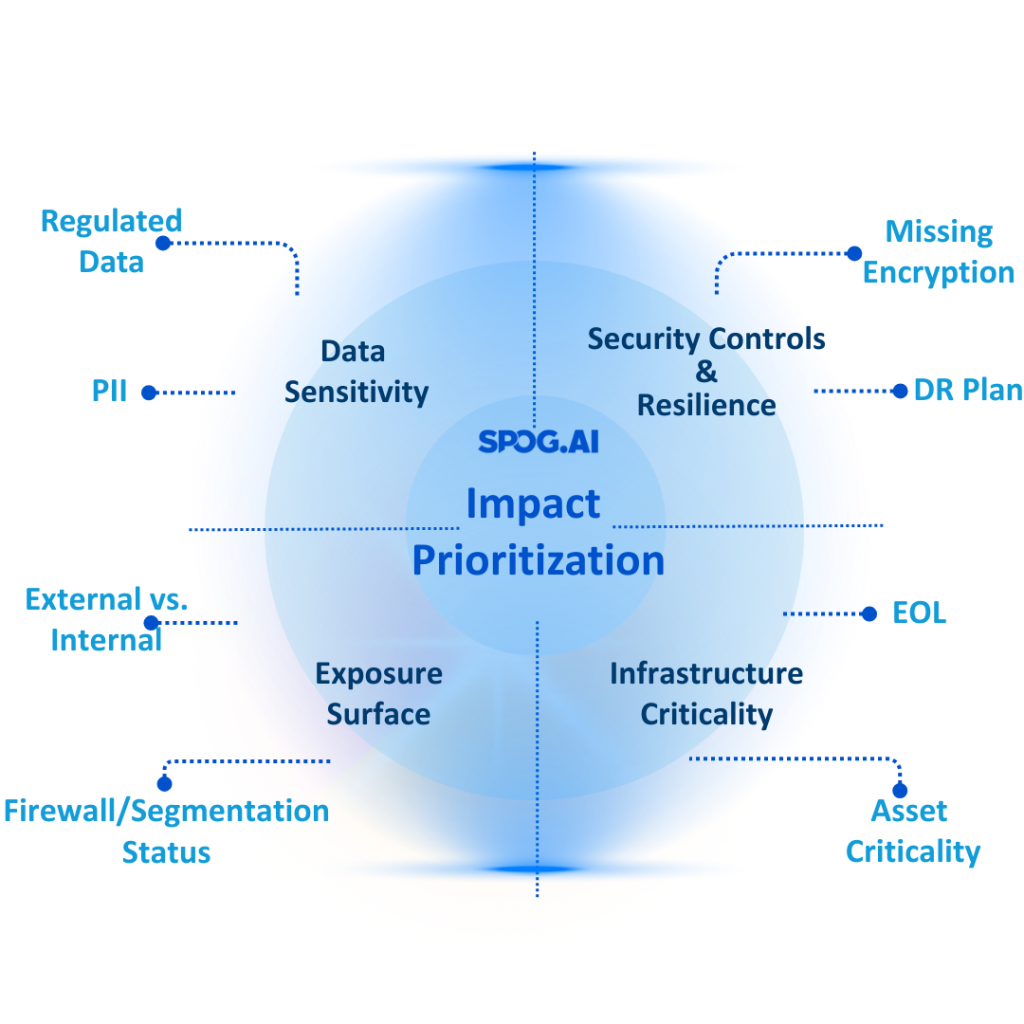
Risks on their own don’t mean much without context. A living register links each risk to the assets it affects, the controls in place, and the person responsible for managing it. For example, if a cloud storage bucket is exposed, the register doesn’t just note “misconfiguration.” It shows which business unit owns it, whether encryption is enforced, and who is accountable for remediation. This prevents risks from sitting as abstract entries without clear ownership.
3. Dynamic Workflows
Static forms can’t reflect the way organizations actually work. A living register adapts to real-world processes. It can escalate issues automatically if they aren’t addressed within a defined timeline, route updates to the right team, or trigger approvals when a risk reaches a certain level. This turns governance from a periodic meeting exercise into a continuous flow of accountability, making it harder for risks to stall.
4. Action Over Documentation
In many organizations, the register is little more than a logbook—something reviewed occasionally to satisfy auditors. A living register shifts the focus to action. Each risk has a lifecycle, moving from identification to assessment, remediation, and closure, with a record of evidence along the way. This makes the register not just a catalog of problems, but a tool for solving them. It transforms compliance work from “checking the box” into proving ongoing assurance.
