Introduction: The Evolution of Third-Party Risk Management
Businesses today rely on third-party vendors for everything from cloud services to data processing. These partners enable scale and speed—but also open the door to risk. Each vendor increases exposure to cyber threats, compliance failures, and operational breakdowns.
Yet most companies still rely on point-in-time assessments—risk reviews during onboarding or annual audits. That’s no longer enough. Risks shift fast. A vendor secure last quarter could be breached today—and you may not know until it’s too late.
The fallout is growing. 61% of companies experienced a third-party breach in the past year—a 50% spike, and three times higher than in 2021. Static reviews can’t keep up with a threat landscape that changes by the hour.
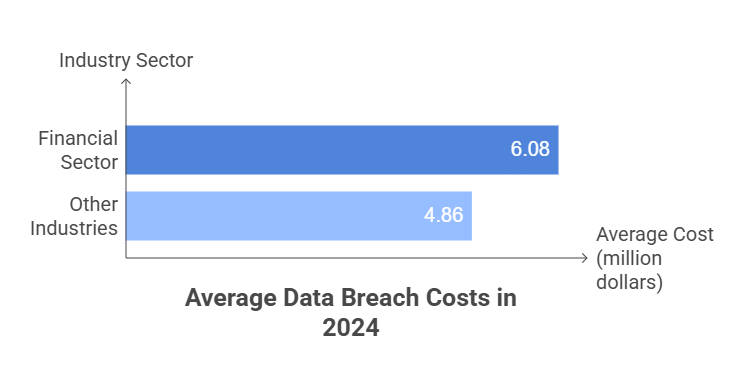
Continuous monitoring changes the game. It tracks vendors in real time and flags changes in risk—like cyber incidents, financial distress, or negative media—before they escalate. According to the 2024 IBM/Ponemon Cost of a Data Breach Report, third-party breaches increase breach costs by 5%, making them one of the most expensive risks to recover from.
That’s why more organizations are shifting from outdated checklists to dynamic, always-on risk management. In this article, we’ll explore how continuous monitoring works, how it fits into modern third-party risk management platforms, and how it helps in managing third-party risk with greater speed and precision.
Why Point-in-Time Assessments Are No Longer Enough
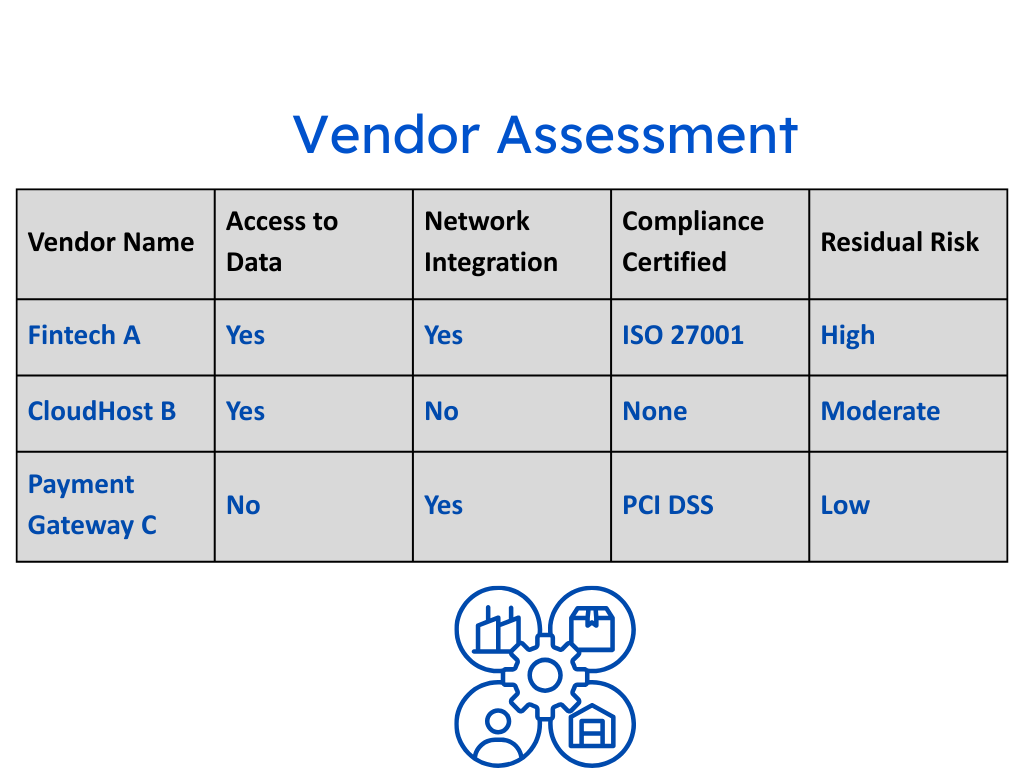
Traditional third-party risk management relies on point-in-time assessments—risk reviews during onboarding or at set intervals. But today’s risk landscape doesn’t follow a schedule. A vendor’s security posture can shift overnight due to a data breach, regulatory violation, or reputational crisis. By the time the next review rolls around, the risk may have already turned into damage.
