This wasn’t a case of zero-day surprise. The threat was known, the patch existed, and the risk was clear. But slow action, siloed communication, and scattered response processes allowed the damage to spread. The MOVEit breach showed, once again, that knowing your risks isn’t enough—acting on them fast is what matters.
Many organizations face the same struggle. Risk teams identify threats, assign scores, and publish reports. Meanwhile, incident responders work in firefighting mode—reacting to alerts without context. These two functions rarely speak the same language, and that disconnect causes delays, confusion, and missed priorities.
To fix this, organizations must connect risk to response. By integrating risk data into incident workflows, teams can prioritize by impact, respond faster, and remediate more effectively. This approach doesn’t just reduce dwell time—it protects what matters most.
In this article, we’ll show how to bridge the gap. You’ll learn why traditional risk practices fall short, and how a connected, integrated response model leads to faster, smarter resolutions.
The Siloed State of Risk and Response
Many organizations treat risk management and incident response as separate disciplines. Risk teams focus on identifying vulnerabilities, scoring threats, and producing reports for audits and governance. They use tools like risk registers, compliance dashboards, and periodic assessments. Meanwhile, incident response teams operate in a different world—chasing alerts, containing threats, and restoring systems under pressure.
This separation creates serious problems. Risk teams often lack visibility into how their assessments impact day-to-day operations. Their findings might stay buried in spreadsheets or slide decks, untouched until the next audit. On the other side, response teams make decisions based on technical severity or alert volume, not on which systems or threats carry the highest business impact.
This siloed approach leads to several common issues:
- Delayed Response to Known Risks: Even when the risk is documented—like in the MOVEit breach—response teams may overlook it if it doesn’t surface through their own tools.
- Poor Prioritization: Response teams may patch a medium-risk system before a high-risk one simply because it triggered an alert first.
- Redundant Work and Alert Fatigue: Security teams often chase alerts that don’t matter while missing the ones that do.
- Lack of Accountability: Without shared workflows, no one owns the handoff between identifying risk and remediating it.
These gaps are costly. They slow down remediation, weaken defenses, and increase the likelihood of breach escalation. When security teams respond without context—and risk teams assess without follow-through—organizations lose the ability to act with clarity and speed.
To fix this, organizations need to connect these two functions. They must break down silos and build a pipeline where risk drives response—not just on paper, but in daily operations.
Why Risk-to-Response Integration Matters
When organizations integrate risk management with incident response, they shift from reacting to threats to managing them with purpose. This integration enables teams to make faster, smarter decisions based on the true impact of each incident—not just its technical severity.
1. Faster, Risk-Aware Decision-Making
Security teams face hundreds, sometimes thousands, of alerts daily. Without context, they must treat each one as urgent or guess at what matters. But when alerts are enriched with risk data—like asset criticality, compliance impact, or threat exposure—teams can triage intelligently. They focus on incidents that pose the greatest risk to the business, not just those that hit first.
2. Reduced Dwell Time
When responders know which vulnerabilities or systems carry the most weight, they can act faster. Instead of hunting for context after detection, they receive it in real time. This shortens the time from detection to containment—a key factor in limiting damage during an active incident.
3. Business-Aligned Response
A vulnerability in a test server might be low risk. The same issue in a production payment system could be catastrophic. Without business context, both may look identical to a scanner. Integrating risk assessments into response workflows ensures the right incidents receive the right level of attention—based on their potential to disrupt operations or violate regulations.
4. Better Use of Resources
When teams prioritize effectively, they reduce time spent on low-value alerts and repetitive manual tasks. This improves efficiency, prevents burnout, and makes it easier to scale response capabilities.
Bottom line: Integration turns raw alerts into informed action. It aligns teams, speeds up response, and helps organizations protect what truly matters
Key Components of Risk-to-Response Integration
Building a bridge between risk management and incident response doesn’t require reinventing the wheel—but it does require the right structure. Integration succeeds when you bring together tools, data, and workflows in a way that supports real-time, risk-informed action.
1. Shared Data Sources
Integration begins with visibility. Both risk and response teams need access to the same up-to-date data. This includes:
- Asset inventories with business-critical tagging
- Vulnerability data with contextual risk scores
- Threat intelligence feeds that map risks to active exploits
- Compliance obligations linked to specific systems or data types
When these inputs flow into a unified platform—such as a SIEM or a GRC dashboard—they provide a common language for decision-making.