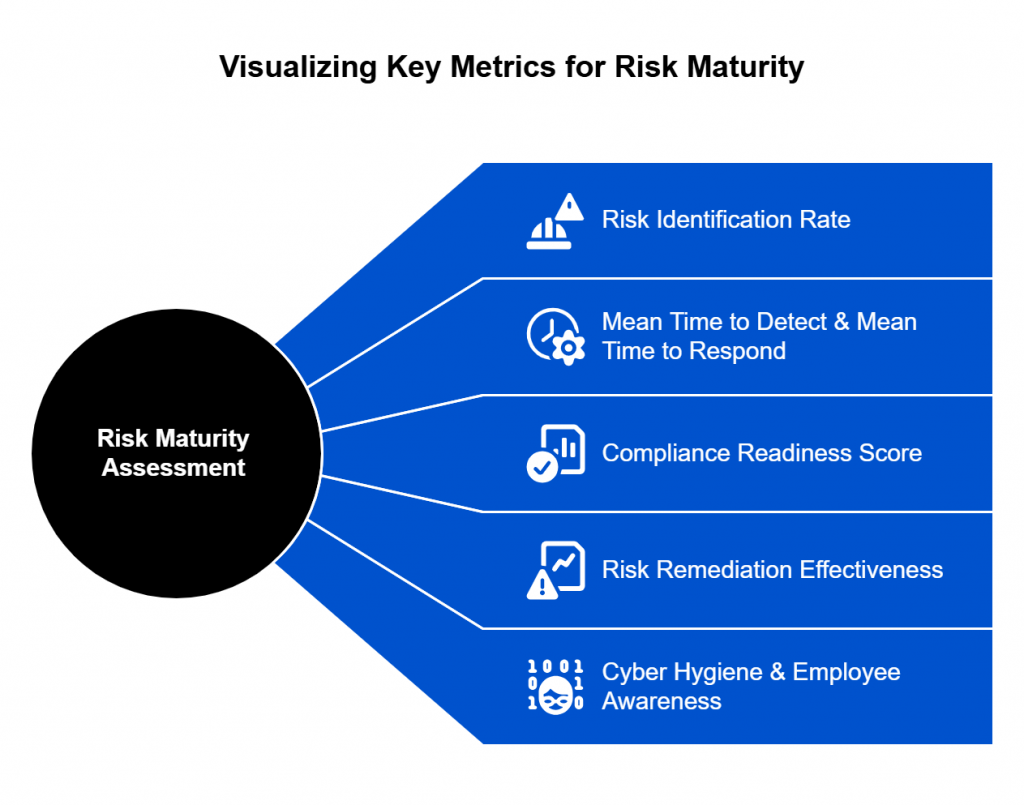
What Benefits Do Living Risk Registers Deliver Beyond Compliance?
A living risk register does more than improve how risks are tracked—it changes how the organization operates. The advantages extend well past regulatory checklists, shaping culture, efficiency, and trust.
1. Improved Cross-Team Collaboration
Static registers often sit with GRC teams, out of reach for security, IT, or business units. A living register breaks down those silos by providing a shared source of truth. Risk data becomes visible across teams, allowing IT to see how their fixes affect compliance, or business leaders to understand how risk decisions tie back to operations. This shared visibility reduces finger-pointing and fosters cooperation.
2. Better Use of Resources
When risks are grounded in live evidence, teams spend less time chasing false alarms or working on low-priority issues. Effort is directed toward the risks that actually matter. This doesn’t just strengthen security—it also saves money and time, allowing scarce resources to be invested in innovation rather than administrative work.
3. Stronger Executive Confidence
Boards and executives want clarity, not technical jargon. A living register offers a clearer picture of the organization’s true risk posture, expressed in terms of impact on business outcomes. This transparency builds trust and makes it easier for leaders to support investments in security, because they see the direct connection between risks and organizational goals.
4. Readiness for the Unexpected
Regulations change. Business models shift. New markets bring new risks. A living register helps organizations adapt faster to these changes because it isn’t locked to rigid templates or static fields. By customizing workflows and taxonomies, companies can adjust their risk lens without overhauling the entire system—keeping governance aligned with the business as it evolves.
