83% of enterprise buyers require SOC 2 compliance before vendor onboarding—making it not just a regulatory checkbox, but a mission-critical enabler of business growth and a gatekeeper for market access. For B2B service providers, achieving SOC 2 Type II compliance is now essential for scaling, establishing credibility, and earning customer trust.
Yet, preparing for a SOC 2 Type II audit can feel overwhelming—especially when you’re juggling the demands of day-to-day operations. The process typically spans 6 to 12 months and involves complex internal controls, cross-functional coordination, and detailed documentation.
But it doesn’t have to be that hard—or that long.
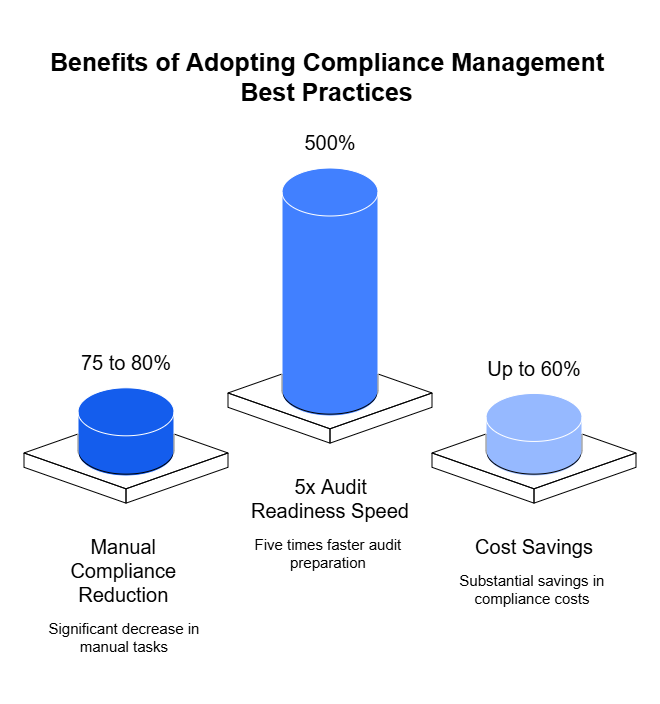
With strategic planning, automation, and a documentation-first approach, you can cut your prep time in half—down to just 3 to 6 months—without sacrificing audit quality or readiness. In fact, companies that adopt best practices report:
- Up to 75–80% reduction in manual compliance work
- 5x faster audit readiness
- Up to 60% cost savings on compliance operations
In this guide, we’ll walk through an accelerated SOC 2 Type II preparation process, including a real-world timeline, essential documentation checklist, and practical automation strategies to supercharge your compliance management.
Why SOC 2 Type II Matters
While SOC 2 Type I assesses whether controls are properly designed at a single point in time, SOC 2 Type II goes much deeper. It evaluates the operational effectiveness of those controls over an extended monitoring period—typically 3 to 12 months—providing a far more rigorous and trusted assurance of a company’s ongoing security posture.
A Signal of Trust for Customers and Partners
With growing concerns around data privacy, cybersecurity, and third-party risk, enterprise buyers and partners demand proof of strong compliance management practices. SOC 2 Type II offers that proof. It demonstrates that your organization:
- Actively protects customer data through clearly defined controls
- Maintains operational discipline across security, availability, and confidentiality
- Has processes in place to detect, prevent, and respond to security incidents
A Strategic Advantage in a Crowded Market
SOC 2 Type II is often the bare minimum requirement to compete in enterprise and regulated sectors. Whether you’re in SaaS, fintech, healthtech, or cloud services, having this audit in place not only reduces friction in procurement processes but also shortens sales cycles and boosts client confidence.
Companies without SOC 2 often face delays in onboarding, loss of deals, and reputational risks—particularly when engaging with industries governed by strict regulatory compliance frameworks.
Future-Proofing Your Organization
Beyond sales and security, SOC 2 Type II instills a culture of risk-aware operations. It forces organizations to evaluate and mature their internal processes—from onboarding and access control to incident response and vendor management. The result? Greater operational resilience and reduced exposure to legal or reputational harm.
