Introduction — The Performance of Protection
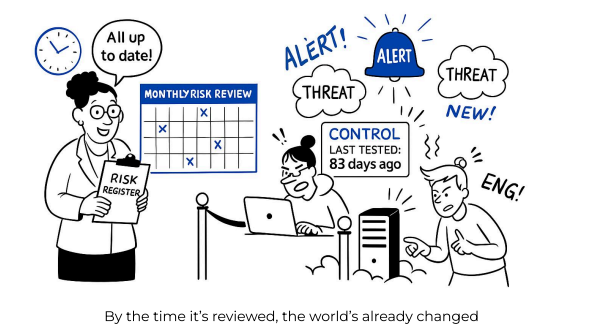
In too many organizations, risk management has become a performance rather than a practice. Every quarter, teams scramble to refresh risk registers, hold a few hurried meetings, and fill color-coded Excel sheets with whatever risks come to mind. The reports look polished. The compliance boxes get checked. The theater lights dim, and everyone applauds the show.
But behind the curtain, little has changed. The same vulnerabilities persist, the same gaps remain unaddressed, and the same uneasy feeling lingers: are we actually safer, or just better at pretending to be?
This is the uncomfortable truth of today’s risk landscape — much of risk management is process theater. It’s a system built to satisfy audits and maintain appearances, not to deliver confidence, visibility, or measurable reduction in risk.
Somewhere along the way, the “R” in GRC (Governance, Risk, and Compliance) became an afterthought — overshadowed by the endless pursuit of governance paperwork and compliance certifications.
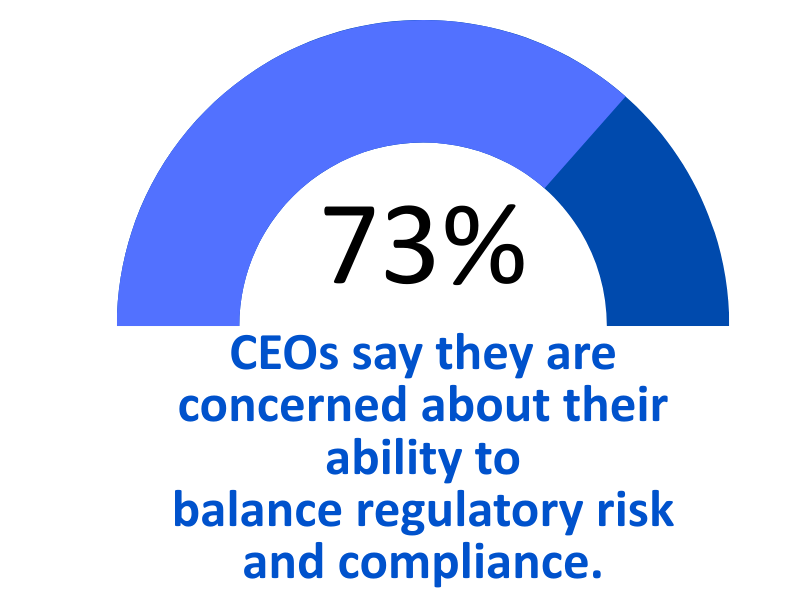
The result? Risk teams are overworked but under-impactful. CISOs walk into board meetings armed with data but lacking conviction. And organizations, despite layers of controls, still struggle to answer the simplest executive question:
“Are we really secure where it matters most?”
This article explores why risk management has drifted into performance mode — and, more importantly, how to bring it back to purpose. It’s time to rebuild our programs around continuous insight, contextual controls, and board-level confidence. Because risk management shouldn’t be a quarterly show — it should be a living system that tells us, in real time, how exposed we truly are.
How Risk Management may have Lost Its Way
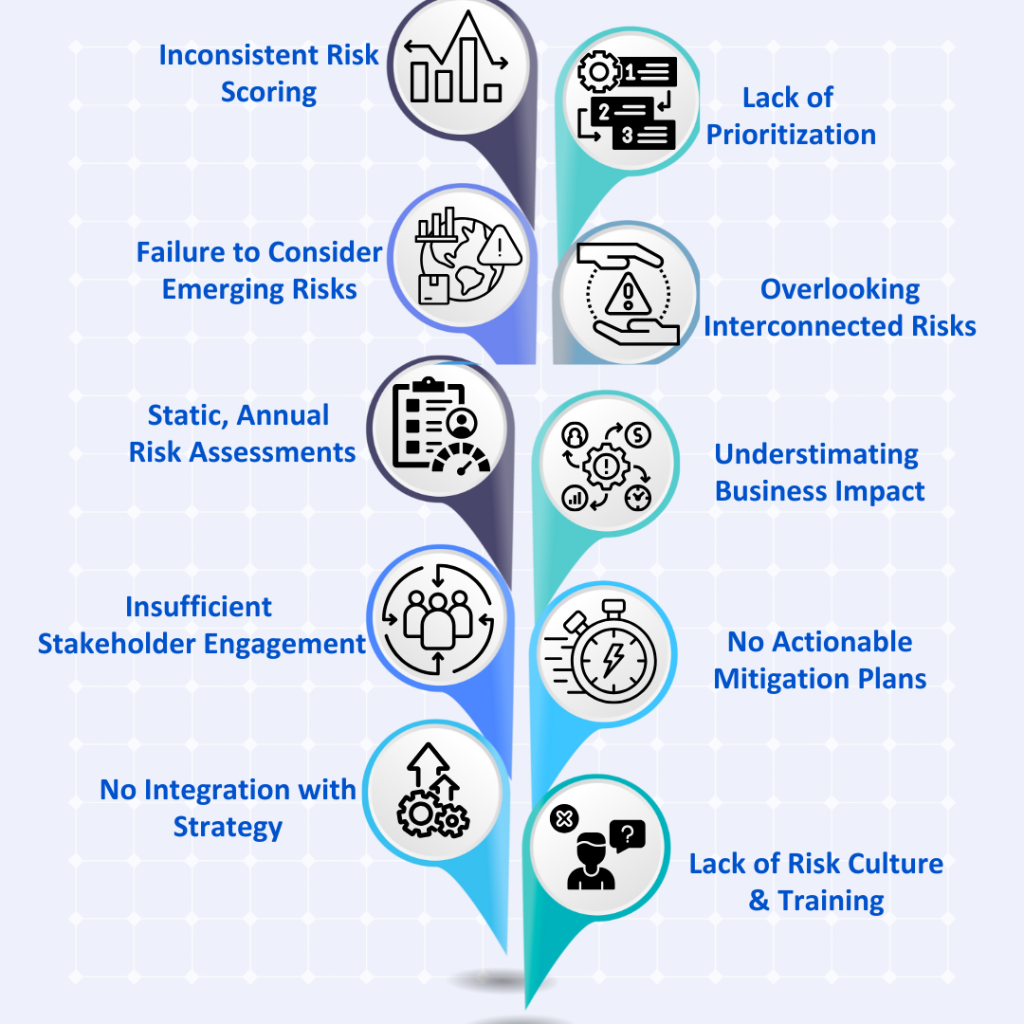
So how did a discipline meant to safeguard organizations from uncertainty turn into a ritual of spreadsheets, status updates, and staged compliance?
The short answer: we built our risk programs around appearances, not outcomes.
Let’s unpack the root causes.
The Compliance-First Mindset
For most companies, risk management didn’t evolve organically — it was born out of audit requirements. SOC 2, ISO 27001, NIST, PCI — frameworks that were designed to standardize trust ended up shaping how we think about risk itself.
Instead of asking, “What threatens our business today?”, teams ask, “What will the auditor want to see?”
The result is a compliance-first culture that equates passing an audit with being secure. But audit readiness is not risk readiness. Compliance is the floor, not the ceiling — yet most organizations stop there because it feels measurable, reportable, and “safe.”