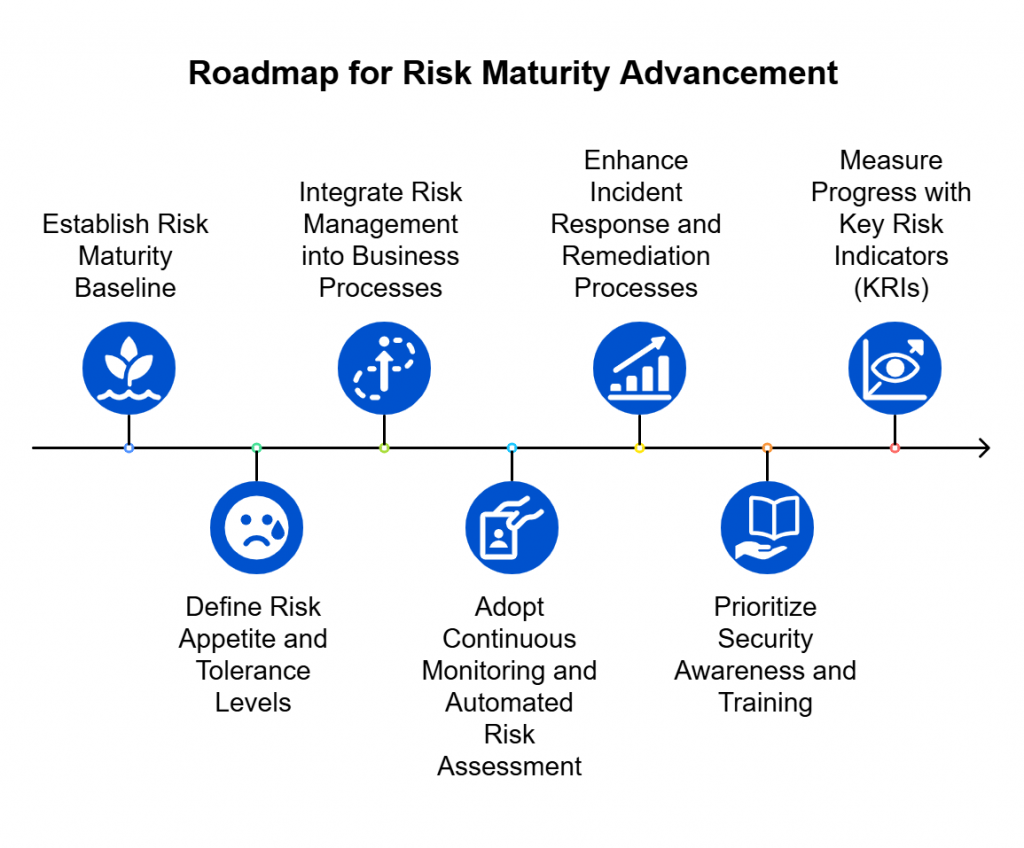
5. A Path to Continuous Maturity
Perhaps the most overlooked benefit is how a living register drives maturity over time. With every cycle, the system gathers more evidence, clarifies ownership, and strengthens workflows. Instead of resetting at each audit, the organization builds on its foundation, making each year more efficient than the last. Risk management becomes a continuous improvement loop rather than a stop-start exercise.
In these ways, the living risk register goes beyond compliance. It becomes a foundation for stronger culture, smarter strategy, and long-term resilience.
From Static Registers to a Living Risk Engine
SPOG.AI transforms the risk register from a passive spreadsheet into a real-time,
living system that evolves with your environment. Instead of static snapshots, it
delivers dynamic, control-aware updates that reflect true risk posture as it shifts.
It doesn’t just list risks; it links them directly to the assets they affect, the controls in
place, and the teams responsible for mitigation, creating a continuous loop of
awareness, accountability, and action.

SPOG.AI Risk management capabilities include the following:
- Real-Time Control Ratings: Each risk is tied to controls monitored in real time. Control status working, drifting, or failing is automatically updated through telemetry, ensuringthat your register reflects ground truth, not assumptions
- Residual Risk Calculated Continuously: With accurate control ratings, SPOG.AI recalculates residual risk dynamically. As assets change, new threats emerge, or controls improve, your risk posture updates automatically per object, per domain.
- Custom Fields and Workflows: No two GRC programs are identical. SPOG.AI lets you define your own fields, tags, processes, and approval chains, whether you follow ISO 27005, FAIR, NIST RMF, or your own hybrid model.
- From Documentation to Action: Say goodbye to disconnected Excel files. SPOG.AI gives security, IT, and compliance teams one place to collaborate on risk, rooted in real telemetry, with workflows that drive maturity, not just reporting.
Conclusion: From Illusion to Assurance
Risk registers were never meant to stay frozen on a page. In an environment where technology shifts daily and threats evolve by the hour, relying on static lists creates more risk than it reduces. Spreadsheets may satisfy an audit, but they don’t give leaders the clarity or confidence they need to act.
The future of governance and risk management lies in living registers—systems that move with the business, connect risks to evidence, and drive accountability across teams. These registers do more than track potential problems; they help organizations prove what’s under control, respond to change with agility, and strengthen trust at every level.
Moving from illusion to assurance means risk management is no longer a back-office chore. It becomes a source of clarity, maturity, and strength for the entire organization.