Imagine installing the latest high-tech locks on your front door. You feel secure—until you realize your teenager leaves the garage wide open every night. That’s what happens when your stack protects the edge but ignores what’s inside. You secure the front, but the back stays exposed.
If your asset inventory is outdated, your threat models are stale, and your environment map hasn’t kept up, your tools protect a version of your system that no longer exists.
This is where most security programs fall short. They collect data, but don’t connect it. They alert, but don’t prioritize. They see, but don’t understand.
The 5 Most Common Hidden Backdoors in Enterprise Environments
You may think your environment is locked down, but attackers know better. They look for the cracks—small oversights, forgotten systems, and gaps between policy and practice. Here are five of the most common places those cracks appear, even in organizations that are “doing everything right.”
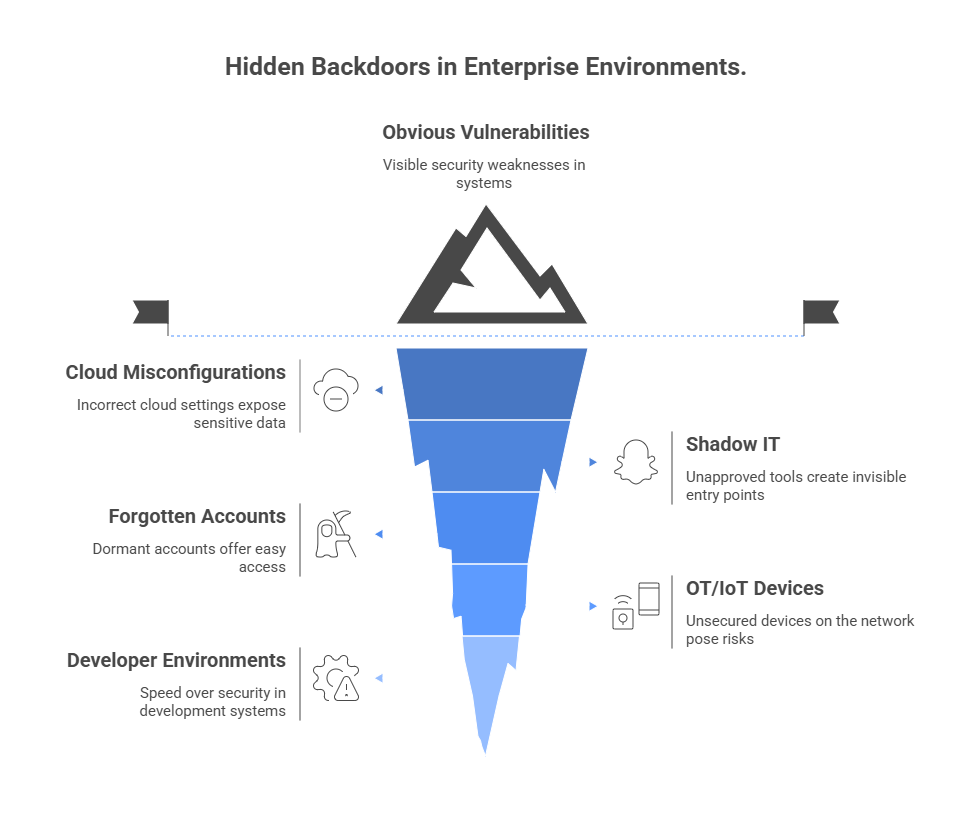
1. Cloud Configuration Drift: Complexity is the Enemy of Control
Public cloud platforms offer agility, scalability, and a dizzying array of features—but they also introduce sprawling, fast-changing attack surfaces. The sheer number of settings across IAM, storage, and compute creates a minefield of hidden risks.
Most security teams don’t have a real-time picture of cloud configuration. One engineer adjusts permissions for a quick fix. Another leaves a diagnostic service exposed. These small actions accumulate. Before you know it, you’re not protecting infrastructure—you’re protecting assumptions about it.
Misconfigurations aren’t rare—they’re normal. And in a dynamic environment, every new commit or deployment can open a door you didn’t know existed.
2. Shadow IT: Risk by Convenience
Technology democratization has made it easier than ever for teams to spin up tools that solve their own problems. The marketing team finds a new analytics app. Sales starts trialing a third-party CRM. Devs deploy a microservice on their personal cloud account. None of these steps require security approval—and that’s the problem.
Shadow IT isn’t malicious. It’s often a sign that centralized IT can’t keep up. But these unsanctioned tools create invisible entry points into your infrastructure. When they fail or get breached, the blast radius doesn’t stay local. Your organization’s brand, data, and domain are still on the hook.
The most dangerous system is the one you don’t even know exists.
