At the same time, organizations must navigate an equally pressing priority: maintaining compliance with regulatory standards and internal policies. Too often, remediation efforts and compliance validation are treated as separate, sequential processes—security teams focus on containing threats, while compliance teams independently gather evidence and align actions to frameworks such as ISO 27001, SOC 2, HIPAA, or PCI-DSS. This fragmented approach creates blind spots, duplicated effort, and missed opportunities to reinforce trust.
By unifying remediation and compliance within an integrated incident response framework, organizations can close these gaps. Embedding compliance checks directly into remediation workflows ensures that every response not only strengthens security posture but also contributes to continuous compliance. This alignment transforms incident response from a purely reactive firefight into a coordinated, strategic process that accelerates recovery, reduces audit fatigue, and builds operational resilience.
The Current Gaps in Remediation and Compliance
Despite advances in detection and response tools, many organizations still struggle with fragmented processes that weaken both security and compliance efforts. These gaps often stem from siloed teams, tool sprawl, and the lack of real-time alignment between incident remediation and compliance validation.
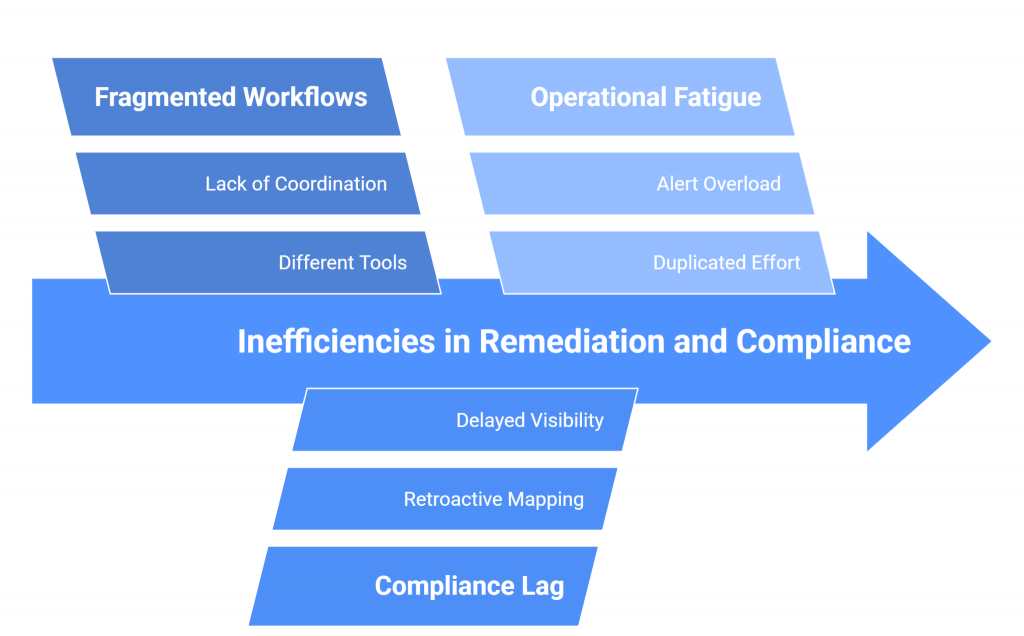
1. Fragmented Workflows
Incident response typically requires coordination across SOC analysts, IT operations, and compliance officers. Yet each group often relies on different tools and workflows. Analysts may use one platform for detection, IT teams another for patching, and compliance staff a separate system for documentation. This fragmentation creates inefficiencies, slows response times, and increases the chance of critical steps being missed.
2. Compliance Lag
Compliance validation usually trails behind incident response. After remediation is complete, compliance teams must retroactively map actions to relevant controls and prepare evidence for audits. This after-the-fact approach delays visibility into whether regulatory obligations are being met in real time, leaving organizations exposed to compliance risks during active incidents.
3. Operational Fatigue
Security teams already face alert overload and must filter through noise to identify the most pressing threats. When remediation and compliance activities are not coordinated, analysts end up duplicating effort—resolving incidents once for security purposes, and then again to produce compliance evidence. This duplication not only drains resources but also contributes to burnout and reduced overall effectiveness.
Principles of an Integrated Incident Response Framework
To close the gaps between remediation and compliance, organizations need a framework that unifies both processes under a single, coordinated approach. An integrated incident response framework emphasizes visibility, prioritization, and automation—helping teams move faster while staying aligned with regulatory obligations.