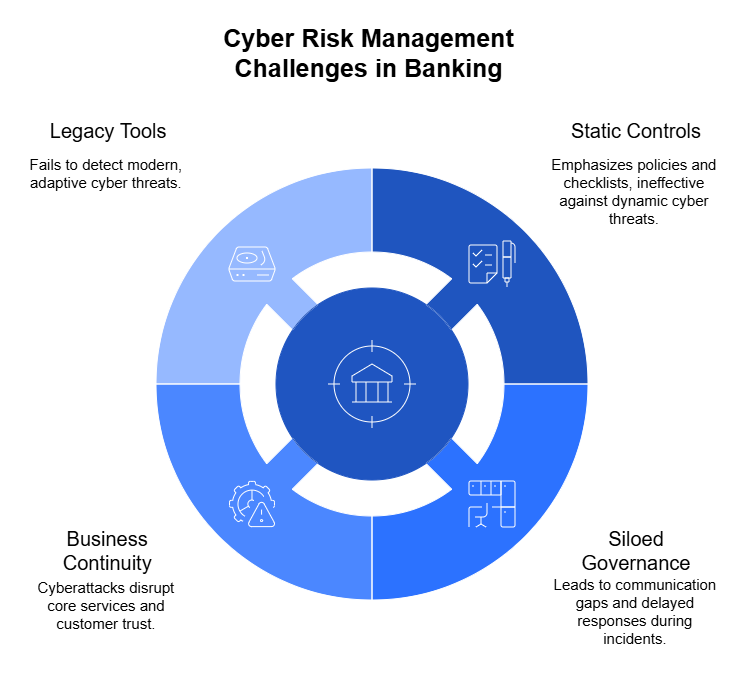
Static Tools for a Dynamic Problem
Modern risk moves at cloud speed; our processes do not.
Quarterly risk assessments, static Excel sheets, and one-off workshops cannot capture the pace of today’s threats.
Every control failure, every system change, every emerging vulnerability shifts your risk posture — yet most teams operate with snapshots frozen in time.
When risk is recalculated once every few months, it’s not a management system — it’s a scrapbook of old information.
Fragmented Ownership and Accountability
Another culprit: risk lives everywhere and nowhere at once.
Security owns some, compliance owns others, and the business owns the rest — each team interpreting “risk” in its own language.
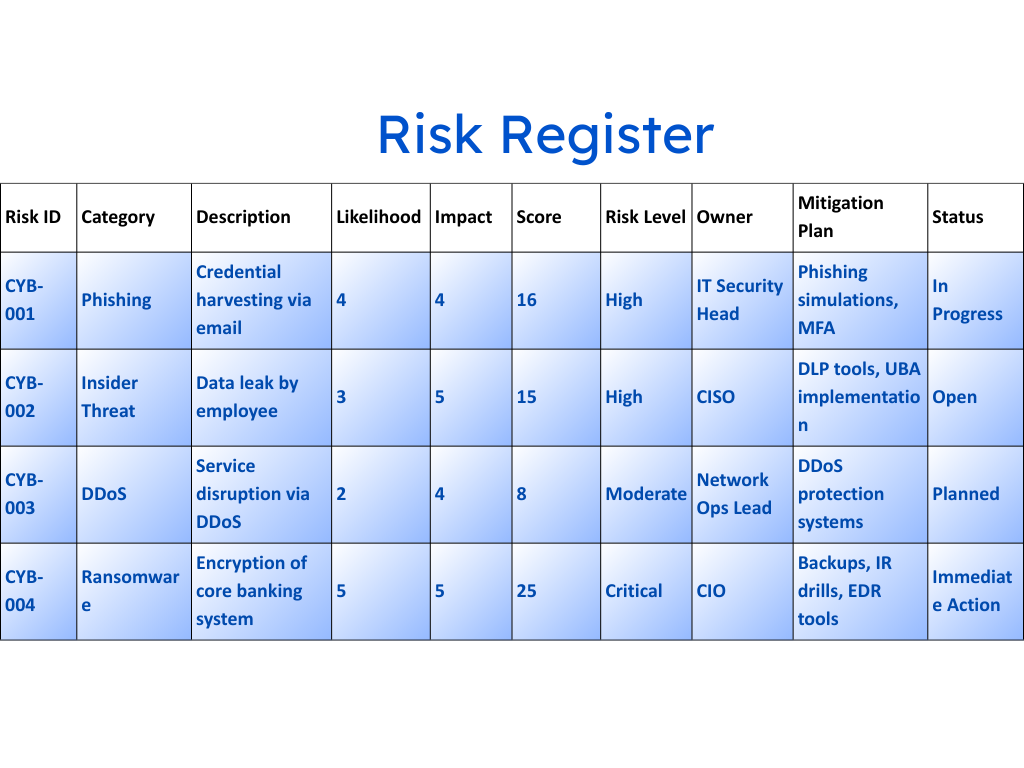
Without a unified view, risk management becomes a consensus exercise: people gather in a room, brainstorm risks from memory, and log them in a register that no one revisits.
What’s missing is ownership tied to outcomes — not just identifying risks, but continuously tracking whether they’re getting better or worse.
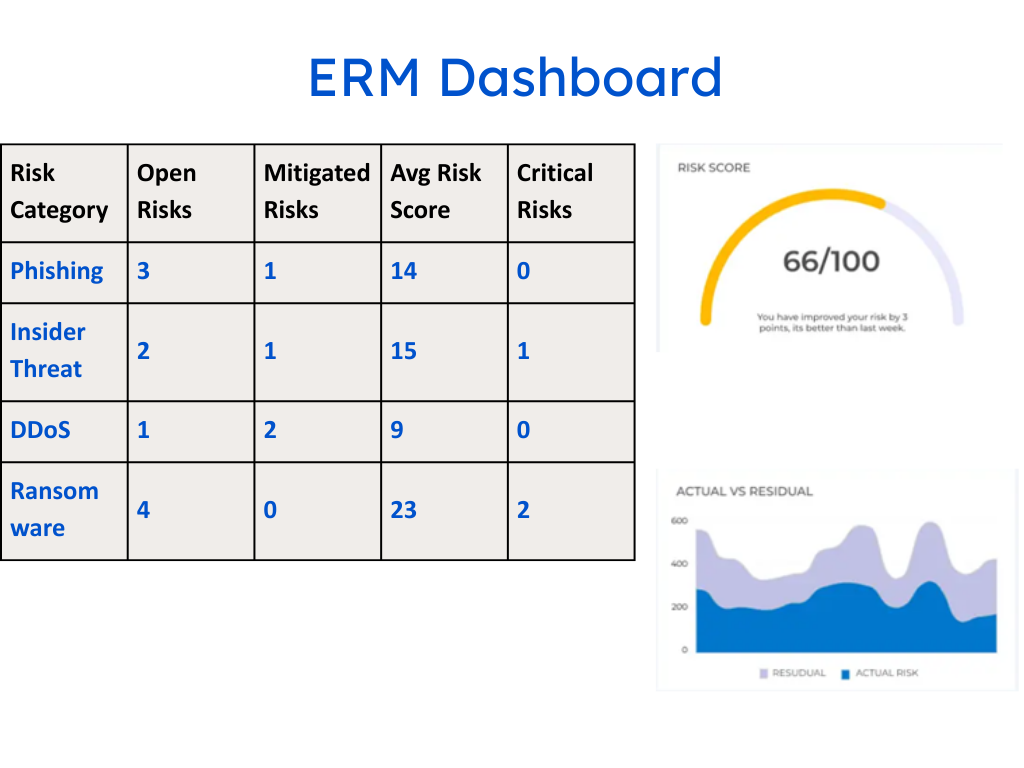
Metrics Without Meaning
Risk dashboards often look scientific: red, amber, and green boxes, “likelihood × impact” matrices, even probability scores with decimals. But let’s be honest — these numbers rarely mean what we think they do.
They’re subjective guesses wrapped in the illusion of precision.
What’s worse, they’re rarely connected to business impact.
When a CISO tells the board a risk score is “7.2,” the real question is, 7.2 compared to what?
Without context — revenue exposure, customer impact, downtime potential — the number is theater, not intelligence.
