Automating Security Questionnaires: How to Streamline Third-Party Risk Assessments
Third-party vendors play a critical role in modern business operations, but they also expand exposure to unpredictable risks. These risks often do not come under the enterprise purview and hence cannot be controlled. A common way to assess the security posture of third-party vendors, partners, and supplies is through security questionnaires. Security questionnaires are structured assessments that work both ways for vendor assessments as well for...
By kalpana v on September 29, 2025
Categories: Uncategorized

Unifying Remediation and Compliance with Integrated Incident Response
When it comes to responding to incidents, time is of the essence. The first few minutes often bring chaos—analysts must quickly switch between tools, evaluate the scope of impact, and...
Categories: Uncategorized
The Rise of Adversarial AI Attacks & AI Security Best Practices to Stop them
It’s an undeniable fact that organizations of all sizes and industries have adopted AI at a colossal scale. While AI is revolutionizing how businesses operate, it also poses major challenges...
Categories: AI

5 Reasons You Need to Move from Spreadsheets to GRC Tools for Compliance Management
For years, spreadsheets have been the go-to tool for managing governance, risk, and compliance (GRC). They’re familiar, easy to set up, and cost nothing more than a license most businesses...
Categories: #GRC
The Definitive Guide to Automated Controls Testing
Every 39 seconds, a cyberattack strikes somewhere in the world (University of Maryland). At the same time, regulators are tightening rules across industries, from finance to healthcare. Leaders can no...
Categories: #automation, #compliance

Turning Risk Registers from Static Records into Living Intelligence
For years, the risk register has been a key tool in governance, risk, and compliance (GRC) programs. But in most organizations, it still sits in spreadsheets or static forms that...
Categories: #risk, #Risk Management
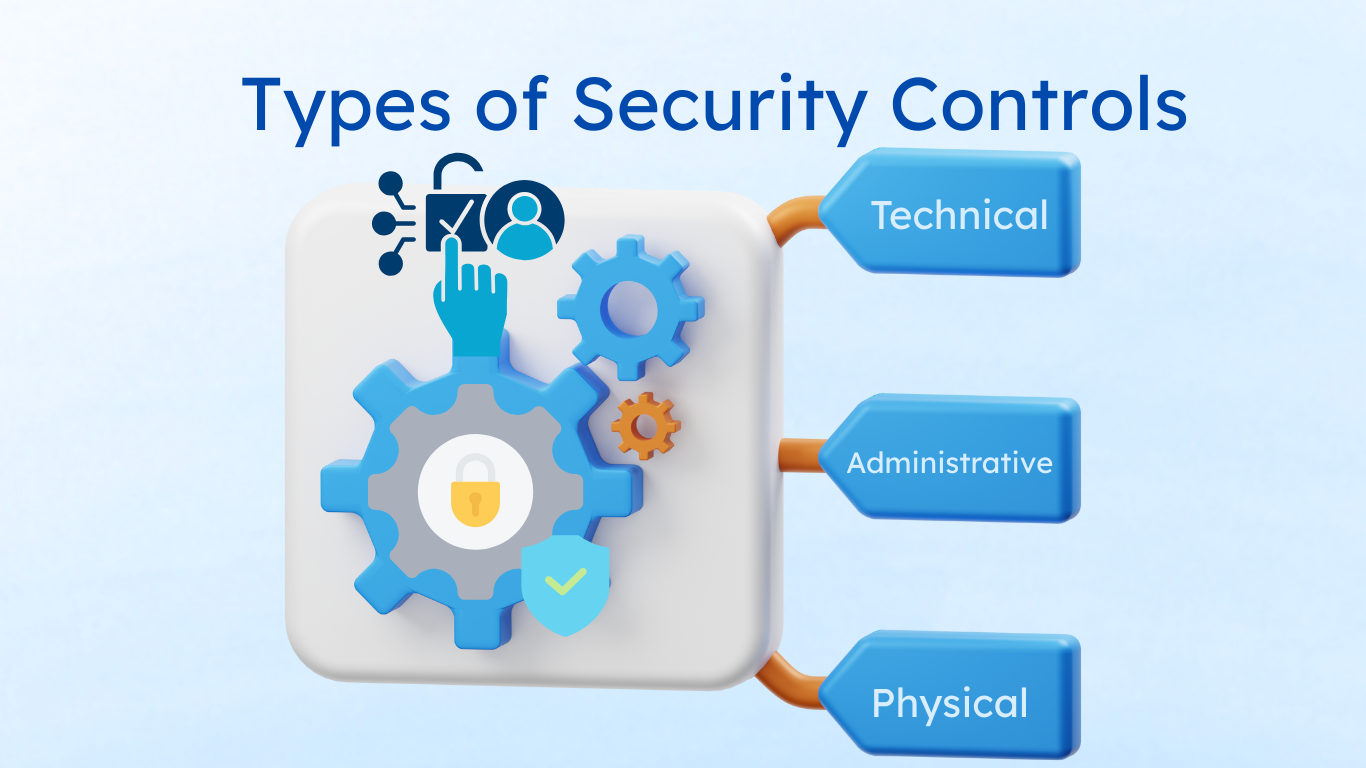
Understanding the Different Types of Security Controls (and Why They Matter)
Security controls come in many forms and levels of complexity. Organizations implement them based on their own risks, needs, and processes. But is it enough to set them up once...
Categories: #Cyber Security
The Evolution of PCI DSS: From v3.2.1 to v4.0
The Payment Card Industry Data Security Standard (PCI DSS) has long served as the global benchmark for safeguarding cardholder data and reducing the risk of breaches. First introduced in 2004,...
Categories: #automation, #compliance