Static tools like spreadsheets and emailed questionnaires only add friction. They’re time-consuming, error-prone, and provide outdated views the moment they’re completed. Meanwhile, threats continue to evolve quietly in the background.
This model also puts pressure on teams to “catch everything” during periodic reviews. But that’s impossible in ecosystems with hundreds—or thousands—of third-party relationships. Without visibility between reviews, organizations operate in the dark.
The core problems with point-in-time assessments:
- ✅ No real-time visibility: Risks can emerge and escalate between reviews.
- ❌ Static tools create blind spots: Spreadsheets and email-based checklists can’t keep pace.
- 🕑 Delayed detection leads to delayed response: Teams react only after damage is done.
- 🔄 Not scalable: Reviewing hundreds of vendors manually isn’t practical.
- 🧩 Lack of context: Point-in-time data ignores changes in external conditions like cyber threats or financial instability.
More than ever, businesses need risk practices that move at the speed of their operations. That means replacing reactive check-ins with real-time insights. Continuous monitoring fills this gap, offering a dynamic way to stay ahead of changes and act on threats as they emerge—not months later.
What Is Continuous Monitoring in TPRM?
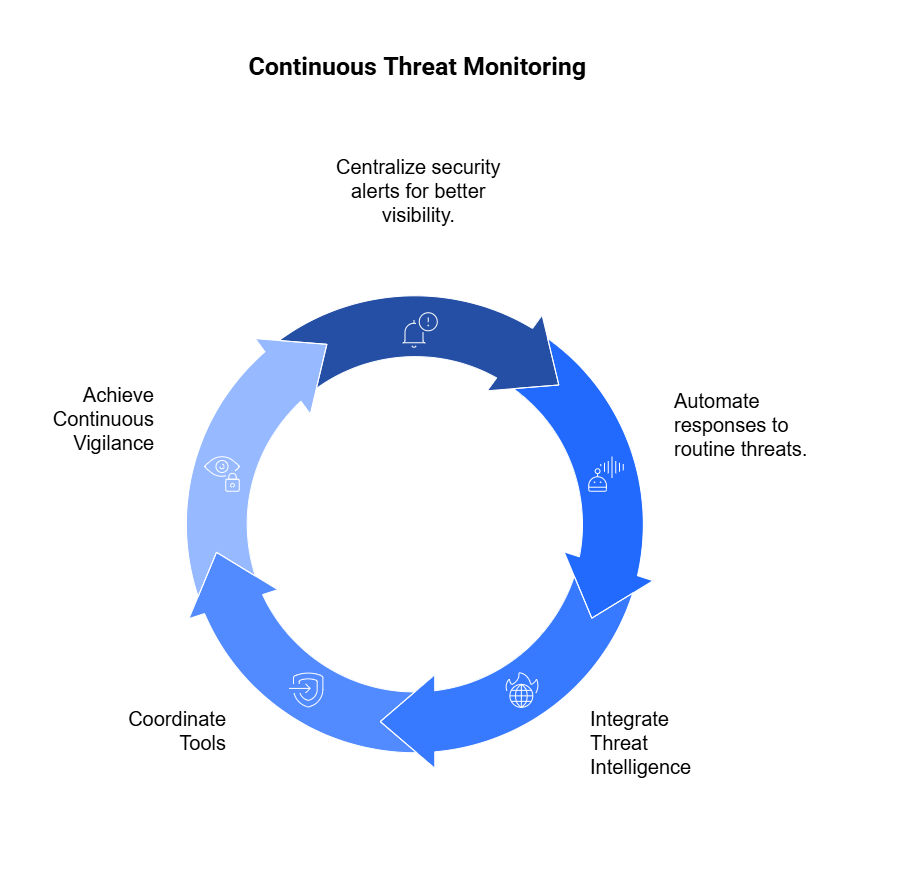
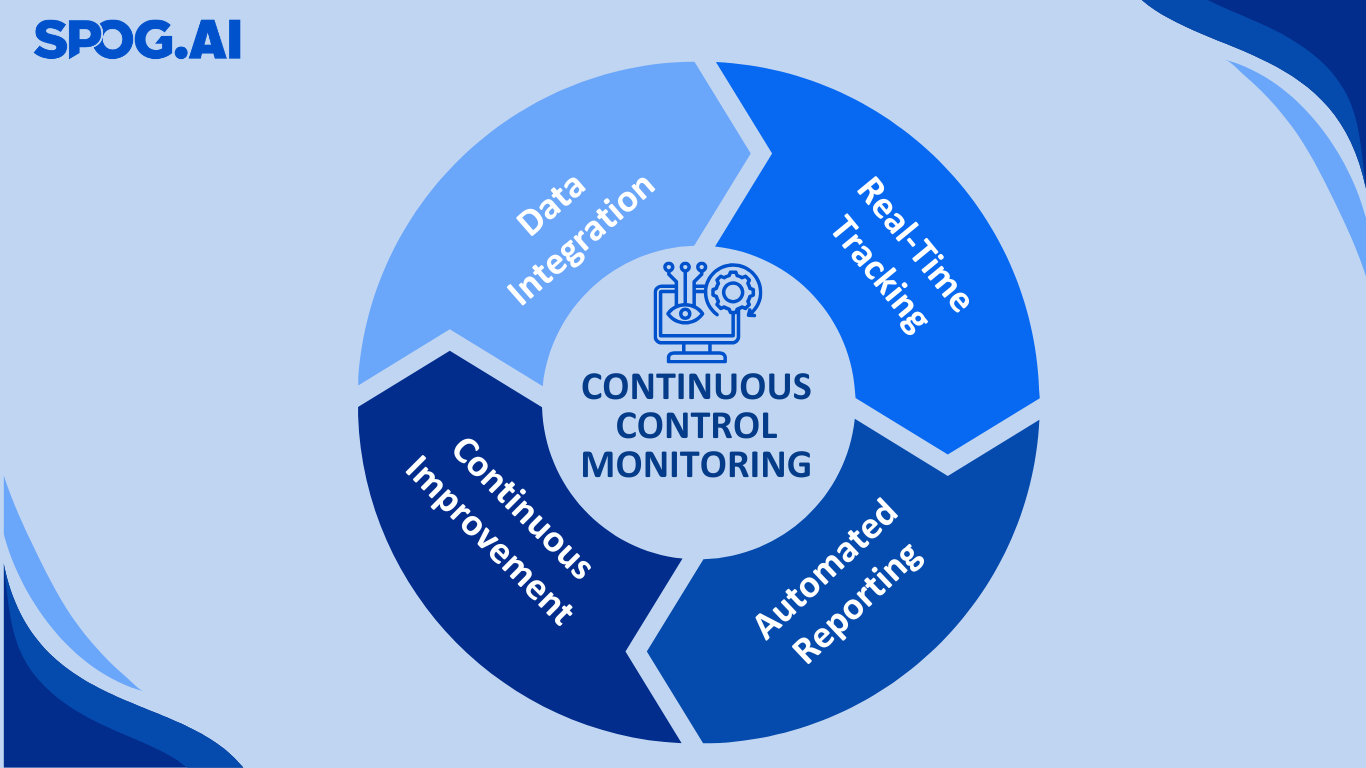
Continuous monitoring is the practice of tracking third-party risk in real time—or near real time—across key areas such as cybersecurity, financial health, regulatory compliance, and reputation. Unlike point-in-time reviews, it provides an always-on lens into a vendor’s risk posture, enabling faster detection, deeper insights, and quicker response.