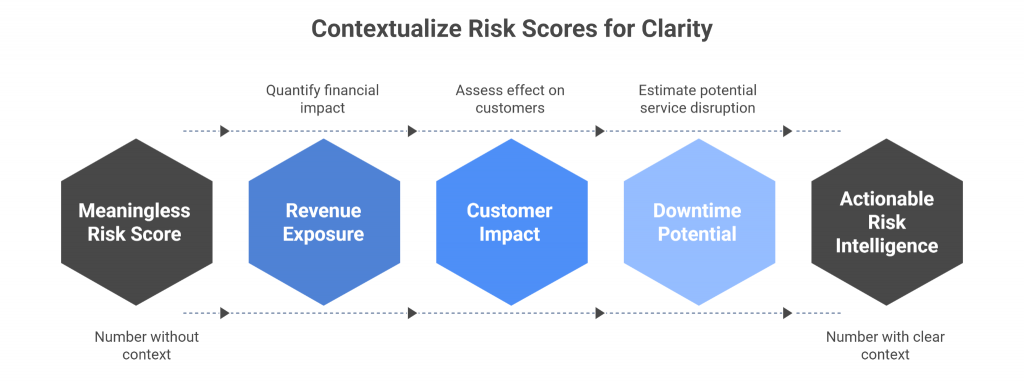
In summary, Risk management lost its way when it became more about documentation than decision-making.
We optimized for compliance over confidence, consistency over context, and process over progress.
But it doesn’t have to stay that way.
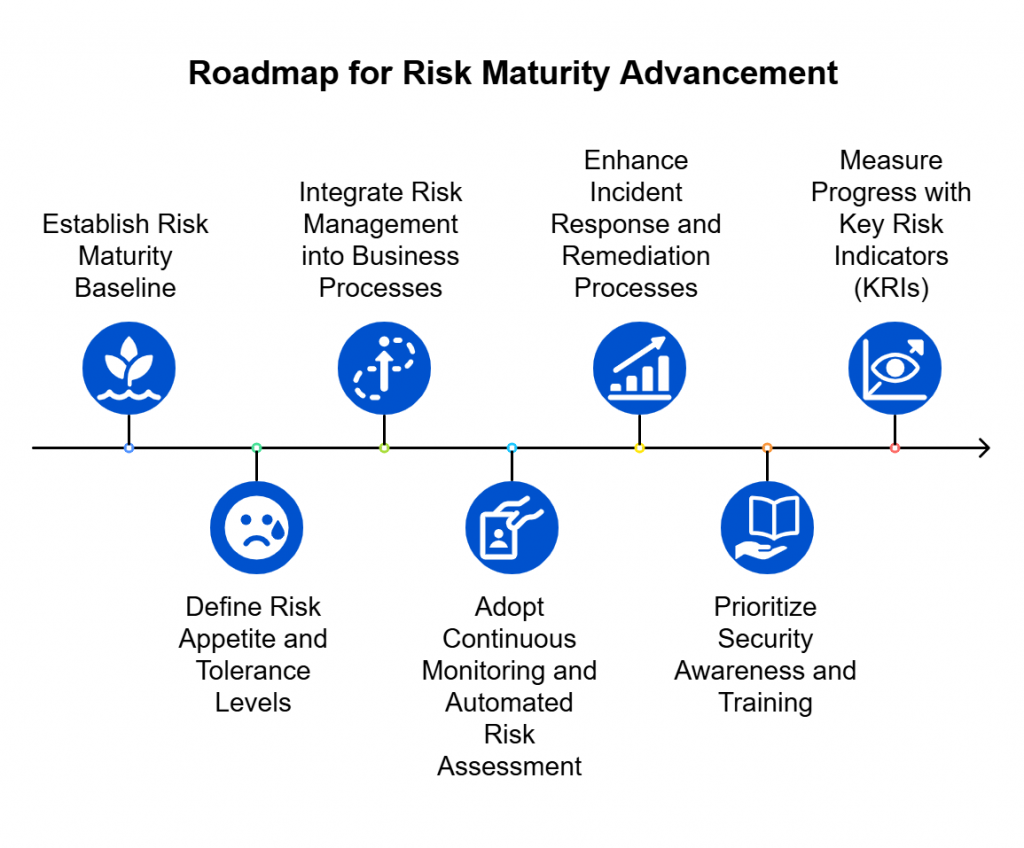
Putting the ‘R’ Back in GRC
If governance and compliance are the structure and scaffolding of a risk program, then risk is supposed to be its heartbeat — the element that keeps everything alive, relevant, and responsive. Yet in most organizations, that heartbeat has gone faint.
It’s time to put the “R” back in GRC — to rebuild our programs around risk as a dynamic, measurable, and continuously managed force.
Here’s what that transformation looks like.
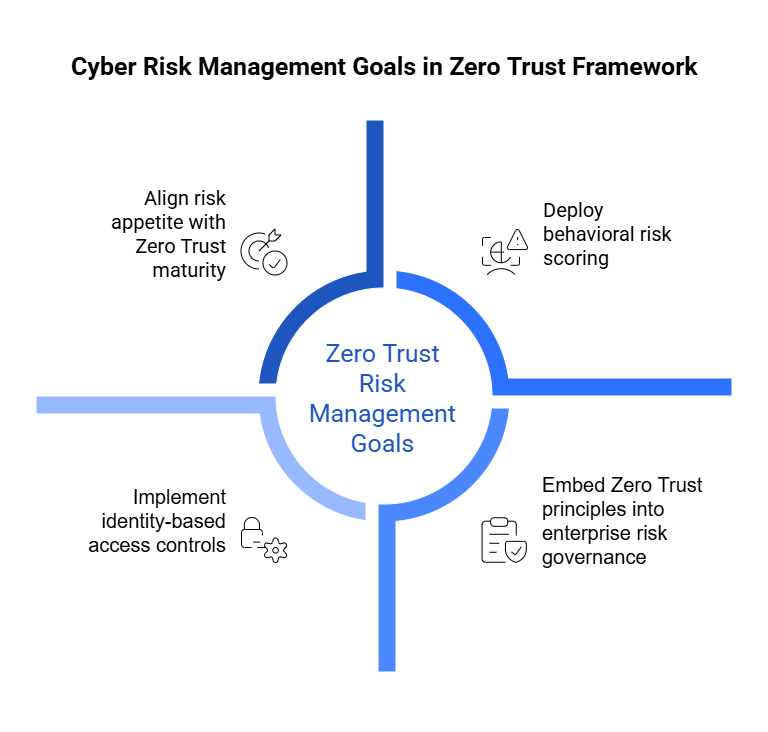
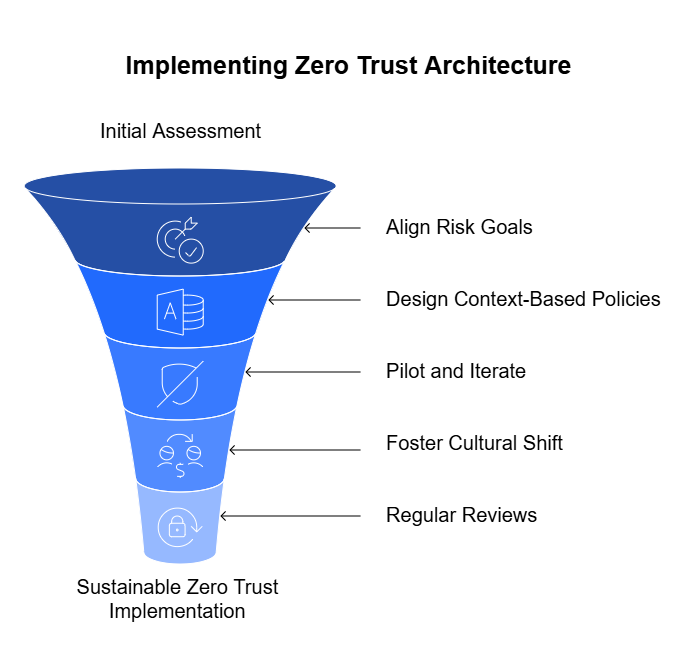
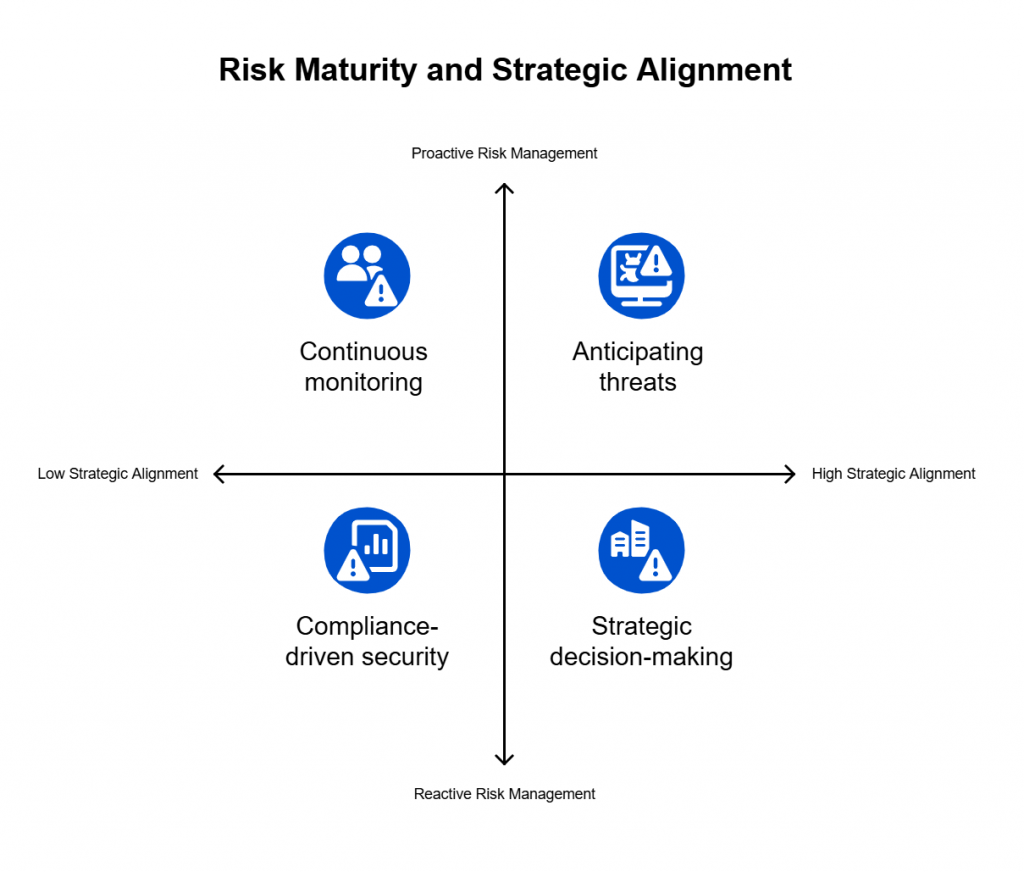
1. Reframe GRC Around Risk — Not Regulation
Governance and compliance should serve one purpose: to reduce risk.