Third-Party Risk Metrics: How to Track and Report
Third-party data breaches are more commonplace than ever. The majority of high-stakes data breaches in recent years have been caused by one missing link in the vendor management workflow. Take...
Categories: #Risk Management, #Vulnerability Management

Setting Up a GDPR Compliance Monitoring and Audit Program: Steps and Checklist
Achieving GDPR compliance is only the beginning, maintaining it is the real challenge. The General Data Protection Regulation (GDPR) demands that organizations not only put privacy controls in place but...
Categories: #compliance, #GDPR

How Cybersecurity Asset Management Improves Risk-Based Alerting and Threat Response
Too often, security tools treat all assets as equal. A critical alert on a decommissioned test server carries the same weight as one on a core financial system. A suspicious...
Categories: #Cyber Security

Automated Access Reviews: Strengthening Security, Simplifying Compliance
Access reviews play a key role in meeting security and regulatory standards. But many companies still handle them manually, creating risk and complexity. According to The State of Access Review...
Categories: #Cyber Security, #Risk Management

CERT-In’s 2025 Cyber Audit Policy: What It Means for India’s Security Ecosystem
On July 25, 2025, the Indian Computer Emergency Response Team (CERT-In) launched a major update to its cybersecurity audit guidelines. These new rules aim to move India’s security posture from...
Categories: #compliance, #Cyber Security

Silent Threats, Loud Consequences: Why Most Breaches Start with a Missed Signal
Introduction: The Breach That Wasn’t Loud — Until It Was The most dangerous breaches often don’t begin with a bang.They start with a blink—missed, ignored, or filed away for “later.”...
Categories: #risk, #Vulnerability Management

From CMDB to Risk Engine: Turning Asset Data into Security Decision
In May 2024, one of the most significant cloud breaches in recent memory made headlines: attackers infiltrated over 160 customer environments in the Snowflake ecosystem, affecting companies like AT&T and...
Categories: #Cyber Security, #Vulnerability Management
A Complete Guide to Third-Party Security Assessment
Third-party data breaches are on the rise. Attackers increasingly target vendors, contractors, and SaaS providers; not just because they’re easier to breach, but because they often have direct access to...
Categories: #Cyber Security, #Risk Management

Is Your Security Stack Missing True Visibility?
You’ve invested in top-tier tools—firewalls, SIEMs, XDRs, MDRs, and real-time threat intel feeds. On paper, your security stack looks solid. You’ve done everything right. But tools only work if they...
Categories: #Cyber Security

Combating Alert Fatigue for SOC Teams with Impact-Based Risk Prioritization
Security Operations Centers (SOCs) protect modern businesses from cyber threats. But instead of battling a lack of information, SOC teams often drown in it. Every day, analysts face thousands of...
Categories: #Cyber Security, #Risk Management, #Vulnerability Management
Connecting Risk and Remediation with Integrated Incident Response
In 2023, attackers exploited a known vulnerability in MOVEit Transfer—a popular file transfer tool used by governments, banks, and large enterprises. Even after the vulnerability became public, many organizations failed...
Categories: Incident Response
Are You Boardroom-Ready? A CISO’s Guide to Cyber Risk Quantification and Security Maturity Assessment
Introduction: Why “Boardroom-Ready” Matters More Than Ever Not long ago, cybersecurity was seen as a technical silo—an IT function buried deep in the infrastructure, discussed mainly in jargon and dashboards...
Categories: #Cyber Security