Accelerated SOC 2 Type II Prep Timeline
Traditional SOC 2 Type II audit preparation can stretch over 6 to 12 months, draining resources and slowing down business momentum. But with the right combination of structure, accountability, and automation, you can shrink that timeline to just 3–6 months—without sacrificing regulatory compliance or audit integrity.
Here’s a streamlined 5-phase prep plan to help you get there faster:
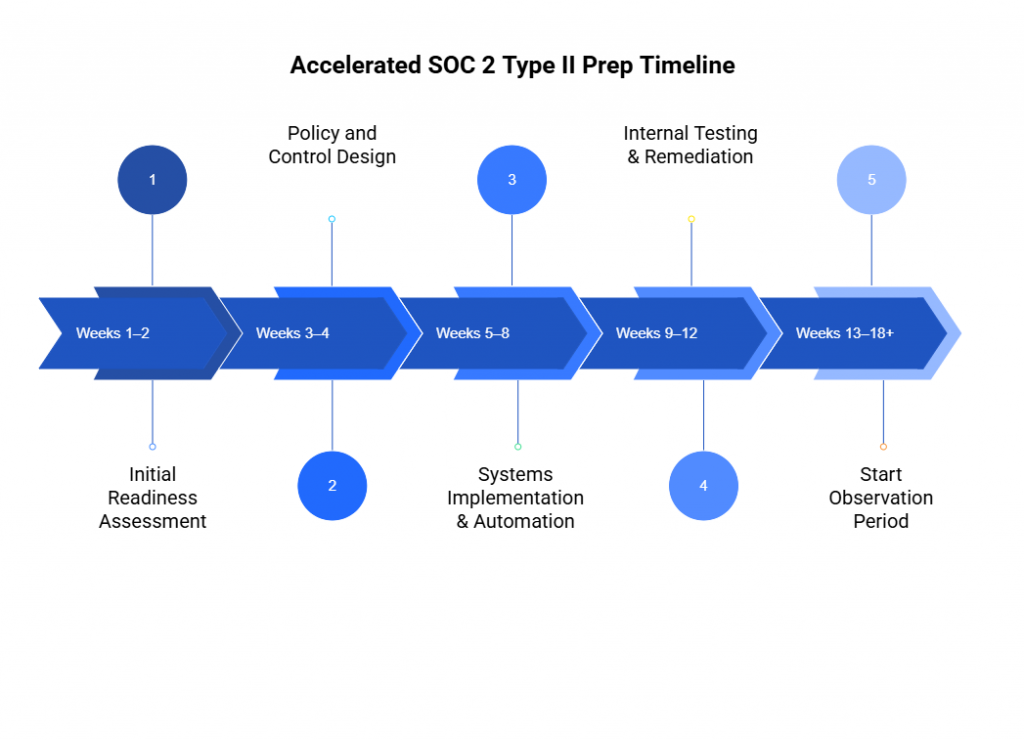
Phase 1: Weeks 1–2 — Initial Readiness Assessment
- Define the scope: Choose the relevant Trust Services Criteria (TSC)—most organizations begin with Security, then layer in Availability or Confidentiality.
- Select an auditor: Engage a certified CPA firm with SOC 2 experience, ideally one that integrates well with your compliance tools.
- Conduct a gap analysis: Evaluate current controls against SOC 2 requirements. Identify high-risk areas and process gaps.
- Build a stakeholder map: Identify compliance owners across IT, HR, DevOps, Security, and Legal.
Phase 2: Weeks 3–4 — Policy and Control Design
- Document key policies: Create or refine information security, access management, data handling, and incident response policies.
- Align controls with systems: Map out how your policies translate into operational controls across infrastructure, endpoints, and workflows.
- Assign ownership: Designate control owners and define review cadences to ensure long-term accountability.
Phase 3: Weeks 5–8 — Systems Implementation & Automation
- Close control gaps: Implement technical safeguards such as MFA, endpoint protection, logging, encryption, and secure onboarding/offboarding.
- Leverage automation tools: Use GRC platforms like Spog.AI to auto-collect evidence and monitor control effectiveness.
- Conduct mock audits: Simulate audit scenarios to identify weaknesses early and streamline internal processes.