Yet in many organizations, the equation is reversed — risk is treated as a side effect of compliance.
Re-centering GRC means flipping that logic.
Instead of starting with, “What controls do we need for SOC 2 or ISO?”, start with, “What risks could actually disrupt our business — and which controls mitigate them most effectively?”
When you lead with risk, compliance becomes a byproduct of good security practice, not the end goal.
It’s not about adding more controls; it’s about applying the right ones, for the right reasons, in the right context.
Audit readiness ≠ risk readiness.
True maturity is measured by visibility, not by certifications.
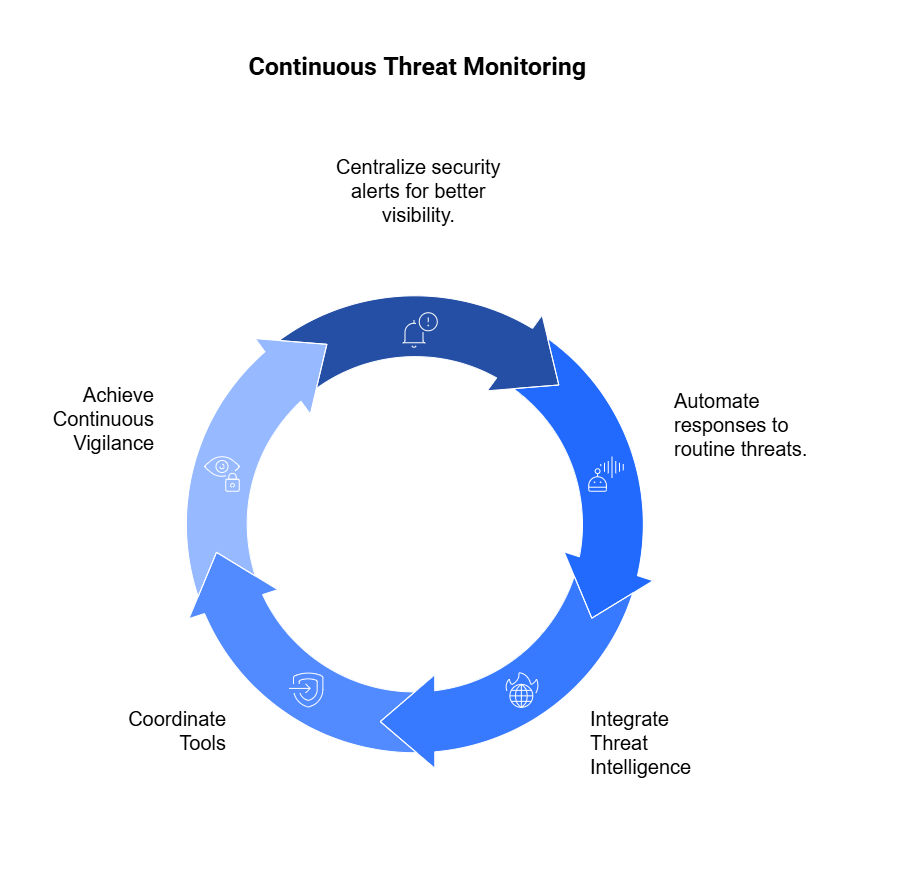
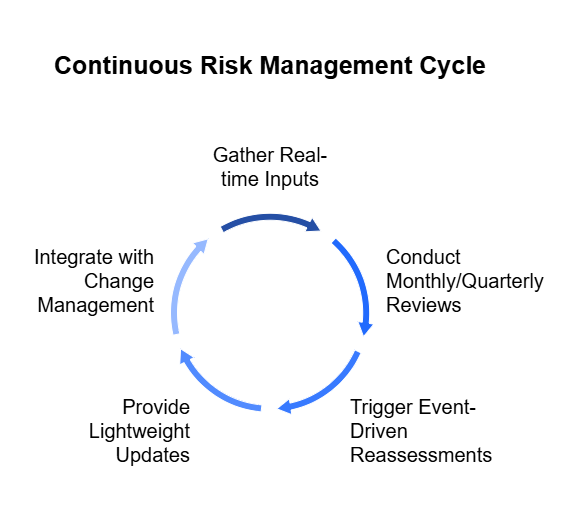
2. Make Risk Continuous
Quarterly assessments made sense when systems changed slowly.
Today, new integrations, vulnerabilities, and attack techniques emerge daily.
Risk management must evolve into a continuous process that keeps pace with change.
Continuous risk means:
- Automating control monitoring to detect drift or failure in real time.
- Ingesting operational data — incidents, patching cycles, alerts — to dynamically update risk posture.