Top 10 Early Warning Signs of Insider Threats Every Company Should Know
Insider threats are one of the most underestimated cybersecurity risks facing organizations today. While companies often focus on defending against external attackers, the real danger might be operating quietly from...
Categories: #Cyber Security, #Vulnerability Management

Modernizing Third-Party Risk Management with Continuous Monitoring
Introduction: The Evolution of Third-Party Risk Management Businesses today rely on third-party vendors for everything from cloud services to data processing. These partners enable scale and speed—but also open the...
Categories: #risk, #Vulnerability Management

The Complete Guide to Data Center Security and Compliance (with an actionable checklist)
Hybrid data centers have become the backbone of modern enterprise IT. These environments integrate on-premises infrastructure with public and private cloud platforms, offering agility, control, and performance. But as architecture...
Categories: #automation, #Cyber Security
What is a Risk and Controls Matrix? A Beginner’s Guide
Every organization, big or small, faces uncertainty. It could be a data breach waiting to happen, a missed regulatory deadline, or risks that emerge from a third-party vendor. The hard...
Categories: #risk, #Risk Management

Designing a Comprehensive Risk Mitigation Strategy: From Assessment to Action
In February 2023, Karmak, a leading business software provider in the trucking industry, was hit by a ransomware attack. Thanks to a well-prepared incident response plan, the company acted fast....
Categories: #risk, #Risk Management
Cyber Risk in Banking: Evolving Threats and Adaptive Risk Management
Banks today work in a fast-moving, always-connected digital world. With every new API, cloud platform, third-party service, remote employee, or customer-facing app, they expand their digital presence, and their exposure...
Categories: #risk, #Risk Management, #Vulnerability Management
GRC Automation for Hybrid Infrastructure
Most companies today aren’t operating in just one environment. They’ve got systems running in the cloud, some in private data centers, and often a good chunk still sitting on on-premises...
Categories: #automation, #GRC

Cyber Risk Management Goals for a Zero-Trust World
As cyber threats grow in sophistication and scale, traditional security models that once protected corporate networks are no longer sufficient. Businesses today face ransomware attacks, insider threats, supply chain compromises,...
Categories: #Cyber Security, #Risk Management
The GRC Metrics That Actually Matter
Governance, Risk, and Compliance (GRC) functions have evolved from reactive compliance checkpoints into proactive strategic enablers. However, this evolution brings a new challenge—how do you prove the value of GRC...
How to Prepare for a SOC 2 Type II Audit in Half the Time
83% of enterprise buyers require SOC 2 compliance before vendor onboarding—making it not just a regulatory checkbox, but a mission-critical enabler of business growth and a gatekeeper for market access....
Categories: #compliance, #SOC2

What to Include in a High-Impact Compliance Report (With Examples)
Think of a compliance report like a routine health check-up for your organization. It might not be the most exciting appointment on the calendar, but it’s essential. Just as a...
Categories: #automation, #compliance

10 Common Gaps in Enterprise Risk Assessments—and How to Close Them
Many organizations treat risk assessments as annual checklists, missing the dynamic threats that truly matter. This guide dives into the top 10 gaps that weaken enterprise risk assessments—from inconsistent scoring...
Categories: #risk, #Risk Management

GRC Platform Selection Guide: What to Look for Based on Your Maturity Level
The GRC (Governance, Risk, and Compliance) technology landscape is vast. It touches nearly every part of a company’s operations—from policy management and control alignment to risk tracking and data classification....
Categories: #automation, #compliance, #GRC
Cyber Security Regulatory Compliance in India: What You Need to Know
Introduction: When Compliance Blocks Market Entry Sometimes, a region’s regulatory compliance rules block businesses from entering a market. That’s exactly what happened with WhatsApp Pay in India. Despite having hundreds...
Categories: #compliance, #CSCRF, #DDPA

Cybersecurity Risk Assessment in Banking: A Strategic Guide with Risk Matrix Templates
Banks today operate in a high-stakes environment, managing sensitive financial data, digital customer interactions, and a growing portfolio of online services. These innovations, while necessary, have dramatically increased their exposure...
Categories: #risk, #Risk Management
The Need for Hybrid GRC Integrations
“Just connect the API.” It’s something that we commonly hear in GRC automation—and one of the least useful if you're dealing with legacy systems. Many Governance, Risk, and Compliance (GRC)...
Categories: #automation, #compliance
Risk Management vs Compliance Management: Which Should Be Your Priority?
Stuck Between Risk and Compliance? That’s the Real Risk. Discover why treating them as rivals is holding your organization back—and how smart teams use both to fuel resilience and agility....
Categories: #compliance, #Risk Management