3. Forgotten Accounts: Ghosts in the Machine
Accounts are easy to create—and surprisingly hard to kill. Contractors come and go. Admins set up test logins and never remove them. Internal transfers leave orphaned access lingering in unexpected places. Over time, your identity directory becomes less of a ledger and more of a graveyard.
These dormant accounts don’t generate alerts. They don’t show up in daily dashboards. But they can offer attackers a golden ticket—credentials with elevated privileges, often lacking MFA, just waiting to be reactivated or exploited.
Security isn’t just about what’s active. It’s about what’s left behind.
4. OT and IoT: The Unseen Layer of Risk
Modern enterprises run on far more than laptops and servers. Behind the scenes are HVAC controllers, smart TVs, factory floor PLCs, badge readers, IP cameras, and yes—smart coffee machines. Many of these systems were designed for uptime, not defense. Few follow patch cycles. Fewer still support modern security controls.
What makes these devices dangerous isn’t just their exposure—it’s the illusion that they’re harmless. They live on the same network as your business-critical systems. They’re often ignored in audits. And they quietly accumulate risk until someone takes notice.
By then, it’s usually too late.
5. Developer Environments: Where Speed Outpaces Security
Developers build the future—but sometimes leave the backdoor open while doing it. In the name of speed, secrets get hardcoded, SSH ports stay open, and CI/CD tools become soft targets with broad access across the infrastructure.
It’s not negligence—it’s a natural result of asking engineers to move fast without embedding security into their workflow. Development systems aren’t just another asset class. They are powerful, privileged, and deeply integrated. Which also makes them extremely attractive to attackers.
An exposed GitHub token or misconfigured Jenkins instance may not sound like a headline—but it’s often how major breaches begin.
None of these risks are introduced deliberately. They grow in the spaces between teams, between tools, and between assumptions. That’s why visibility matters. Not the kind you get from a single dashboard or log stream, but deep, contextual awareness of how your environment is really operating.
Attackers don’t need a zero-day. They need you to miss something. These backdoors are proof that even the most advanced stacks can be undone by what no one’s looking at.
So … How Do You Actually Find the Backdoor?
This isn’t about paranoia. It’s about precision. You can’t secure what you can’t see—and fragmented visibility is the enemy of resilience. Backdoors don’t always look like malware or exploits. Often, they’re the byproduct of overlooked systems, broken processes, and siloed data.
Finding them starts with pulling everything together. Not into 50 dashboards, but one clear, correlated view. The future of defense lies in platformization—not more tools, but smarter integration.
According to a joint survey by IBM and Palo Alto Networks, over half (52%) of executives say fragmented security solutions are limiting their ability to respond to threats. But among organizations that have adopted a platform-based approach, 75% believe better integration across security, cloud, AI, and IT platforms is critical.
The research reveals a growing realization: layering on new tools in response to evolving threats isn’t scaling. It’s slowing teams down, introducing inefficiencies, and driving up costs. In contrast, a platformized security strategy improves response speed, reduces operational drag, and enhances protection—without increasing complexity.
Source- IBM
If resilience is your goal, visibility is your starting point—and platformization is how you get there.
1. Rebuild—and Centralize—Your Asset Inventory
An asset inventory isn’t just a list. It’s your map of reality. But for most orgs, that map lives in six places and updates in none of them.
You need one source of truth—automated, dynamic, and platform-driven. That means continuously discovering:
- Cloud resources and misconfigurations
- Domains, subdomains, and exposed services
- SaaS tools used across departments
- Active and dormant user accounts
- Network-connected devices from laptops to lightbulbs
Unifying these into a platform—not a spreadsheet—means you can correlate asset visibility with alerting, policy enforcement, and threat posture. Security is no longer a guessing game.
2. Model Threats from a Unified Perspective
Threat modeling gets more powerful when it draws from unified asset and identity data. Otherwise, you’re building scenarios around assumptions, not reality.
When you simulate attacker paths, tools like MITRE ATT&CK or BloodHound are essential—but so is having all your telemetry in one place. You want to know:
- Which identities have excessive privileges
- What data is most exposed
- Which cloud components lack guardrails
- What detection gaps exist across environments
With a unified data layer, threat modeling becomes less of a thought experiment—and more of a real-time risk evaluation.
3. Run Purple Team Exercises That Map to Your Stack
Cross-team simulations are great, but their impact doubles when they feed into a platform that contextualizes the results.
When your red team simulates an exploit and the blue team observes the response, you don’t just want scattered logs and screenshots—you want the attack path visualized end-to-end, linked to asset data, user behavior, and control coverage. That’s only possible if the stack is stitched together.