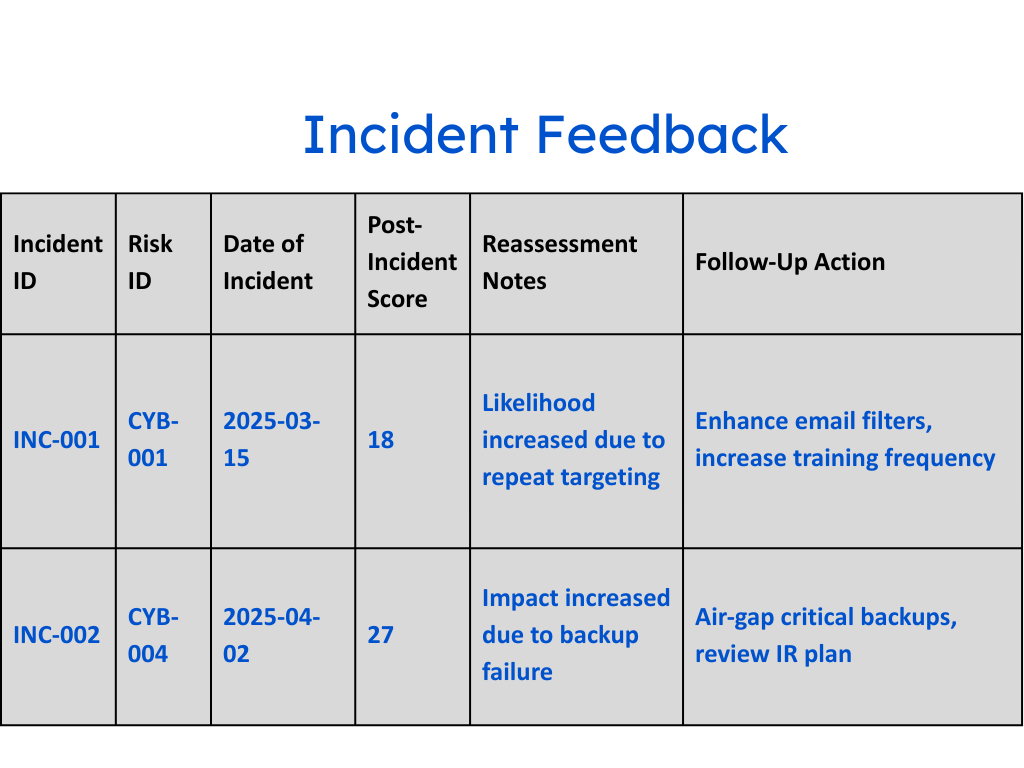
This approach helps organizations shift from a reactive to a proactive stance. Rather than waiting for risk to reveal itself during an annual review or post-incident investigation, teams receive alerts as soon as a vendor’s risk profile changes.