How Compliance Fatigue Undermines Security
Compliance fatigue is real—and it’s putting your security at risk.When checklists replace critical thinking, organizations become vulnerable. Learn how to move beyond box-ticking and build a security culture that stays...
Categories: #automation, #compliance, #Cyber Security
Moving Beyond Static Risk Management Frameworks to Continuous Control Monitoring
In the Banking, Financial Services, and Insurance (BFSI) sector, many organizations still rely on traditional risk management frameworks like the Three Lines of Defense (3LOD). These models worked well in...
Categories: #risk, #Risk Management
Compliance as a Continuous Cycle: Maintaining PCI-DSS, HIPAA, & More
Compliance isn't just about meeting regulatory requirements; it's about safeguarding your organization from risks that can cost millions. Yet, many companies still approach compliance as a one-time project, leaving them...
Categories: #automation, #compliance
From EDR to XDR: Evaluating Tool Efficacy in Risk Assessments
Cyber threats are faster, stealthier, and more coordinated than ever — and your tools need to keep up. This article dives into the real difference between EDR and XDR, how...
Categories: #Cyber Security, #Risk Management
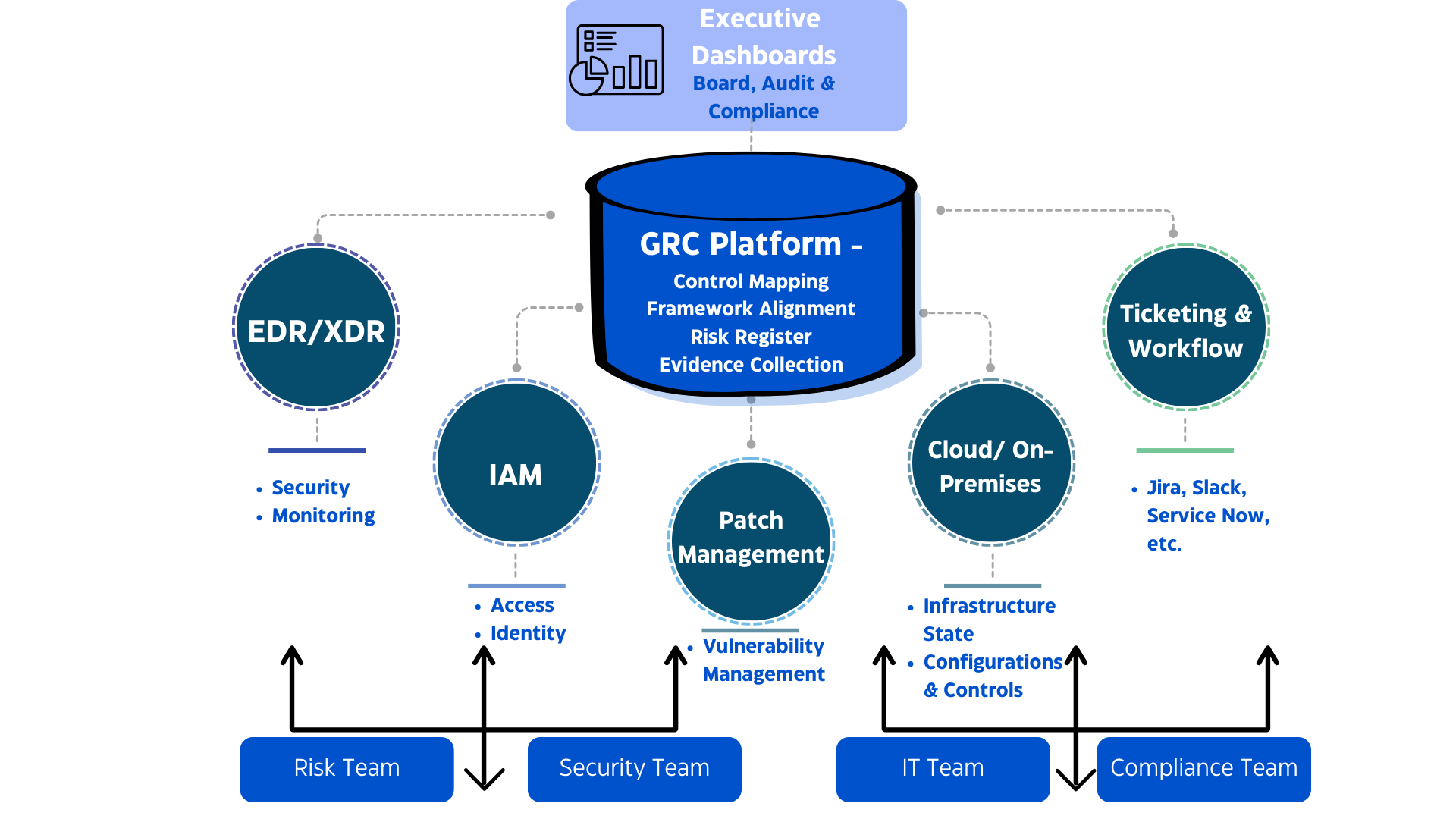
The Tech Stack for Ongoing Compliance: Integrations that Matter
Your team ships code every day. But your audit still runs once a year. In between, things break. Evidence gets lost. Risk data lives in ten different places. Most companies...
Categories: #automation, #compliance
Building a Risk-Aware Culture: The Human Element in Security
Protection starts with people. And, if you have not recognized this yet, you are overlooking the human element in security. In fact, humans are the weakest link in security, not...
Categories: #risk, #Risk Management