A unified platform gives you the clarity to act faster and fix smarter. Without it, every lesson learned stays locked in someone’s notes or slides.
4. Analyze Logs Through a Correlated Lens
Backdoors don’t always ring alarm bells. Most blend into the noise of normal operations—unless your logs speak to each other.
A unified platform helps you correlate across:
- IAM logs (suspicious logins)
- Endpoint behavior (unexpected processes)
- Network data (unusual destinations)
- Cloud telemetry (sudden privilege escalations)
Alone, each of these signals might look benign. Together, they tell a story. Without a centralized view, that story gets lost.
5. Track Exceptions Like Inventory—With Built-In Expiry
One of the most common backdoor creators? Temporary exceptions that never get rolled back.
Permissions granted for a sprint. Firewall rules opened for a vendor demo. Admin roles added “just for now.” Without a unified change tracking layer, these get forgotten—until they’re exploited.
A central platform can enforce policy-level expirations, prompt reviews, and surface lingering risks. You don’t need 20 workflows to fix this—you need one platform that remembers what people forget.
Unification Is the Real Security Upgrade
Backdoors thrive in fragmentation. The more tools you use without connecting them, the more places you create for risk to hide.
Finding hidden entry points isn’t just a matter of process—it’s a matter of perspective. When your data lives in silos, you miss the context. When it lives in one place, everything sharpens.
The organizations moving fastest aren’t adding more tools. They’re aligning the ones they already have—through a unified platform that turns logs into answers, assets into accountability, and alerts into action.
Because in modern security, visibility isn’t a dashboard—it’s your defense strategy.
Real-World Examples of Visibility Gaps
When breaches happen, it’s rarely because organizations didn’t have security tools. It’s because those tools didn’t see the whole picture. Whether it’s an overlooked device, an unsanctioned app, or a forgotten access point, attackers thrive in the blind spots.
Here are real-world examples where fragmented visibility cost organizations dearly.
1. TalentHook (2025): Misconfigured Cloud Storage Exposes 26 Million Resumes
In a significant data breach, TalentHook, a recruitment software firm, left an Azure Blob storage container misconfigured, resulting in the exposure of nearly 26 million resumes. These documents contained sensitive personal information such as full names, email addresses, phone numbers, educational backgrounds, employment histories, and other professional details of U.S. citizens. Cybersecurity experts warn that such misconfigurations are increasingly common and pose significant security risks.
2. Qantas (2025): Social Engineering Breach via Third-Party Call Center
Qantas experienced a cyberattack that exposed the personal data of up to 6 million customers. Hackers exploited an offshore IT call center using social engineering techniques, accessing third-party systems and bypassing security measures such as multi-factor authentication. This incident highlights the vulnerabilities associated with human factors and third-party systems in cybersecurity.
3. Snowflake Data Breach (2024): Credential Theft Leads to Massive Data Exposure
In 2024, Snowflake Inc., a cloud-based data warehousing platform, suffered a large-scale cybersecurity incident involving unauthorized access to customer cloud environments. The breach affected numerous high-profile clients, including AT&T, Ticketmaster, and Santander Bank. Attackers exploited stolen credentials, many lacking multi-factor authentication, to access customer instances directly. This breach underscores the risks associated with insufficient access controls and the importance of integrated security measures.
4. Rockerbox (2025): Unprotected Database Exposes 250,000 Records
Nearly 250,000 records containing sensitive personal data were exposed in a major data breach involving Rockerbox, a Texas-based tax credit consulting firm. A publicly accessible and unprotected database totaling 286.9 GB was discovered, containing names, addresses, Social Security numbers, and employment-related tax documents. The breach highlights the dangers of inadequate data protection and the need for continuous monitoring of data repositories.
Visibility is the Foundation of Cybersecurity
Cyber threats are evolving—but so are the gaps within most enterprise environments. As we’ve seen, it’s rarely the lack of tools that leads to a breach. It’s the absence of unified visibility. Misconfigured cloud storage, unmanaged shadow IT, forgotten access privileges, and overlooked endpoints aren’t just oversights—they’re attack paths. And they thrive in environments where security data lives in silos.
That’s why the future of cybersecurity isn’t about adding more tools. It’s about making the ones you already have work together—sharing context, reducing noise, and driving decisions with clarity.
SPOG.AI unifies your entire security stack—across clouds, identities, endpoints, and data—into a single, impact-aware view. It goes beyond aggregation by layering in risk prioritization, attack path correlation, and actionable insights across your tools. No more swivel-chair investigations. No more dashboards that tell half the story.
With SPOG.AI, security teams don’t just see more—they understand more, act faster, and reduce noise without losing control.
Because real visibility isn’t about collecting data—it’s about connecting it.