2. Risk-Informed Playbooks
Most incident response teams use playbooks to guide their actions. But if those playbooks trigger based only on severity (e.g., CVSS scores or alert frequency), they miss the bigger picture.
Modern playbooks should include:
- Conditional logic tied to business impact (e.g., “Is this a regulated system?”)
- Dynamic prioritization based on asset risk profile
- Escalation rules that consider both threat severity and exposure
This ensures that every response is tailored not just to the threat, but to the organization’s unique risk landscape.
3. Automation and Orchestration
Manual triage and investigation slow down response. Automation can enable:
- Alert enrichment with risk data
- Risk-based ticket routing
- Pre-approved remediation actions for known low-risk scenarios
Automation doesn’t replace human judgment—it frees up time for analysts to focus on complex, high-risk incidents.
4. Feedback Loops
Integration isn’t a one-way street. Effective programs include feedback loops where:
- Incident outcomes inform risk scores (e.g., repeated exploits increase threat likelihood)
- Post-incident reviews update controls and refine playbooks
- Lessons learned from response efforts improve risk models
This continuous learning process strengthens both risk posture and operational response over time.
Implementation Blueprint
Integrating risk with incident response doesn’t have to be a massive overhaul. You can start small, prove value quickly, and scale gradually. Here’s a five-step roadmap to help you implement a connected, risk-aware incident response framework.
Step 1: Map Risk Sources to Detection Capabilities
Start by identifying where your risk data lives and how it can inform detection:
- Link CVSS scores, threat intelligence, and asset criticality to your SIEM rules.
- Tag high-risk assets and systems in your asset inventory.
- Connect compliance requirements (e.g., PCI, HIPAA) to relevant infrastructure.
Goal: Ensure alerts and detection rules consider not just technical factors, but business risk and regulatory context.
Step 2: Prioritize Based on Business Impact
Not all systems are equal. A breach on a sandbox server is inconvenient. A breach on a payroll system is a crisis.
- Use a scoring model that includes business criticality, data sensitivity, and external exposure.
- Highlight “crown jewel” assets in your detection and response platforms.
- Use impact scoring to inform alert triage and escalation paths.
Goal: Make sure response teams don’t treat all incidents the same—and focus on what truly matters.
Step 3: Build or Update Playbooks
Your playbooks should do more than react to alerts—they should react based on risk context.
- Add decision points based on asset risk level, system ownership, and threat history.
- Include conditional actions (e.g., notify legal for regulated data, quarantine high-risk endpoints automatically).
- Design modular playbooks that scale based on severity and impact.
Goal: Enable structured, predictable, and business-aligned responses to incidents.
Step 4: Automate Where Safe
Automation accelerates response—especially for repetitive or low-risk actions:
- Automate enrichment: Pull risk data into alerts (e.g., asset criticality, open vulnerabilities).
- Automate containment: Auto-isolate infected devices with a known, low false-positive rate.
- Automate escalation: Route high-risk incidents to senior responders with full context.
Goal: Free up analysts from manual tasks and shorten time to resolution without sacrificing control.
Step 5: Monitor, Refine, and Repeat
Integration is not a one-time project. Create feedback loops:
- Conduct post-incident reviews to assess response quality and improve playbooks.
- Update risk scores based on real-world outcomes (e.g., exploit frequency, patch effectiveness).
- Measure performance: Track metrics like time to triage, remediation rates, and risk-adjusted response coverage.
Goal: Continuously improve both risk accuracy and response effectiveness through iteration.
How Spog.AI Powers Risk-to-Response Integration
Achieving true integration between risk and incident response requires more than just stitching together dashboards—it demands a platform that understands both the business context and the operational urgency of security events. Spog.ai is built to deliver exactly that.