Phase 4: Weeks 9–12 — Internal Testing & Remediation
- Test control effectiveness: Perform walkthroughs and control validation exercises with internal or external consultants.
- Remediate findings: Address any deficiencies quickly and re-test as needed.
- Prepare teams: Conduct compliance training and run through sample auditor interviews with key stakeholders.
Phase 5: Week 13–18+ — Start Observation Period
- Kick off the audit window: Your controls must now perform consistently over 3–6 months.
- Enable continuous monitoring: Use automated tools to track evidence and flag anomalies in real time.
- Maintain communication with auditors: Periodic check-ins help reduce surprises during final reporting.
SOC 2 Documentation Checklist
Solid documentation is the foundation of a successful SOC 2 Type II audit. It not only demonstrates that your controls are in place—it proves they’re operating effectively over time. Incomplete or inconsistent documentation is one of the most common reasons audits are delayed or fail.
Below is a structured checklist of must-have documents, categorized for clarity and aligned with core compliance management responsibilities.
Governance & Security Policies
These are foundational documents that establish your organization’s security and compliance posture:
Information Security Policy
Acceptable Use Policy
Access Control Policy
Data Classification & Handling Policy
Incident Response Plan
Business Continuity & Disaster Recovery Plan
Vendor Management Policy
Risk Assessment & Risk Treatment Policy
Password & Authentication Policy
Change Management Policy
Pro Tip: Ensure these policies are version-controlled, reviewed annually, and acknowledged by employees.
🛠 Operational Procedures & Records
Demonstrate the day-to-day execution of your policies with:
Onboarding and offboarding checklists
Security awareness training logs
Employee signed acknowledgments of security policies
Background checks and screening documentation
Asset inventory with owner assignments
Access reviews and user provisioning logs
Incident response logs (even if no major incident occurred)
🧰 Technical Artifacts & Evidence
This category includes system-level logs and technical configurations that prove your controls are enforced:
Access control logs (e.g., Okta, GSuite, AWS)
Audit trails for critical systems
MFA enforcement and reporting
Encryption configuration (in-transit and at-rest)
System uptime/availability records
Backup and restore test reports
Patch management and vulnerability scan logs
Endpoint protection deployment reports
Pro Tip: Automating the collection of these artifacts via a compliance management tool will save significant time and reduce audit stress.
📊 Organizational Structure & Control Mapping
Auditors also expect to see how your team and controls are structured:
Organizational chart with roles and responsibilities
Control matrix mapping each policy to its technical and human enforcement
List of key service providers and third-party dependencies
Vendor risk assessments and due diligence records
Collecting, organizing, and maintaining this documentation upfront not only accelerates your audit prep—it also strengthens your internal regulatory compliance program long-term. Make it a habit to keep these updated continuously rather than rushing during audit season.
Automation Tips to Accelerate SOC 2 Compliance Management
One of the most effective ways to fast-track your SOC 2 Type II audit prep is to embrace automation. Manual evidence collection, policy tracking, and control monitoring are not only time-consuming—they’re also prone to error and oversight.
Below are high-impact automation tips that can supercharge your compliance management process.
1. Use a GRC Platform for Continuous Monitoring
Automated GRC tools can automatically:
- Pull evidence from your tech stack (e.g., AWS, Google Workspace, GitHub, Okta)
- Monitor for control failures in real time
- Generate reports aligned with auditor requirements
- Alert you to drift or noncompliance as it happens
This reduces the need for manual snapshots and helps ensure ongoing regulatory compliance.
2. Automate Employee Onboarding & Offboarding
Integrated workflows with your HRIS (e.g., Rippling, BambooHR) and identity providers (e.g., Okta, Azure AD) can:
- Enforce security training completions
- Auto-provision access based on roles
- Ensure timely deprovisioning during offboarding
- Track and log employee policy acknowledgments
This not only supports compliance but reduces the risk of human error or insider threats.
3. Centralize Policy Management
Use tools like Confluence, Notion, or built-in policy modules in GRC platforms to:
- Host version-controlled policy documents
- Track employee acknowledgments
- Manage annual policy reviews and updates
- Maintain a single source of truth for auditors
Automating notifications and sign-offs ensures you never fall behind on documentation maintenance.