1. End-to-End Visibility
A fragmented view of incidents is one of the biggest barriers to effective response. Analysts often spend precious minutes pulling data from multiple systems, while compliance officers search for evidence after the fact. End-to-end visibility consolidates detection, response, and compliance activities into a single pane of glass. This means:
- SOC teams can see the full lifecycle of an incident, from detection through remediation.
- Compliance staff can track whether each remediation step meets regulatory requirements without chasing down separate logs.
- Executives gain high-level dashboards that show both risk reduction and compliance status at a glance.
This level of visibility reduces blind spots, cuts down on duplicate effort, and ensures everyone is working from the same real-time information during an incident.
2. Impact-Based Prioritization
In most environments, teams face far more alerts than they can realistically investigate. Without prioritization, minor issues consume attention while critical threats linger. An integrated framework uses impact-based prioritization to ensure that incidents with the highest potential harm—especially those tied to compliance obligations—rise to the top. For example:
- A phishing attempt targeting a test account may rank low priority.
- A similar attempt targeting a system storing regulated health data (HIPAA) or payment data (PCI-DSS) should be escalated immediately.
This approach not only reduces risk exposure but also ensures remediation actions directly support compliance objectives, improving audit readiness while strengthening security.
3. Automation and Orchestration
Manual processes are slow and error-prone, especially in high-stress scenarios. Automation reduces these risks by executing predefined playbooks for common incidents—such as isolating compromised endpoints, resetting credentials, or applying patches. Compliance checks can be embedded in the same playbooks, so evidence is automatically collected and logged as part of the workflow.
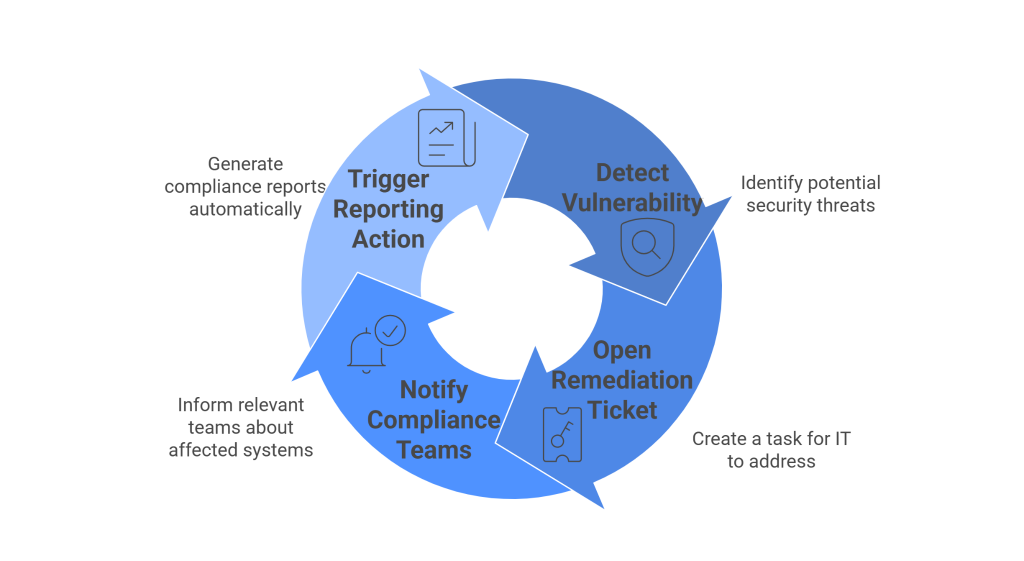
Orchestration ties these automated tasks together across teams and tools. For example, when a vulnerability is detected, an orchestrated workflow can:
- Open a ticket in IT’s system for remediation.
- Notify compliance teams that a regulated system is affected.
- Trigger a reporting action to demonstrate compliance with relevant standards.
This coordination accelerates response, reduces human error, and ensures compliance validation happens in parallel with remediation rather than as an afterthought.
Linking Remediation to Compliance Controls
An integrated incident response framework does more than contain threats—it ensures every remediation step also reinforces compliance obligations. By connecting remediation actions directly to compliance controls, organizations reduce audit fatigue, improve transparency, and demonstrate continuous alignment with regulatory requirements.
1. Control Mapping
The first step is to align incidents with the right compliance frameworks. Each event—whether a vulnerability, misconfiguration, or insider threat—should be mapped to relevant controls in standards like NIST CSF, ISO 27001, SOC 2, HIPAA, or PCI-DSS.