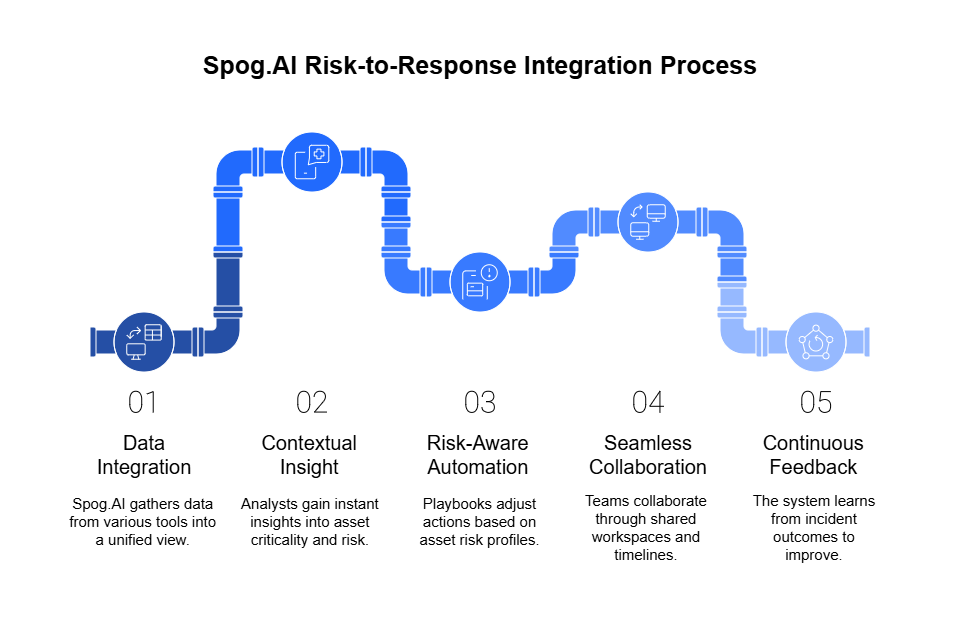
Unified Context in a Single Pane
Spog.ai brings together data from disparate tools—vulnerability scanners, asset inventories, SIEMs, GRC systems, and ticketing platforms—and presents it in a unified incident command center. This single interface shows:
- The affected asset’s criticality
- Relevant risk scores and business impact
- Historical incident context
- Associated compliance obligations
Analysts no longer need to swivel between tools or dig through PDFs and spreadsheets. With Spog.ai, they get instant, contextual insight at the moment of triage.
Risk-Aware Automation and Response Playbooks
Spog.ai doesn’t just alert—it acts. Its intelligent playbooks adjust actions based on:
- Asset risk profiles (e.g., crown jewels vs. dev environments)
- Threat severity and exploitability
- Regulatory sensitivity of impacted systems
For example, an alert involving a high-risk, regulated asset can automatically trigger:
- Quarantine workflows
- Legal and compliance notifications
- Enhanced logging for audit readiness
This dynamic response model ensures that remediation aligns with both technical urgency and business risk.
Seamless Collaboration Between Teams
Security, IT, and risk teams often operate in silos. Spog.ai bridges these gaps through:
- Shared workspaces and timelines for incidents
- Automated assignment of tasks to relevant owners
- Centralized evidence tracking and post-incident review tools
This fosters cross-functional accountability and ensures that risk insights lead to measurable action.
Continuous Feedback and Risk Calibration
Every incident resolved in Spog.ai contributes to a smarter, more adaptive system. The platform learns from:
- Response outcomes
- Missed alerts
- Reopened cases
It uses this feedback to fine-tune risk scoring, prioritize future alerts more accurately, and suggest playbook improvements—powering a living, learning security response engine.
The Bottom Line
Spog.ai empowers security teams to move from reactive firefighting to strategic, risk-aligned response. It connects the dots—data, teams, tools, and decisions—so that no risk assessment sits idle, and no response happens without purpose.
Conclusion
Knowing your risks isn’t enough. The real challenge lies in turning that knowledge into timely, effective action. As breaches like MOVEit have shown, even well-documented vulnerabilities can cause massive damage if teams can’t act fast—and act smart.
Traditional, siloed approaches to risk and response leave too much room for delay, miscommunication, and missed priorities. Risk teams assess threats. Response teams fight fires. But without integration, their efforts remain fragmented—and the organization remains exposed.
By connecting risk assessments directly into incident response workflows, organizations gain more than just speed. They gain clarity. They respond not just to alerts, but to the alerts that matter most. They align their actions with business impact, reduce dwell time, and improve outcomes across security, compliance, and operations.
Platforms like Spog.ai make this possible. By unifying tools, enriching alerts with risk context, and enabling dynamic response, Spog.ai helps teams close the loop—from detection to decision to resolution.
The path forward is clear: break the silos, integrate your workflows, and let risk drive response. Organizations that make this shift won’t just respond faster—they’ll respond smarter, and safer.