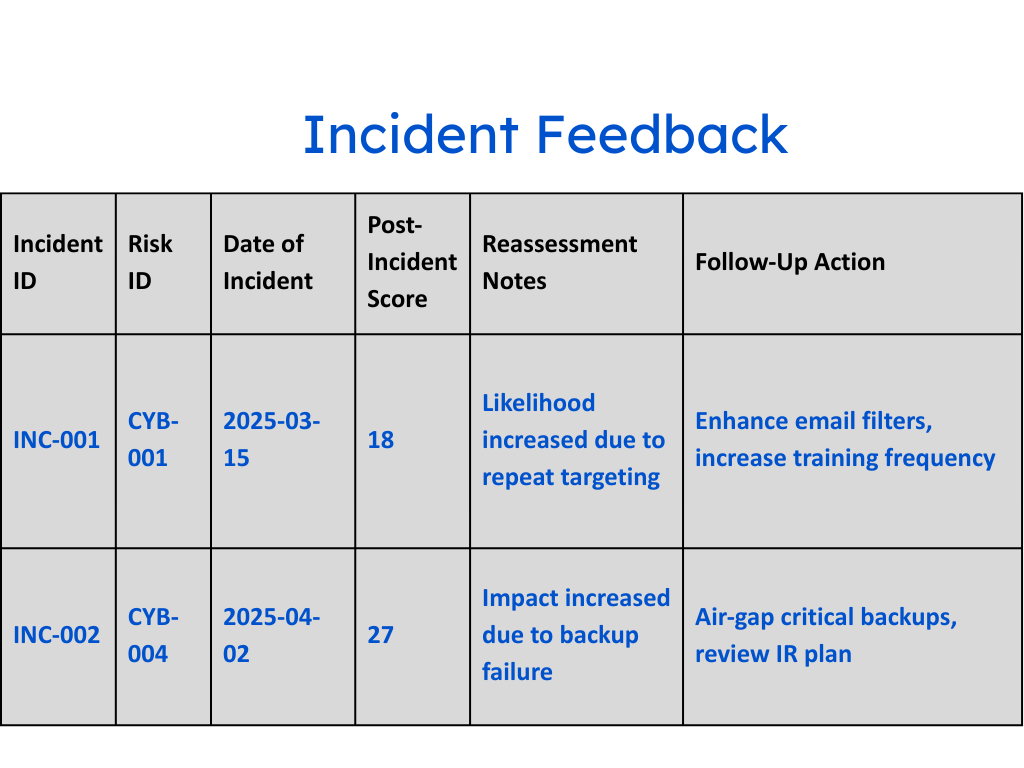
- Triggering reassessments automatically when something material changes.
This shift replaces static reporting with risk observability — the ability to see, measure, and respond to emerging threats as they happen.
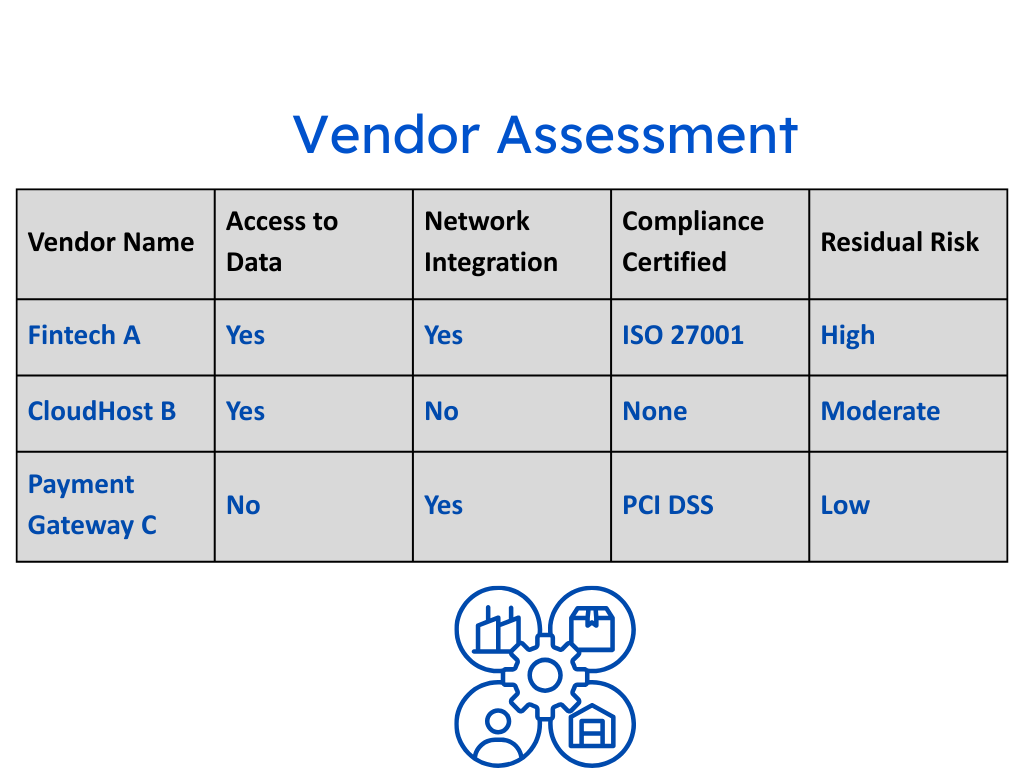
3. Add Context to Controls
A control that works for one organization may be irrelevant to another.
Think of it like the car analogy: putting on your seatbelt is a baseline, but adjusting the mirrors and seat to your height is what makes driving safe for you.
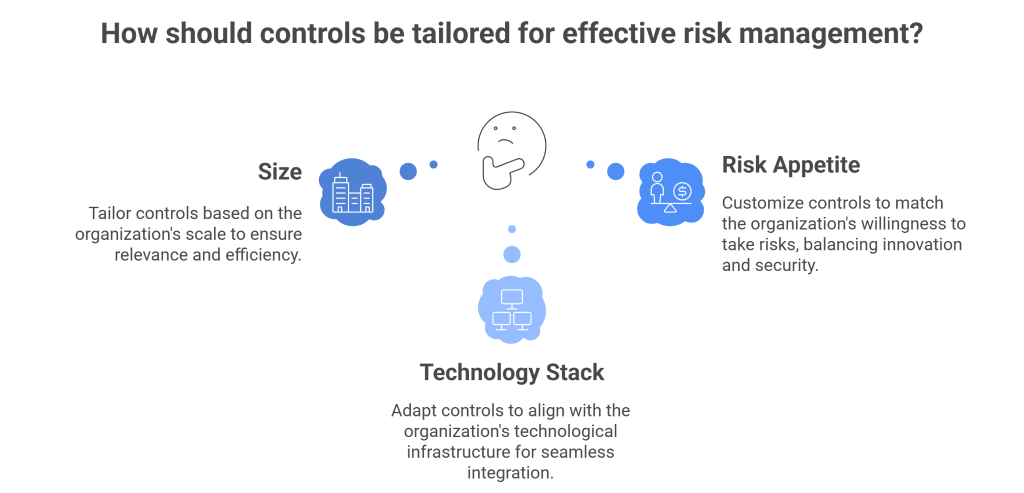
Controls must be contextualized — tailored to an organization’s size, technology stack, and risk appetite.
That means:
- Moving beyond “cookie-cutter” controls copied from frameworks.
- Designing custom internal controls that map directly to your operational realities.
- Continuously testing those controls against evolving risks.
When controls are tuned to context, they stop being theater props and start being genuine risk mitigators.
4. Unify the Risk Story
The final step is to align the narrative across governance, security, and business teams.
Every stakeholder — from compliance managers to the board — should share a single source of truth:
- What are our biggest risks?
- Which controls mitigate them?
- How confident are we in those controls right now?
Unifying this story transforms risk from a compliance metric into a strategic conversation.
Boards don’t want to hear about patch cycles or SOC 2 clauses — they want to understand exposure, trend, and impact.
When you can say, “Our exposure to insider credential theft has dropped 35% in the last quarter due to automated control validation,” you’re not performing risk management — you’re demonstrating it.
Engineering the Future of Risk Management
Risk management doesn’t need more paperwork — it needs engineering.
If risk is to be dynamic, measurable, and actionable, it must be treated like a system, not a ceremony. That means applying the same principles that drive software innovation — automation, observability, iteration — to how we detect, assess, and respond to risk.
The future of GRC isn’t built in spreadsheets.
It’s engineered into the organization’s DNA.
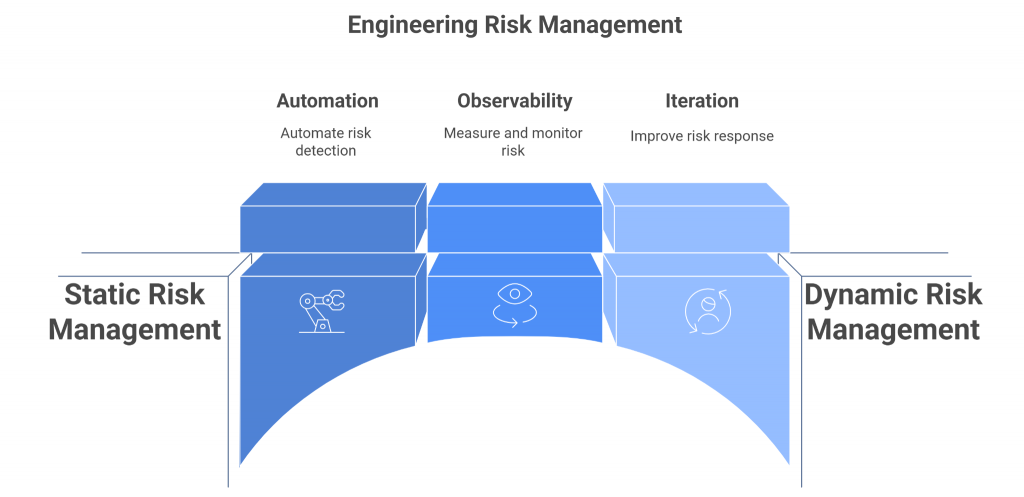
From Risk Registers to Risk Observability
The traditional risk register is like a photograph — useful once, but quickly outdated.