- Example: A failed login attempt from an unusual location could be mapped to identity and access management (IAM) controls.
- Benefit: This mapping makes it clear which compliance requirement is being tested during an incident, ensuring that remediation is both technically sound and audit-ready.
2. Continuous Compliance Validation
Traditional compliance reviews happen after incidents are resolved, often weeks or months later. With integration, validation occurs in real time. As remediation steps are executed, systems can automatically verify whether the actions meet compliance requirements.
- Example: When patching a critical vulnerability, the system can confirm that patching deadlines set by PCI-DSS are met.
- Benefit: This eliminates lag between incident response and compliance assurance, closing gaps that auditors or regulators might otherwise flag.
3. Policy-Driven Remediation
Standardizing remediation through policy-based playbooks ensures consistency across teams and incidents. Instead of leaving responses to manual decision-making, organizations can design workflows that are pre-approved against compliance standards.
- Example: A playbook for handling lost devices could include automated data wipe, access revocation, and evidence logging steps that align with GDPR or HIPAA requirements.
- Benefit: This reduces guesswork, accelerates decision-making under pressure, and ensures every action is compliant by design.

Building Integrated Workflows
Once remediation and compliance are linked at the control level, the next step is to operationalize them through integrated workflows. These workflows ensure that incident response, remediation, and compliance activities flow together seamlessly, reducing delays and eliminating the need for manual handoffs.
1. Unified Playbooks
Playbooks are at the heart of integrated workflows. They define step-by-step actions that respond to specific types of incidents—while also embedding compliance checks along the way.
- Example: A ransomware response playbook may include isolating infected endpoints, notifying affected stakeholders, restoring from backup, and simultaneously collecting compliance evidence for regulations like HIPAA or GDPR.
Instead of treating compliance as a separate process, each remediation action is already aligned with the organization’s regulatory obligations.
2. Cross-Team Collaboration
Incident response touches multiple teams: SOC analysts, IT operations, compliance officers, and business leaders. Without integration, each group operates in its own silo, causing delays and miscommunication. Integrated workflows bridge these gaps by providing a shared view of the incident lifecycle.
- Example: When an endpoint is quarantined, SOC analysts see the technical details, IT receives an automated remediation ticket, and compliance staff are notified of the control being addressed—all from the same system.
Collaboration becomes proactive rather than reactive, reducing friction and speeding resolution.
3. Metrics and Reporting
Integrated workflows should produce metrics that highlight both operational efficiency and compliance coverage. These metrics help organizations continuously improve and stay audit-ready.
- Key Metrics to Track:
- Mean Time to Remediation (MTTR): How quickly incidents are resolved.
- Compliance Coverage: Percentage of incidents mapped to regulatory controls.
- Audit Readiness: Evidence automatically collected during response versus manual collection later.
Leadership gains visibility into the value of incident response not only for security but also for compliance assurance, making it easier to justify investments and demonstrate resilience.
Benefits of Unified Remediation and Compliance
Bringing remediation and compliance together within an integrated incident response framework offers tangible advantages. It transforms how teams respond to threats, reduces operational overhead, and ensures organizations are always audit-ready.
1. Faster, More Accurate Incident Response
Integrated workflows remove the delays and errors that often result from juggling multiple tools and processes. By consolidating remediation and compliance checks into a single workflow, teams can act decisively and consistently during incidents.
For instance, a misconfigured cloud storage bucket exposing sensitive data can be detected, remediated, and logged for compliance automatically within minutes. This not only reduces the window of exposure but also ensures the response aligns with regulatory requirements from the start. The combination of speed and accuracy gives organizations a stronger defense against both technical and regulatory risks.
2. Reduced Audit Preparation Effort
Audit readiness has traditionally required weeks of effort to compile logs, reports, and evidence. With integrated systems, evidence is gathered as part of the incident response process itself, meaning every remediation action is automatically linked to the appropriate compliance control.
For example, when a vulnerability is patched, details such as the patch version, timestamp, and control mapping are captured instantly. This eliminates the stressful pre-audit scramble, reduces the burden on staff, and provides auditors with verifiable, real-time records of compliance. Over time, organizations build a living evidence base that simplifies both internal reviews and external certifications.
3. Lower Operational Costs with Automation
Manual, repetitive tasks consume valuable analyst time and strain compliance staff, especially in environments flooded with alerts. Automation addresses this by executing remediation steps, updating tickets, notifying stakeholders, and collecting compliance evidence without constant human intervention.