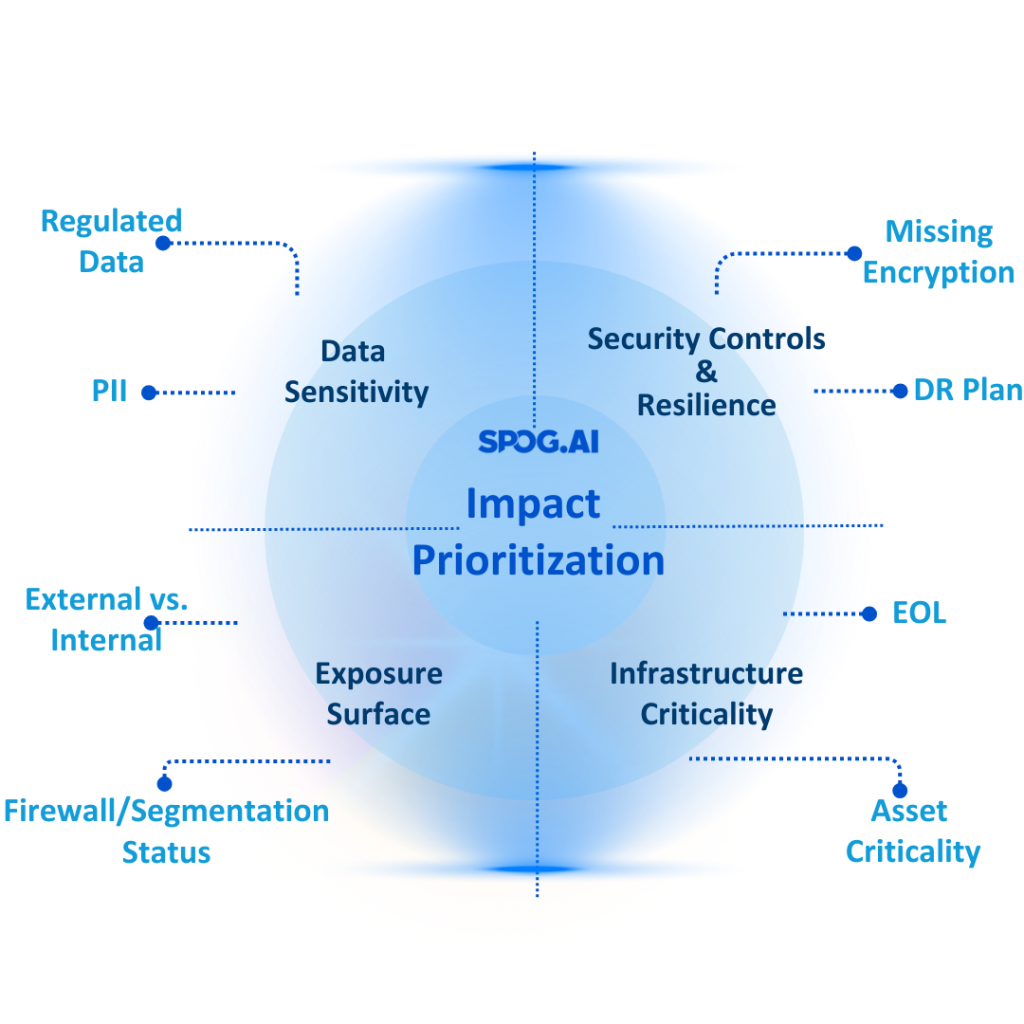
Core components of continuous monitoring in TPRM:
- Cybersecurity intelligence: Monitors threat activity, data leaks, and security score changes using external threat intelligence feeds and dark web scanning.
- Financial health monitoring: Tracks credit ratings, bankruptcy filings, and revenue signals to detect financial instability.
- Regulatory and compliance checks: Flags vendor violations, sanctions, or enforcement actions in real time.
- Reputational risk analysis: Captures news mentions, social sentiment, and media signals that could affect brand alignment or trust.
- Automated alerts and workflows: Notifies stakeholders and triggers playbooks when high-risk changes are detected.
Modern third-party risk management platforms often integrate these capabilities into a single dashboard—giving teams a unified, real-time view of vendor risk across the enterprise. Some platforms even incorporate AI to prioritize alerts, detect anomalies, or summarize incidents for faster triage.
This level of continuous visibility transforms how organizations approach managing third-party risk. It helps security, procurement, and compliance teams align better, respond faster, and avoid the high costs and reputational damage that follow unchecked vendor failures.
Benefits of Real-Time Risk Intelligence
Shifting from point-in-time reviews to continuous monitoring unlocks significant advantages across the business. Real-time risk intelligence doesn’t just improve visibility—it transforms how organizations detect, manage, and respond to vendor-related threats.
By embedding continuous insights into your third-party risk management (TPRM) program, you gain the speed and control needed to stay ahead of emerging risks, reduce costs, and strengthen compliance.
Key benefits of continuous monitoring:
- ⚡ Faster Detection, Faster Response
Real-time alerts allow teams to act within hours—not weeks. This reduces dwell time and limits the damage caused by third-party incidents. - 🔁 Continuous Risk Awareness
Teams can see how a vendor’s risk posture evolves over time. Instead of relying on one-off assessments, they use trend data to make smarter decisions about onboarding, renewals, and offboarding. - 📊 Data-Driven Vendor Oversight
Risk-based decisions become more consistent and defensible. Continuous data supports internal audits, regulatory reporting, and executive-level oversight. - 🤝 Better Cross-Functional Collaboration
Procurement, security, compliance, and legal teams can work from the same risk data—enabling aligned workflows and fewer gaps in communication. - ⚙️ Automation of Risk Workflows
Modern third-party risk management platforms integrate continuous monitoring with ticketing systems and response playbooks. This reduces manual effort and ensures quicker mitigation.