In contrast, risk observability gives you a live feed of your organization’s exposure.
Imagine being able to see:
- When a critical control starts failing in production.
- When a new integration introduces unvetted data exposure.
- When an incident in a peer company mirrors your environment’s vulnerabilities.
This isn’t science fiction — it’s the natural evolution of continuous risk management.
Just as DevOps introduced observability to track system health in real time, GRC must adopt the same philosophy for risk health.
Observability replaces assumptions with evidence — measurable, data-driven insights into how secure your environment truly is at any given moment.
Automate the “R” in GRC
Automation isn’t about replacing humans; it’s about removing the repetitive, low-value tasks that bury them.
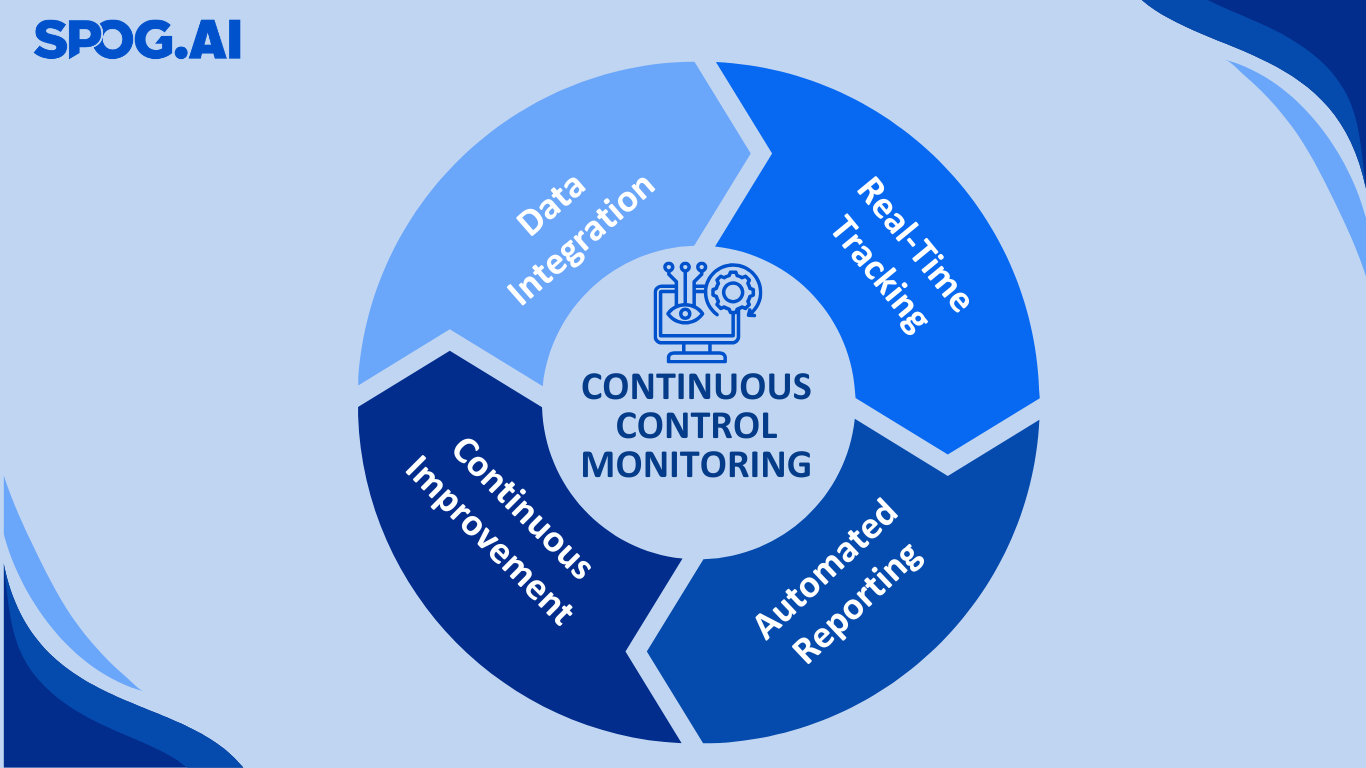
Modern risk engineering uses automation to:
- Continuously monitor controls for effectiveness and drift.
- Ingest threat intelligence and correlate it with internal asset data.
- Trigger alerts when emerging risks surpass defined thresholds.
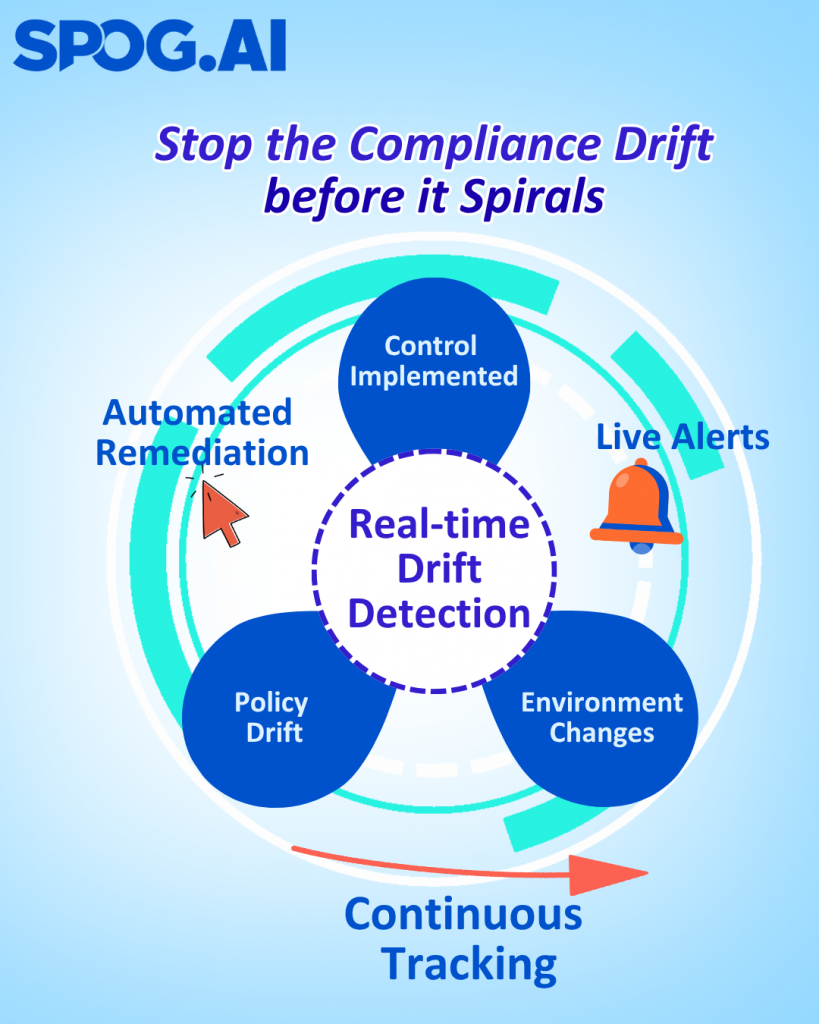
This turns risk from a reactive reporting exercise into a proactive defense mechanism.
Instead of learning about control failures during the next audit cycle, you discover them the moment they happen — and can act before they cascade into incidents.
Automation transforms awareness into agility.
It shortens the time between risk identification and risk response — the true measure of maturity.