Instead of requiring a dedicated analyst to log each action, an automated workflow ensures consistency while scaling across hundreds or thousands of incidents. This reduces the need for additional headcount and lowers the cost of maintaining both security operations and compliance programs. Freed from administrative tasks, teams can focus on higher-value activities like threat hunting, policy refinement, and strategic planning.
4. Stronger Alignment Between Security and Business Goals
When remediation is tied directly to compliance outcomes, organizations gain more than just technical protection—they reinforce customer trust, safeguard brand reputation, and reduce legal exposure. Executives and stakeholders can see that every action taken during incident response contributes to broader business objectives such as regulatory adherence, risk reduction, and operational resilience.
A healthcare provider responding to a data breach, for example, can demonstrate HIPAA-compliant remediation while also proving to patients that their data was quickly secured. This alignment elevates the role of security from a reactive function to a strategic partner, showing that investments in incident response drive measurable business value.
How SPOG.AI Unifies Compliance and Remediation in One Platform
SPOG.AI is designed to close the gap between incident response and compliance by delivering a single platform where remediation and regulatory alignment happen in tandem. Instead of forcing security teams, IT operations, and compliance officers to work in separate silos, SPOG.AI orchestrates their workflows into one seamless experience.
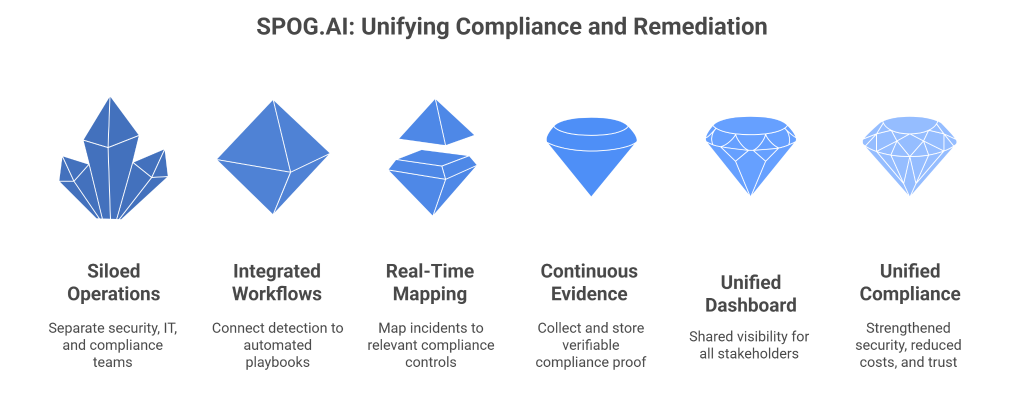
Integrated Detection-to-Remediation Workflows
SPOG.AI connects detection systems with automated playbooks that not only resolve issues but also log compliance evidence at every step. For example, when a vulnerability is detected on a regulated system, SPOG.AI can automatically trigger patch deployment, update IT tickets, and capture compliance proof—all without requiring manual intervention. This ensures that technical remediation is inseparable from compliance validation.
Real-Time Compliance Mapping
Every incident within SPOG.AI is automatically mapped to relevant controls across frameworks such as ISO 27001, SOC 2, HIPAA, and PCI-DSS. This means teams know immediately which regulatory obligations are at stake during a security event. Compliance validation happens in real time, so remediation steps are both technically effective and audit-ready from the start.
Continuous Evidence Collection
Instead of scrambling to prepare for audits, organizations using SPOG.AI benefit from continuous evidence collection. Each remediation action is timestamped, tagged, and stored as verifiable proof, building a living library of compliance records. Auditors can access these records instantly, reducing preparation time and improving trust.
Cross-Team Collaboration in a Single View
SPOG.AI provides a unified dashboard where SOC analysts, IT staff, compliance officers, and executives see the same real-time information. This shared visibility eliminates context switching and miscommunication, allowing teams to coordinate faster and with greater accuracy. Leaders gain confidence knowing that remediation and compliance are progressing hand in hand, without blind spots.
Business Value Beyond Security
By embedding compliance into remediation workflows, SPOG.AI not only strengthens security posture but also reduces operational costs and audit fatigue. Organizations can demonstrate regulatory adherence during every incident, building resilience and trust with customers, partners, and regulators—all from a single platform.