Real-time intelligence empowers companies to move from reactive firefighting to proactive defense. It also demonstrates due diligence to regulators, customers, and investors—strengthening trust and accountability across the vendor ecosystem.
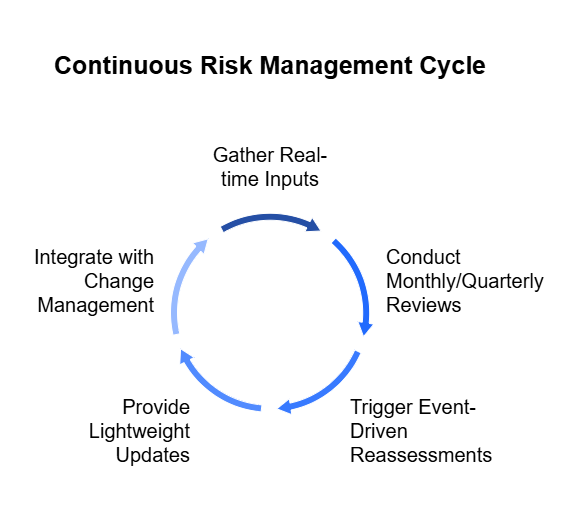
How to Implement Continuous TPRM Monitoring
Organizations that succeed with continuous monitoring don’t just add a new tool—they build a smarter, more adaptive risk management model. They integrate real-time monitoring into their workflows, define clear processes, and focus on the vendors that matter most.
Here’s how to put continuous TPRM into action:
- 🎯 Prioritize High-Risk Vendors
Not all vendors pose the same level of risk. High-performing teams use risk-based segmentation to focus monitoring efforts on critical vendors—those with access to sensitive data, regulated services, or key operations. - 🔗 Integrate with Existing Platforms
Instead of managing risk in isolation, continuous monitoring connects with existing GRC tools, SIEMs, and procurement systems. This creates a seamless flow of risk data across the organization. - 📡 Use Multiple Data Sources
Effective monitoring pulls from a variety of feeds—cyber threat intelligence, financial health reports, regulatory watchlists, and reputational data. The more inputs, the more accurate the risk picture. - 🚨 Establish Real-Time Alerting and Playbooks
Alerts alone aren’t enough. Top teams define action paths for specific risk events—whether that means triggering internal reviews, escalating to legal, or notifying executive leadership. - 📈 Monitor Trends, Not Just Events
Smart organizations look beyond isolated alerts. They track changes over time to understand vendor trends—whether risk is rising, stable, or improving—and use that data to inform contract renewals or termination decisions. - 🤖 Automate What Matters
Through rule-based triggers and machine learning, teams automate low-level tasks (e.g., routing tickets, logging evidence, notifying stakeholders) so they can focus on complex, high-risk scenarios.
By embedding continuous monitoring into their third-party risk management programs, these organizations reduce blind spots, improve response times, and build more resilient vendor ecosystems—without overwhelming their teams.
Choosing the Right Tools and Metrics for Success
The most effective third-party risk management (TPRM) programs pair technology with strategy. They focus on visibility, automation, and outcomes that align with business goals.