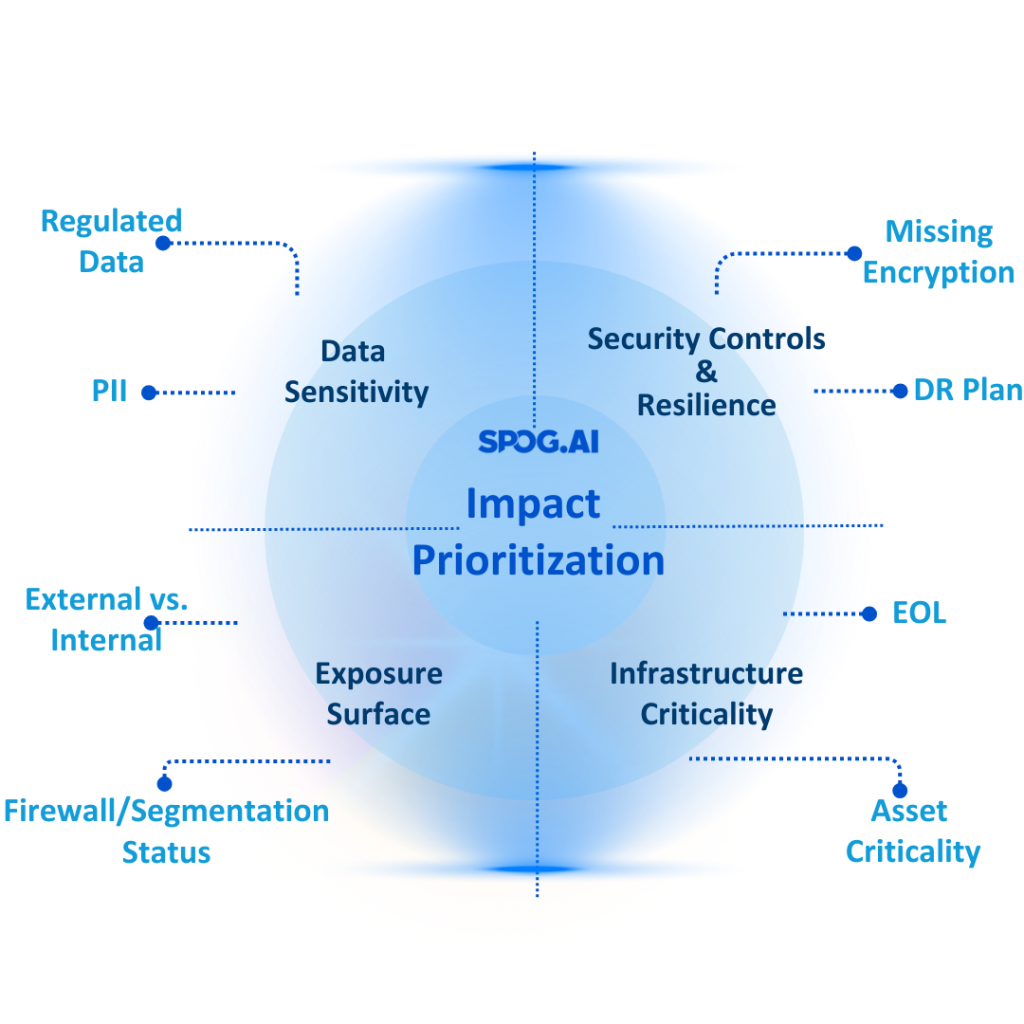
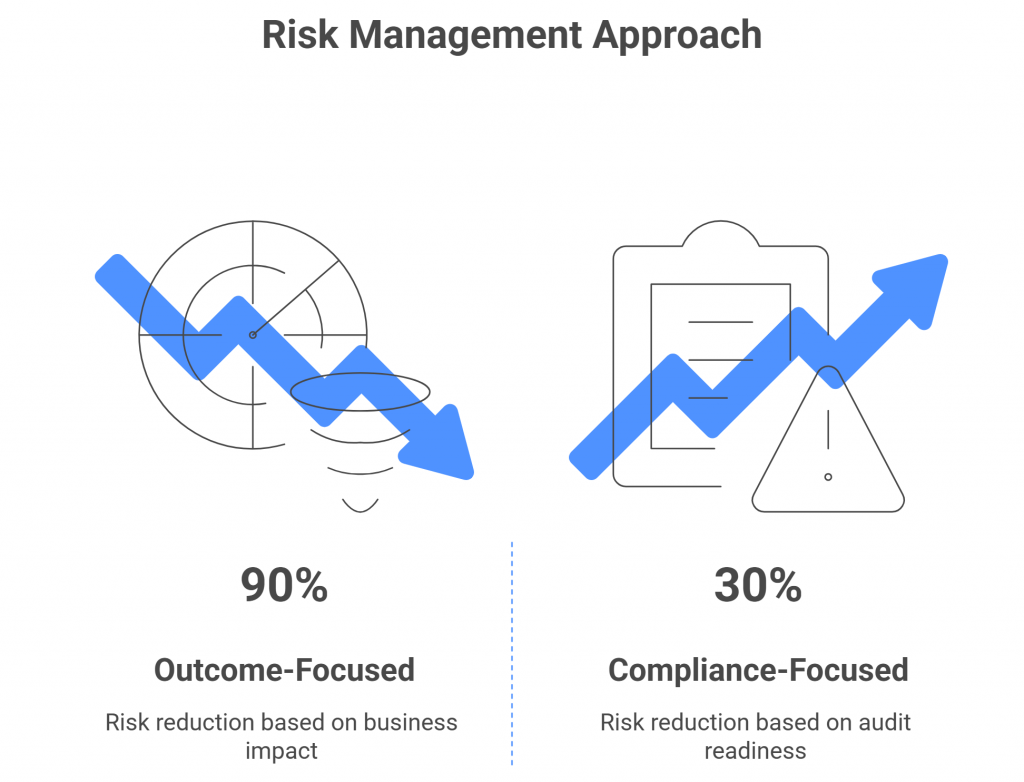
Quantify Impact, Not Just Likelihood
For decades, risk scoring has relied on subjective likelihood × impact formulas.
But without quantifying actual business impact, those numbers remain academic.
The next generation of risk programs will use impact-based prioritization — quantifying how each risk affects what the business truly values: revenue, uptime, customer trust, or regulatory exposure.
For example:
- Instead of “medium likelihood, high impact,” say “this misconfiguration could expose 40% of production data and cause $2M in potential loss.”
- Instead of “critical vulnerability,” say “this issue directly affects a tier-1 service relied on by 80% of customers.”
This approach transforms GRC from a compliance function into a decision engine — one that helps leaders allocate effort, investment, and urgency where it truly matters.
Build Feedback Loops into the Risk Lifecycle
Just as continuous integration transformed software delivery, continuous feedback must now transform risk management.
Every incident, near miss, or control failure should feed back into:
- Updated risk models
- Adjusted control logic
- New detection rules
This turns every failure into a learning input, not a reporting artifact.
Over time, these feedback loops create adaptive risk systems — ones that learn, self-correct, and evolve as the environment changes.
The Shift from Risk Compliance to Risk Intelligence
Engineering risk management isn’t just about technology — it’s a mindset shift.
Compliance answers, “Did we follow the process?”
Risk intelligence answers, “Do we understand our exposure, and are we improving it?”
That shift redefines the role of the CISO — from gatekeeper to strategic risk engineer, guiding the organization toward measurable resilience.
“The future of GRC will not be audited — it will be observed.”
When we treat risk as a living system — observable, automated, and impact-driven — we move beyond process theater and into a new era of intelligent assurance.
The Boardroom Connection
At the end of the day, risk management succeeds or fails in the boardroom.
That’s where security leaders translate complex technical realities into business decisions, where numbers become narratives, and where confidence — or doubt — is born.
And yet, this is where process theater does the most damage.
When risk programs rely on outdated registers and subjective assessments, CISOs are left presenting performative data instead of actionable insight. They can show color-coded matrices and audit results, but not real evidence of exposure or progress.
That disconnect erodes trust — not because leadership doesn’t value security, but because they can’t see its business relevance.
1. Risk Is the Language of the Board
Boards don’t speak in vulnerabilities, frameworks, or patch cycles.
They speak in risk, exposure, and impact — the language of uncertainty and consequence.
When security leaders frame discussions around these dimensions, they shift from defending budgets to driving decisions.