4. Automate Security Scans and Patch Management
Leverage tools like Tenable, CrowdStrike, or Jamf to:
- Continuously monitor for vulnerabilities
- Auto-deploy critical patches
- Generate compliance-ready reports
- Provide proof of endpoint protection and OS compliance
These capabilities directly support controls around system security and incident prevention.
5. Schedule Recurring Internal Controls Testing
Use task management tools like Asana, Jira, or ClickUp to:
- Automate control reviews on a monthly or quarterly basis
- Assign accountability for recurring audits
- Track remediation timelines
- Log evidence collection tasks to avoid last-minute scrambles
This habit of recurring compliance work keeps your SOC 2 program healthy between audit cycles.
Automation doesn’t replace your compliance team—it empowers them. By eliminating repetitive tasks and increasing visibility, automation transforms SOC 2 from a one-time fire drill into a continuous, manageable business function.
How to Choose the Best SOC 2 Compliance Management Solution
The right SOC 2 compliance management solution can drastically simplify your audit journey, reduce manual work, and ensure continuous regulatory compliance. But with so many tools on the market—each claiming to offer complete automation and seamless integration—it’s essential to evaluate your options based on your business size, tech stack, and compliance maturity.
Here’s a strategic framework to help you choose the best solution for your SOC 2 needs:
✅ 1. Look for Purpose-Built GRC Platforms
Ensure the tool is designed specifically for SOC 2 and other security frameworks like ISO 27001, HIPAA, or GDPR. The best GRC automation tools specialize in SOC 2 automation and offer pre-mapped control libraries, evidence collection templates, and audit-aligned workflows.
What to look for:
- Built-in SOC 2 Type II control mapping
- Preloaded templates for policies and procedures
- Support for multiple frameworks (if you’re planning to scale)
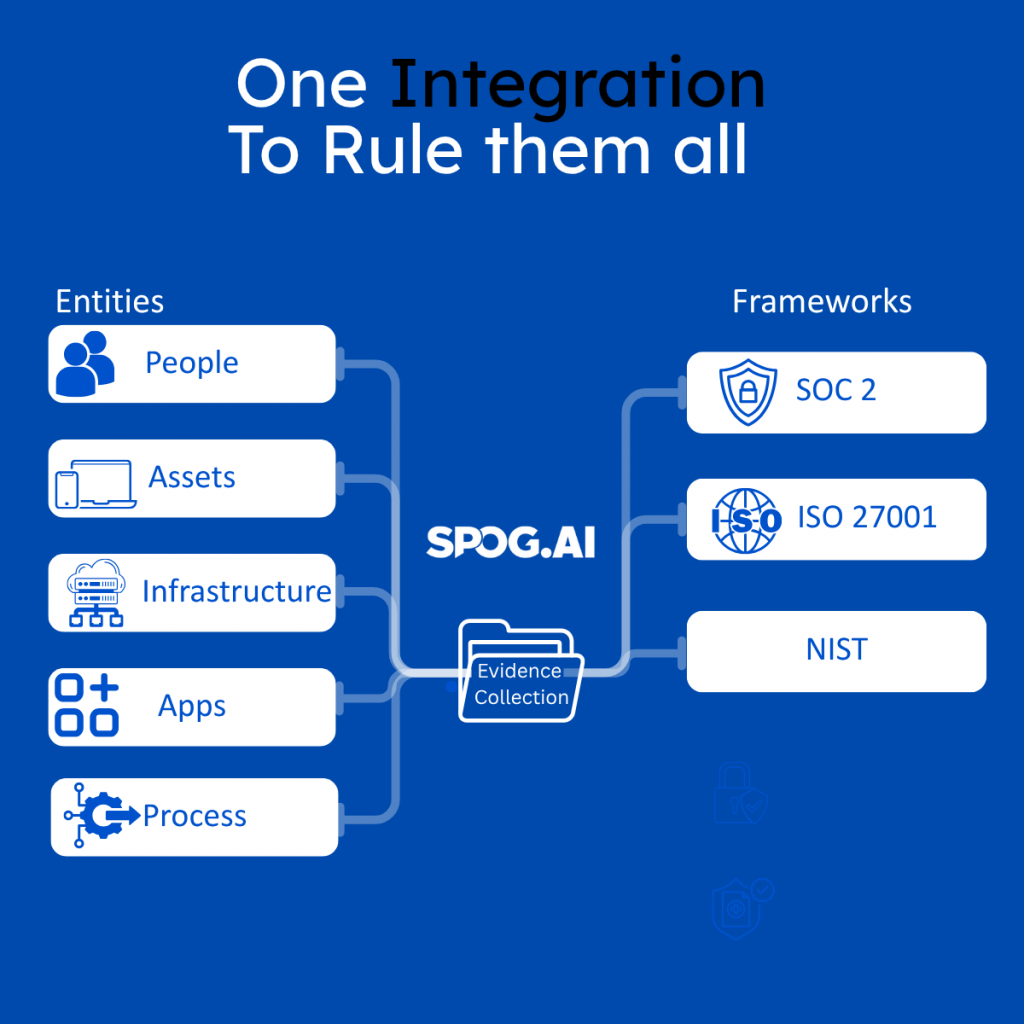
2. Prioritize Seamless Integrations
Your tool should integrate with your entire tech stack, including cloud and on-premises, to automatically pull audit evidence from:
- Cloud providers (e.g., AWS, Azure, GCP)
- Identity and access management (e.g., Okta, Google Workspace, Azure AD)
- Code repositories (e.g., GitHub, GitLab)
- Endpoint and security tools (e.g., Jamf, CrowdStrike)
- On-Premises Data Centres
The goal: Minimize manual uploads by connecting all relevant systems for real-time evidence collection.
3. Ensure Real-Time Control Monitoring
Choose platforms that continuously monitor and alert you to control failures, misconfigurations, or risks—before your auditor does. This allows you to stay proactive and compliant between audits.