What to look for in a continuous monitoring solution:
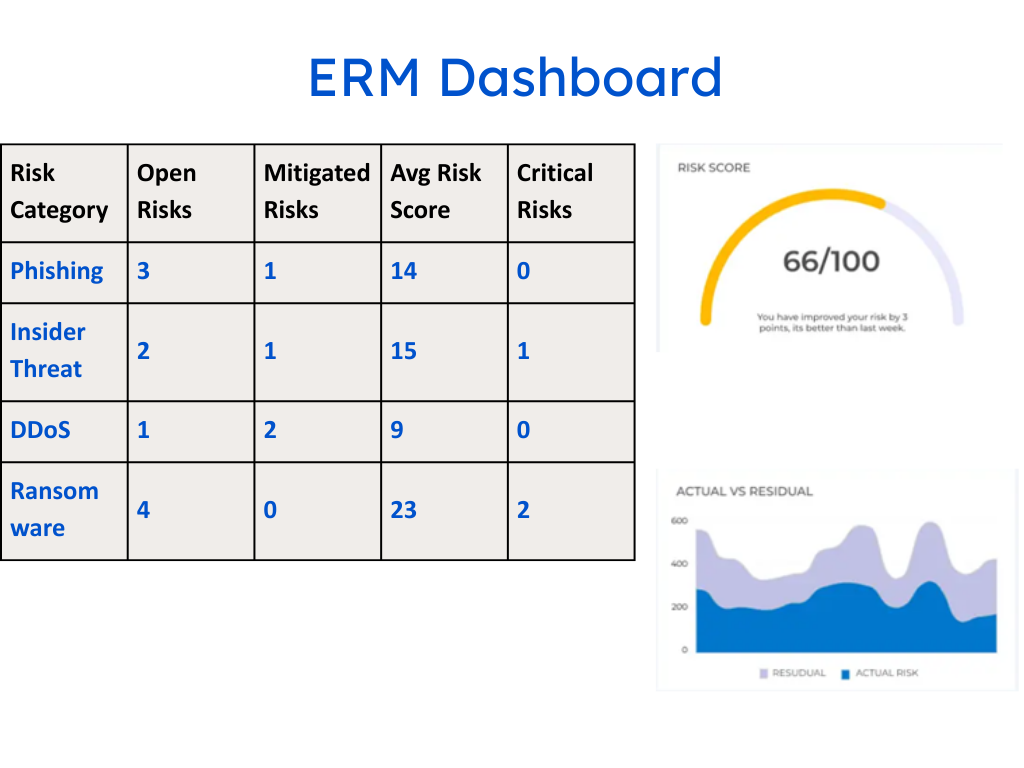
- Unified Risk Dashboard
A centralized view that consolidates cyber, financial, compliance, and reputational risks across all vendors—no more siloed reports or fragmented data. - Real-Time Alerts and Custom Thresholds
The ability to receive instant notifications on specific risk indicators and set custom thresholds based on your organization’s tolerance. - API Integrations with Core Systems
Seamless connectivity with procurement tools, GRC platforms, and ticketing systems (like Jira or ServiceNow) for faster response and better workflow alignment. - Intelligence-Driven Scoring Models
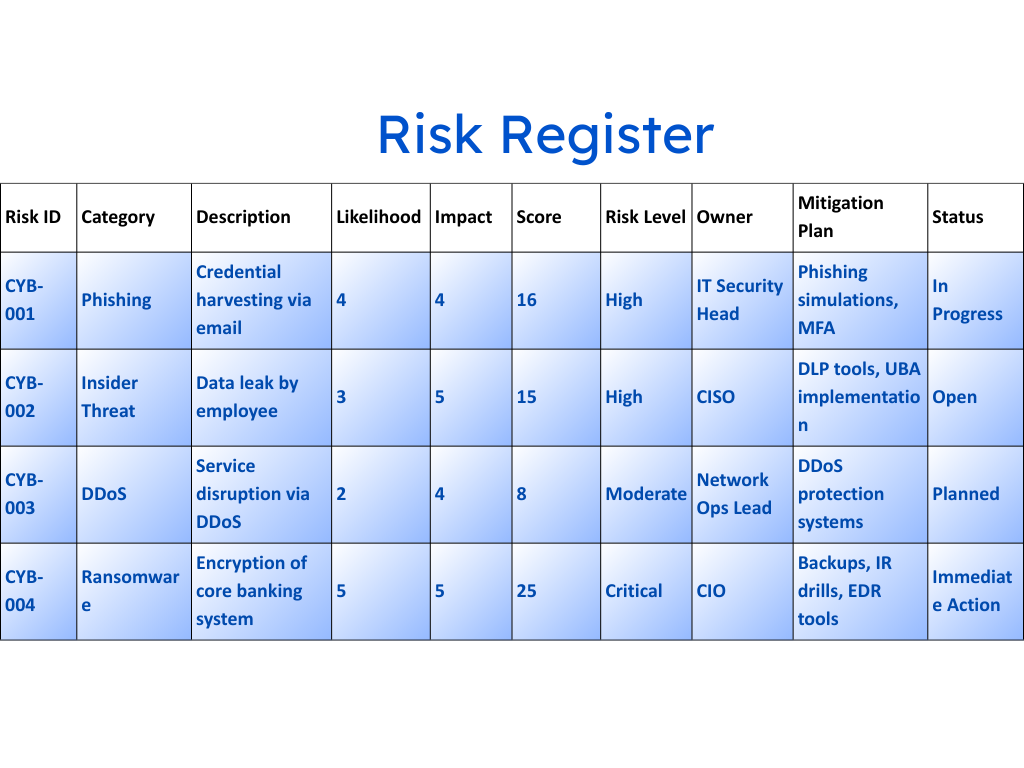
Risk scores that adapt based on live inputs—not static questionnaires. Look for solutions that factor in contextual intelligence and vendor behavior over time. - Automated Documentation and Audit Trails
Automatically log every alert, action, and resolution for internal reporting, audits, or compliance checks.