Navigating Multiple Frameworks: ISO 27001, SOC 2, GDPR, and Beyond
Imagine trying to find your way through a maze where many paths look the same, but each has different rules. Organizations face this challenge when complying with multiple security and...
Categories: #compliance

Quantifying Cyber Threats: Advanced Techniques for Risk Identification
This article explores the best ways to identify and manage cyber risks. By using techniques like scenario modeling, machine learning analytics, and threat correlation, companies can turn cybersecurity into a...
Categories: #Risk Management, #Vulnerability Management
The ROI of Real-Time Compliance: Cost Savings and Risk Reduction
Ignoring compliance is not just a legal risk. It is a financial mistake. But there is a better way. Let’s dive into it! Many companies see compliance as a burden....
Categories: #compliance

Conducting a Holistic Risk Audit: Key Steps & Best Practices
Most organizations approach risk audits the way they approach an annual health check-up—routine, compliance-driven, and often surface-level. If nothing appears broken, it’s business as usual. But just as hidden health...
Categories: #risk, #Risk Management
Continuous Compliance Demystified: From Checklists to Real-Time Insights
Did you know that nearly 67% of businesses reported an increase in data privacy violations in 2024 compared to the previous year?. That's a clear sign that traditional compliance methods...
Categories: #automation, #compliance

Measuring Organizational Risk Maturity: An In-Depth Framework Overview
Cyber threats aren’t slowing down. Every day, security teams are fighting fires, trying to keep up with evolving risks, compliance demands, and resource constraints. But here’s the question: Do you...
Categories: #risk, #Risk Management

Top 10 Vulnerability Management Metrics you need to be tracking
Every CISO and cybersecurity leader faces the same challenge. You invest in advanced vulnerability management (VM) tools, run regular scans, and patch the critical vulnerabilities your system detects. On paper,...
Categories: #Vulnerability Management

SEBI CSCRF: The Ultimate Guide for SEBI-Regulated Entities
Cyber threats are rising, and SEBI’s Cybersecurity and Cyber Resilience Framework (CSCRF) sets strict mandates to protect financial entities. With a March 31, 2025 deadline, firms must act now to...
Categories: #CSCRF

GRC Silos Cost More Than You Think – Here’s Why
Governance, Risk, and Compliance (GRC) functions often operate in silos, leading to inefficiencies, higher costs, and increased regulatory risks. Disjointed processes create blind spots, delay incident response, and make compliance...
Categories: #GRC

AI Compliance Frameworks: Why They Matter and What You Need to Know
With AI transforming industries at an unprecedented pace, the risks of bias, privacy violations, and regulatory non-compliance are skyrocketing. Global regulations like the EU AI Act, NIST AI RMF, ISO/IEC...
Categories: #compliance

ISO 27001:2022 Update – Are You Ready for the New Compliance Requirements?
The latest ISO 27001:2022 update brings critical changes to information security, risk management, and compliance requirements. With a stronger focus on cyber resilience, supply chain security, and evolving threats, organizations...
Categories: #ISO 27001