Instead of saying,
“We patched 80% of critical systems,”
say,
“We reduced potential revenue exposure from ransomware by 60% this quarter.”
It’s a small linguistic shift — but a massive strategic one.
It replaces activity with outcome, and transforms cybersecurity from a cost center into a business enabler.
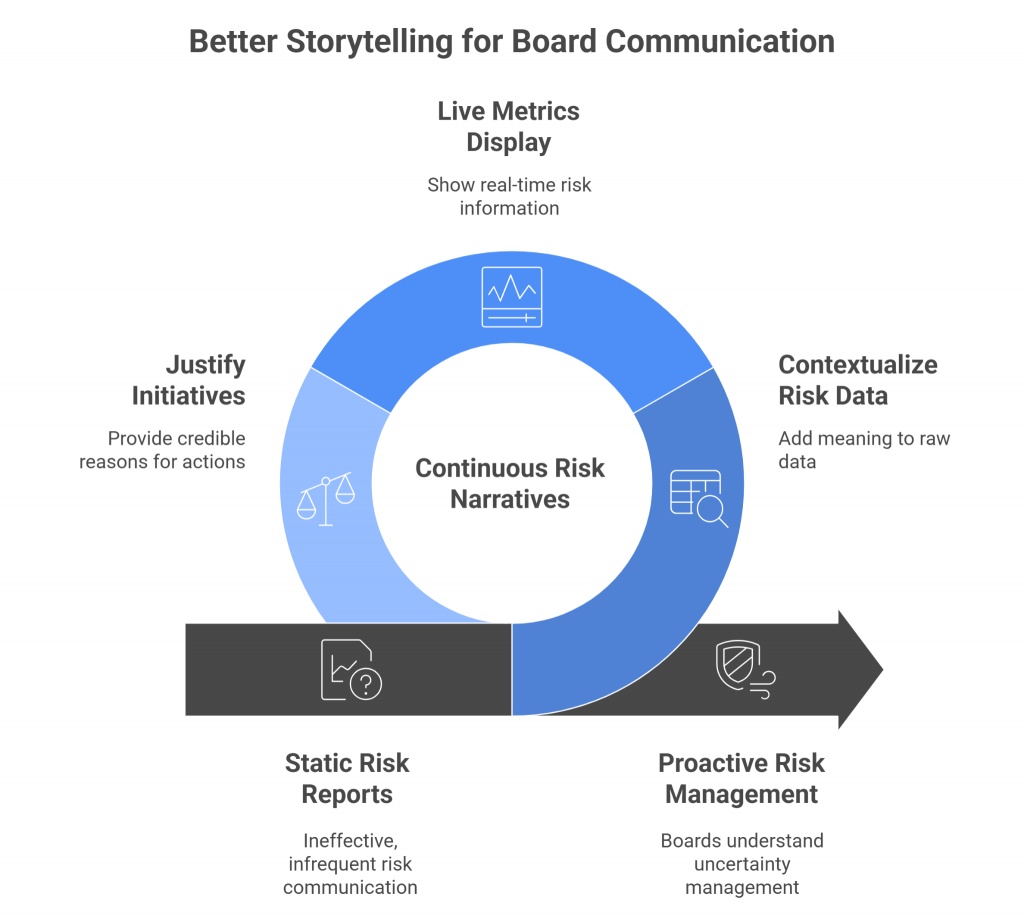
2. From Reporting to Storytelling
The future of board communication isn’t more data — it’s better storytelling.
CISOs must evolve from status reporters to narrators of risk intelligence:
- What changed in our risk landscape this quarter?
- Which controls failed or succeeded?
- Where did we reduce exposure, and where do we still need investment?
When risk data is engineered to be continuous and contextual, these stories write themselves.
Instead of static reports, boards see live metrics, clear trends, and credible justifications for every initiative.
The boardroom conversation shifts from “Are we compliant?” to “How well are we managing uncertainty?”
3. Building Credibility Through Evidence
Confidence comes from evidence, not assertion.
A risk leader who can back up every statement with data from live control telemetry, validated risk indicators, and impact quantification earns trust faster than any certification can provide.
When the board asks, “Are we exposed to this new threat?”, imagine being able to respond with:
“Here’s our exposure score trend over the last 30 days, and the top three controls actively mitigating it.”
That’s no longer process theater — that’s risk intelligence in action.
It’s tangible, defensible, and instantly credible.
4. The ROI of Real Risk Management
Executives fund what they understand.
When risk is communicated through the lens of business impact, investment becomes logical, not political.
By quantifying how risk reduction directly supports business continuity, customer trust, and revenue protection, security leaders can:
- Justify budget increases with data-driven narratives.
- Prioritize initiatives based on measurable exposure reduction.
- Align security KPIs with enterprise objectives.
Boards don’t resist funding security — they resist funding uncertainty.
Clarity is the ultimate catalyst for investment.
5. From Doubt to Dialogue
The ultimate goal isn’t just to inform the board — it’s to engage them.
When risk management evolves into a real-time, data-rich discipline, board discussions become two-way dialogues about resilience, not one-way updates on compliance.
And that’s where transformation happens — not in the metrics, but in the mindset.
When risk becomes the shared language of business,
cybersecurity finally earns its seat at the strategic table.
Conclusion — From Performance to Progress
For too long, risk management has been an act — a set of rituals designed to demonstrate diligence rather than deliver resilience.
Quarterly assessments, static risk registers, and compliance checklists have given us a comforting illusion of control, but not control itself.
The time for process theater is over.
Organizations can no longer afford to treat risk as a formality; they must treat it as a function of engineering, intelligence, and impact.
That means rebuilding our programs around four guiding principles:
- Continuity — risk monitoring should be as real-time as the threats we face.
- Context — controls must adapt to each organization’s unique environment and priorities.
- Clarity — risk communication should translate technical data into business impact.
- Confidence — leaders should be able to answer, at any moment, “How safe are we, really?”
This is not an aspirational future — it’s an achievable one.
With modern risk engineering, automation, and impact-based prioritization, security teams can finally move beyond the theater of compliance and into the science of decision-making.
When risk management becomes continuous, contextual, and credible, it earns something far more valuable than audit approval — it earns trust.
Trust from the board, trust from the business, and trust from the people who depend on those systems to work securely every day.
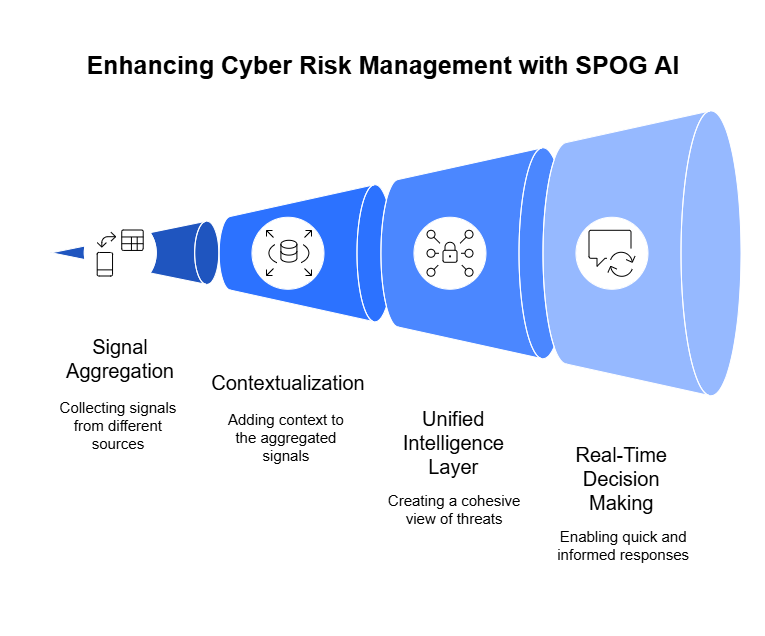
And this is precisely the vision driving SPOG.AI.
By delivering impact-based risk intelligence, SPOG.AI helps security teams cut through the noise of endless alerts and manual assessments — transforming fragmented data into a clear, dynamic picture of what truly matters.
It’s the difference between knowing your risks exist and knowing which ones matter right now — and acting on them before they escalate.
Because true risk management isn’t a performance — it’s progress.
And progress is what the next generation of security leadership will be measured by.