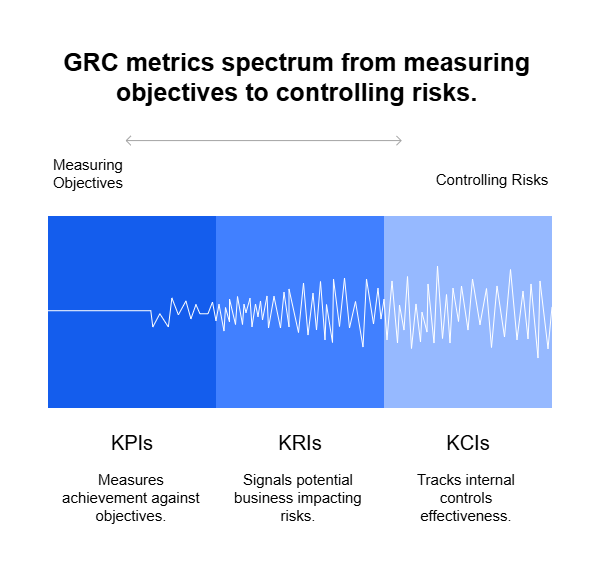
KPIs That Matter in Continuous TPRM
Tracking success is just as important as tool selection. Leading organizations measure:
- ⏱️ Mean Time to Detect (MTTD) – How quickly the system surfaces vendor risk events.
- ⏳ Mean Time to Respond (MTTR) – How fast your team takes action once notified.
- 📉 Risk Reduction Over Time – Changes in overall vendor risk scores and incident frequency.
- 🧩 Vendor Risk Distribution – Percentage of vendors by criticality or risk tier.
- 📬 Alert Volume vs. Resolution Rate – Ratio of alerts received to those reviewed and closed.
Choosing the right tools and metrics ensures your continuous monitoring program delivers not just data—but decisions. It turns insights into outcomes and positions your organization to stay ahead of emerging threats with confidence.
Conclusion: The Business Case for Real-Time TPRM
As third-party ecosystems grow larger and more complex, the cost of delayed risk detection continues to rise. Static assessments leave organizations exposed, while real-time insights give them the visibility and speed to act decisively.
Continuous monitoring empowers teams to detect vendor risks faster, respond more effectively, and make smarter, data-driven decisions. It aligns security, procurement, and compliance functions around a shared view of third-party risk—and drives operational resilience across the enterprise.
The business case is clear:
- Reduce the likelihood and impact of third-party breaches
- Automate risk workflows and reduce manual overhead
- Build trust with regulators, customers, and stakeholders
- Stay ahead of threats in an increasingly volatile vendor landscape
Organizations that invest in modern third-party risk management platforms and embrace real-time risk intelligence position themselves not just to avoid disruption—but to lead with confidence.
If your TPRM program still relies on static assessments, now is the time to evolve. Continuous monitoring isn’t just the future of third-party risk management—it’s the standard for organizations that take risk seriously.