Bonus: Look for tools with customizable dashboards, automated alerts, and daily compliance scores.
4. Evaluate Security & Data Privacy
Ironically, your compliance platform should itself be secure and compliant. Confirm that the vendor:
- Has its own SOC 2 Type II certification
- Offers end-to-end encryption and secure data hosting
- Complies with GDPR or other relevant regulations
- Provides audit trails and user activity logs
5. Assess Usability and Support
Even the most powerful tool won’t help if it’s too complex for your team to use. Look for solutions that offer:
- A clean, intuitive user interface
- Guided setup or implementation support
- Onboarding services and compliance experts
- Dedicated customer success managers
6. Consider Scalability and Long-Term ROI
If you plan to expand your security certifications or enter regulated markets, make sure the platform supports:
- Multiple frameworks (e.g., ISO 27001, PCI-DSS, HIPAA)
- Vendor risk assessments
- Enterprise reporting and audit trail history
- Collaboration across multiple business units or subsidiaries
Summary Checklist
| Criteria | What to Look For |
| SOC 2 Framework Support | Pre-built controls, policy templates |
| Integrations | Cloud, HR, IAM, code, security tools |
| Continuous Monitoring | Real-time alerts, compliance dashboards |
| Security & Privacy | SOC 2 certified vendor, encryption, GDPR compliance |
| Usability & Support | Guided setup, expert advice, responsive CS |
| Scalability | Multi-framework support, cross-team collaboration |
Choosing the right tool is a foundational step in building a resilient, audit-ready organization. A strong SOC 2 compliance platform doesn’t just help you pass an audit—it makes compliance management a sustainable, efficient, and value-driven part of your business.
Conclusion & Next Steps
SOC 2 Type II compliance is no longer optional—it’s a business requirement. Whether you’re selling into the enterprise market, managing sensitive customer data, or simply building trust, a strong compliance posture is essential.
The good news? Preparing for a SOC 2 audit doesn’t have to drain your time and resources. With smart planning, automation, and focused documentation, you can achieve audit readiness in half the time—while strengthening your overall security and operational resilience.
To get started:
- Run a readiness assessment to identify gaps
- Standardize your documentation early
- Invest in automation to reduce manual effort
- Stick to a 90–180 day roadmap for faster results
Compliance doesn’t have to be a burden. Done right, it becomes a competitive advantage—one that accelerates trust, unlocks enterprise deals, and future-proofs your organization.